The Worsening State of Application Security
At the Defcon conference last year, I was struck by the simplicity of most of the hacks that were being described. Five years ago, most of the talks I attended discussed high complexity attacks. This past year, it was the opposite. Instead of exploiting tricky buffer overflows requiring much debugging of assembly code, these talks were more about how apps didn’t verify their server’s identity when using SSL or stored passwords in plain text in the firmware of internet connected devices.
This made me wonder: is Defcon losing its edge? Or are applications getting less secure? Or am I just biased by an unrepresentative sampling of talks?
Vulnerability Data Trends
To test this, we looked at data from the National Vulnerability Database (NVD). NVD rates the severity of application vulnerabilities according to how easy the flaw is to exploit and how serious the damage if it is exploited. They also rate the complexity of an attack that exploits the flaw.
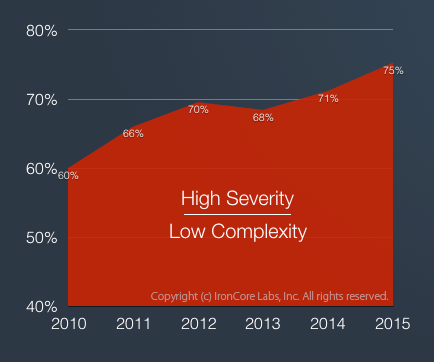
Percent of high severity vulnerabilities that were ranked low complexity in the National Vulnerability Database.
We looked at the percentage of high severity vulnerabilities (those scoring between 7 and 10) that were easily exploited (complexity score was “low”).
In 2010, an unfortunate 60% of high severity vulnerabilities were low complexity.
In 2015, the percentage of low complexity, high severity vulnerabilities increased to a staggering 75%.
For reference, the number of high severity vulnerabilities of all complexities in 2010 was 2,094 and in 2015 was 2,409, a 15% growth rate, while the low complexity high severity vulnerabilities went from 1,813 in 2010 to 1,264 in 2015, an increase of 43%.
Conclusion: it isn’t Defcon; the software industry is producing less secure software. It’s easier to exploit applications today than five years ago.
Contributing Factors
So why is software security getting worse rather than better? We can hypothesize that startup culture of just getting anything out the door and taking shortcuts; the onslaught of new programming languages, libraries and backends; or the rapid evolution of connected devices from phones to thermostats play a role. These hypotheses, however reasonable sounding, are hard to prove.
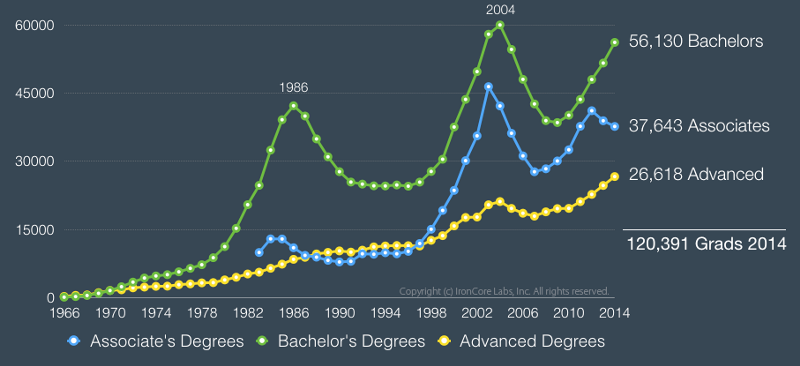 U.S. Computer Science degrees over time according to the National Science Foundation WebCASPAR Database.
U.S. Computer Science degrees over time according to the National Science Foundation WebCASPAR Database.
That said, one fact really jumps out: in 2014, 56,130 bachelors degrees in computer science were awarded in the U.S., but of the top 10 computer science schools including Carnegie Mellon, MIT, and Stanford, none required secure coding to graduate. According to a CloudPassage study, of the top 50 Universities, only three require any kind of cyber-security course.
If we don’t teach computer science students how to write secure code, how can we expect applications to be written in a secure way? How can we turn the tide towards more secure applications?
The Unsurprising Result: Crappy App Security
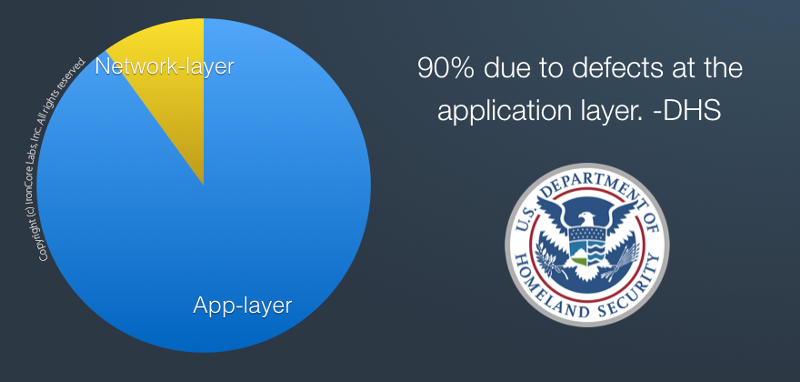 Security incident causes according to DHS.
Security incident causes according to DHS.
With so little effort and training put into security, it’s hardly surprising that 90% of security incidents are the result of application defects according to the Department of Homeland Security.
Perhaps less surprising, but certainly more depressing, are the findings of the HP Enterprise 2016 Cyber Risk Report that show that 86% of web applications had serious issues with authentication, access control and confidentiality, up 14 points from the previous year.
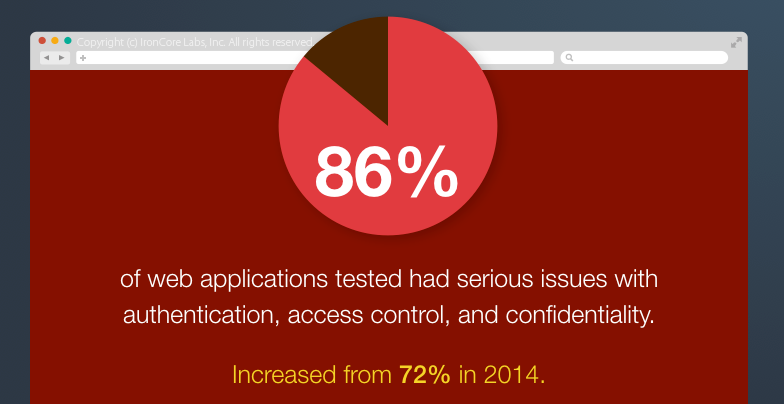 Source: HPE 2016 Cyber Risk Report
Source: HPE 2016 Cyber Risk Report
WhiteHat Security’s 2015 report took those results one step farther and tracked how long it takes companies to fix serious vulnerabilities once they were alerted to them. On average, retail companies took 227 days to fix reported vulnerabilities. Even IT took an average of 132 days.
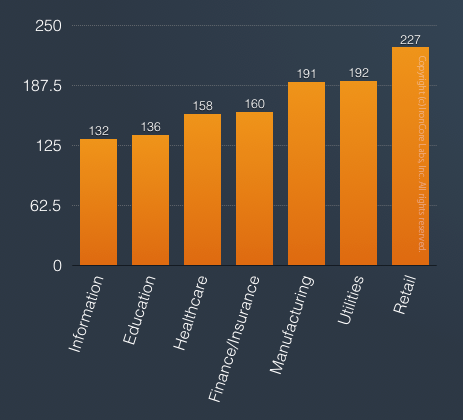
White Hat Security Stats Report on average number of days to fix reported vulnerabilities by industry. Only the worst industries are shown here.
WhiteHat also tracked the percent of their customers who had at least one serious, exploitable and known vulnerability in their web app for more than 151 days out of calendar year 2015. Well over half of companies across industries fit in this category.
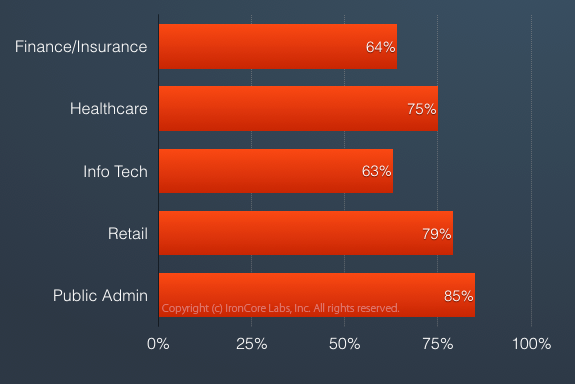
Percent of companies with a serious vulnerability for more than 151 days in 2015 according to WhiteHat.
Where Do We Go From Here?
These stats should be a wake-up call to software developers and to software companies in general. Applications are the problem. However hardened a server and however tightly controlled a network, if the application can access the data and the application is vulnerable, then the data is vulnerable. Applications are inevitably vulnerable.
But applications need not be easy to hack. With better training and more attention to security in the software development lifecycle starting with design through testing and into the maintenance phase, we can make hacking hard again.
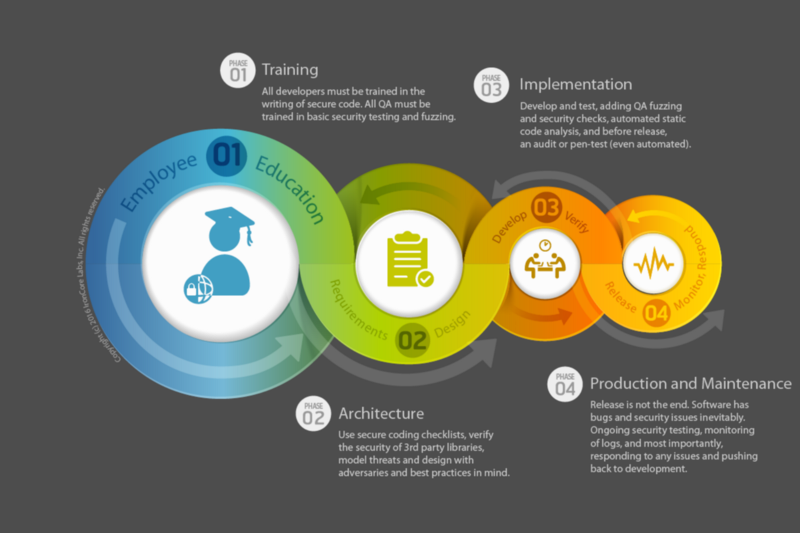 Add security to every step of a software lifecycle starting with employee education before design, coding or testing even beings. Then remember to never stop reviewing an application for security issues until end-of-life.
Add security to every step of a software lifecycle starting with employee education before design, coding or testing even beings. Then remember to never stop reviewing an application for security issues until end-of-life.
For applications or portions of applications that handle sensitive data, the risk of a vulnerability leading to high volume data theft can be greatly reduced. Data today can be secured such that even a compromised application can’t access it (in the clear at least) unless requested by an authorized user. Few users should have access to large amounts of sensitive data.
There’s no excuse today to miss high severity / low complexity vulnerabilities in the application development process. The industry needs to own up to the problem and stop waiting for magic laser weapons to stop attacks before they hit their app. Even the smallest software startup needs to review security at every step of their process and in every role that touches the product up through the CEO and to the board.
Spread the word and stop the madness.

