Roundup of Apple's Latest Security Updates
Last week, Apple released iOS 10.3.3 and security updates to the desktop operating systems, Sierra, El Capitan, and Yosemite. Anytime there’s a security update, there are plenty of good reasons to install it right away, but this time around, we think the issues are serious enough to warrant a blog post and a break down. We’re encouraging friends and family to update immediately and we encourage you to do that, too.
Below is a breakdown of the critical issues in Apple’s recent batch of updates.
WiFi
Easily the scariest issue in this batch relates to the “Broadpwn” WiFi vulnerability that affects both Macs and iOS devices. Full disclosure on how to exploit this vulnerability is due to come this week and will allow an attacker in proximity to a victim to take over their WiFi card and install custom software on it.
This is concerning, in part, because you can’t just delete the bad software off your hard drive. Even worse, there’s no easy way to fix a compromised WiFi chip or to even know it’s hacked. It’s like a secret foothold into your computer.
Note: this issue also impacts some Android devices with Broadcom chips.
Note 2: if you’ve wiped your old Mac and installed Linux on it, you’re in trouble, because there doesn’t seem to be a way to upgrade the WiFi firmware except in Bootcamp or Mac. Note to self: leave a small Mac partition in the future.
iCloud Keychain Sync
To enable iCloud Keychain Sync to share stored passwords and credit cards across devices, there’s bad news. Researchers were able to register a fake device and then gain access to all of those secrets in plain text. Frankly, it’s just better to turn that feature off.
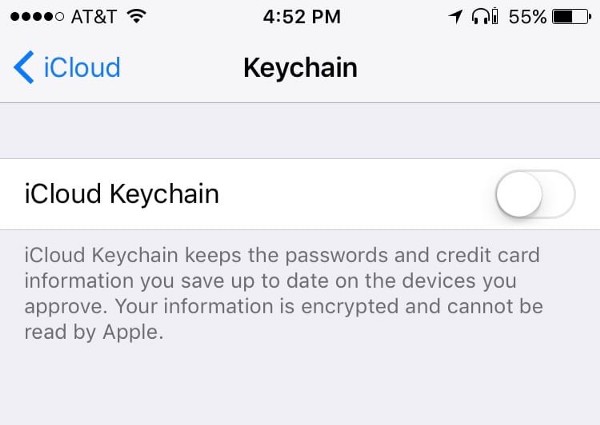 Although it’s convenient, turning this on is risky
Although it’s convenient, turning this on is risky
Instructions:
- On iOS: Open Settings, click on your name at the top, then on iCloud and scroll down to Keychain. If it says “On,” click in and turn it off. Keep data on your device when prompted.
- On macOS: Go to the Apple menu in the top left-hand corner, click on System Preferences, click into iCloud, scroll down and make sure Keychain is unchecked.
Bluetooth
For Mac, there are three issues that lead to arbitrary code execution with system or kernel privileges. According to the related vulnerabilities in the National Vulnerability Database, these can be exploited by someone with proximity to your computer and without any authentication. The complexity scores are low (meaning easy to execute), and the impact scores are high (meaning total system compromise). The saving grace here is that user interaction is required, which means you would likely get a warning of an attack via an unexpected message or pop-up.
USB
Almost all of Apple’s product line including tvOS, watchOS, iOS, and macOS are subject to an issue where a malicious USB device could take control of the computer. This is something that most security professionals just assume — any device you plug into your computer gets a level of trust you don’t want to give to an attacker. Consequently, you should never plug in USB devices you didn’t purchase yourself, never take USB swag at conferences, and ignore any USB devices you get randomly in the mail. Depending on your level of paranoia and the physical security of your computer, you may want to check out USB port blockers on Amazon.
Audio/Video
There are five vulnerabilities that involve malicious audio or video files on macOS and iOS.
It’s unclear whether or not surfing to a web page that causes malicious audio or video to play could trigger these vulnerabilities, so it’s best to assume that is the case. To disable autoplay of audio and video, take a look at this article with instructions for Safari and links to plugins for other browsers (note: read through the updates section before doing anything). For Safari, the Terminal commands you want are:
defaults write com.apple.Safari WebKitMediaPlaybackAllowsInline -bool false
defaults write com.apple.SafariTechnologyPreview WebKitMediaPlaybackAllowsInline -bool false
defaults write com.apple.Safari com.apple.Safari.ContentPageGroupIdentifier.WebKit2AllowsInlineMediaPlayback -bool false
defaults write com.apple.SafariTechnologyPreview com.apple.Safari.ContentPageGroupIdentifier.WebKit2AllowsInlineMediaPlayback -bool false
iOS WiFi Calling
The National Vulnerability Database reserved the disclosure number for this one, but there currently isn’t any information that we could find, and there’s no attribution for who found the issue on Apple’s list of fixed security issues. However, both iPhones and iPads with both WiFi and Cellular are impacted, and this comes under the heading of “Telephony,” so we expect that the issue is specific to the WiFi calling feature.
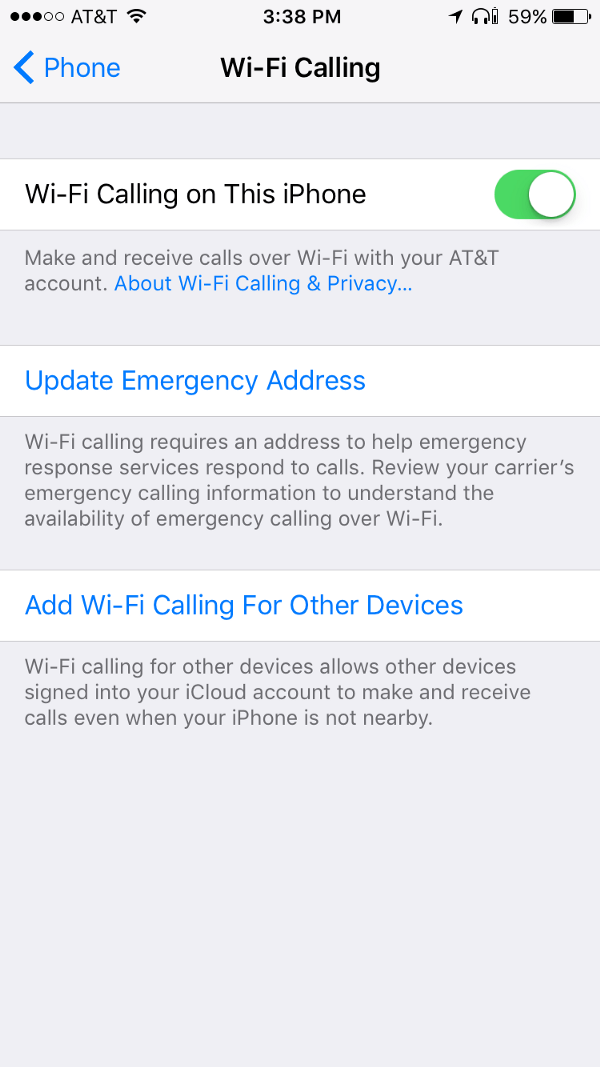 WiFi calling is great when coverage is poor, but it also opens up possible attacks when you’re on an untrusted network, such as in a coffee shop.
WiFi calling is great when coverage is poor, but it also opens up possible attacks when you’re on an untrusted network, such as in a coffee shop.
Apple has this to say about the vulnerability:
An attacker in a privileged network position may be able to execute arbitrary code.
We expect this means that an attacker on a local WiFi network can mess with the call data in such a way that an iOS device connected to the network can be compromised.
At this time, we don’t see an issue with leaving WiFi calling on if you install the update.
Browser
An astounding 25 Safari-related vulnerabilities were fixed on macOS, and another 26 (many overlapping) were fixed on iOS. The worst of these lead to arbitrary code execution if a user navigates to a malicious website or a trusted site that was hacked or is hosting malicious ads. Use those ad blockers and update Safari now.
Graphics
Apple’s graphics power management and Intel’s graphics card driver have a combined total of 7 Mac vulnerabilities. No more details are available.
Kernel
By our count, there are ten fixed vulnerabilities in the macOS kernel and 9 in the iOS kernel (some of these overlap), most of which lead to arbitrary code execution and some of which leak information. There are almost zero details on specifics for these or whether or not the issues could be triggered remotely, so updating is your best protection here at this time.
How to Update
On iOS: go to Settings -> General -> Software Update
On macOS: go to the Apple icon in the top left corner of your screen, then App Store, then click the Updates tab.
Conclusion: Go Update
It’s always a good idea to update your devices when security patches come out, but it’s also easy to put off. No one wants their phone or watch or laptop to be inaccessible indefinitely, but you can look at it as a great excuse to read an old fashioned magazine or book, hike, meditate, or talk to friends and family. Because this is important, the issues are serious, and we expect information on how to exploit some of these exploits to be released imminently.
And don’t forget your Apple TVs, too.
Original photo by Hannu Viitanen