Thales CipherTrust Manager Integration
The fastest route to data sovereignty for customers of IronCore Labs and Thales

Discover the peace of mind of data sovereignty
Data privacy laws like GDPR only allow the transfer of personal data to third countries with adequate privacy protections, which rules out the United States and China, among others. That puts SaaS companies in a tough position when customers are increasingly demanding data control.
Technical measures for data sovereignty
One of the key methods to achieving data sovereignty is through encryption and regional key management, where sensitive data is encrypted by the SaaS application and encryption keys are given to the customers for them to hold in the geographic region that is sovereign over the data.
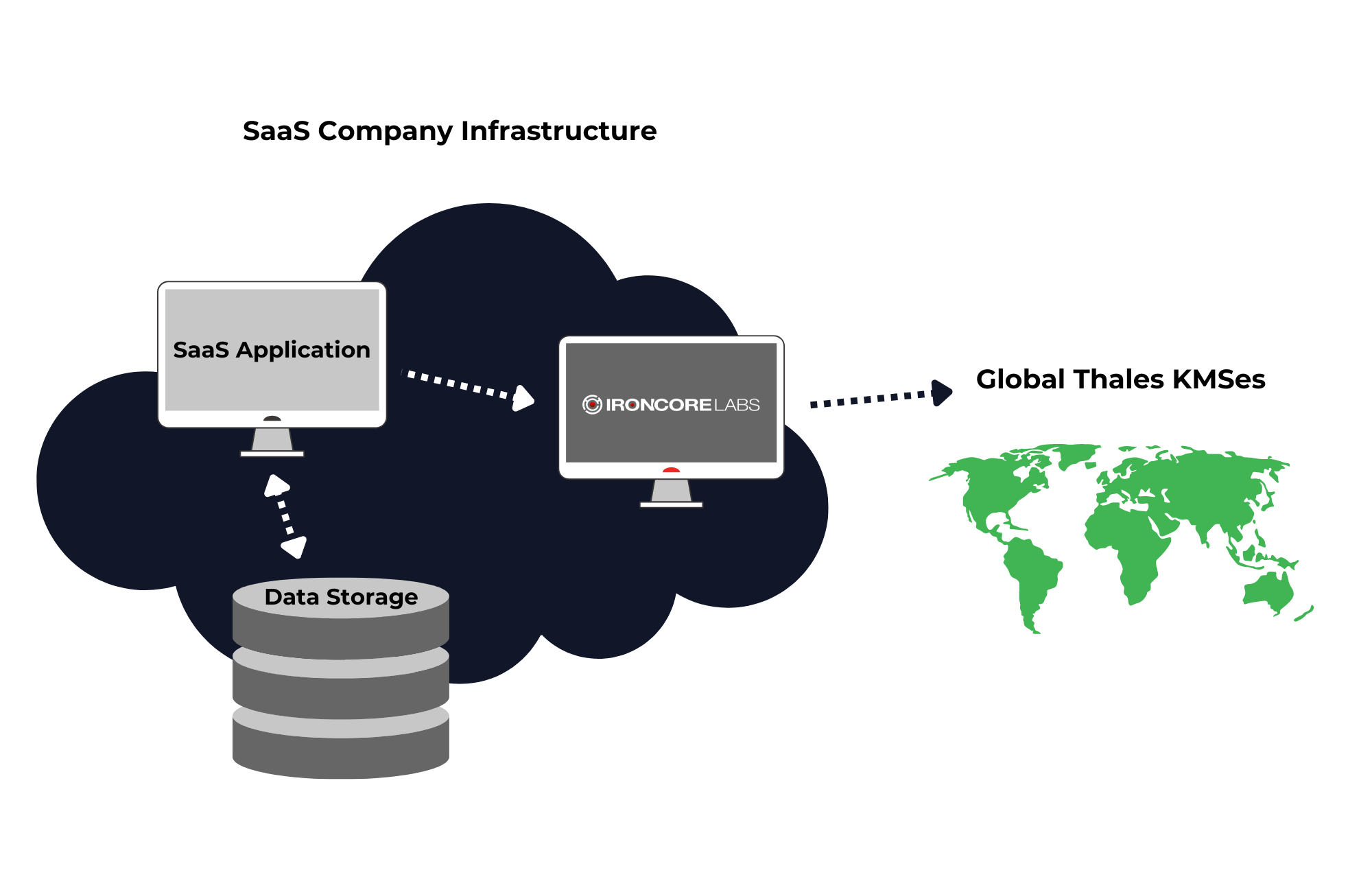
IronCore Labs + Thales = Data sovereignty
The IronCore Labs SaaS Shield platform and the Thales CipherTrust Manager combine the power of usable, performant encryption and BYOK with global key management. Encrypt your customers’ sensitive data at the application layer, before it goes to the data store, and place the keys under the jurisdiction of the appropriate country.
For B2B SaaS companies, customers can even hold their own keys or leverage a partner that offers the Thales CipherTrust Manager as a service.
Getting started: The data sovereignty guide
The simple way to determine where to start and where to find the resources you need.
Are you the data holder or the key holder?
Data holder: get started
Data holders are typically SaaS companies that hold sensitive customer data in their application.
Step 1: Find your entry point
IronCore Labs
Data holders start by protecting sensitive data with advanced, usable encryption with SaaS Shield.
Step 2: Take action
Prioritize data sovereignty
At IronCore Labs, we make sure you get the benefits of encryption without the years of cryptography experience or expense of building application-layer encryption (ALE) or bring your own keys (BYOK) from scratch. Performance and usability are our bread and butter.
Read more about SaaS Shield and download the integration data sheet to help explain the importance of application-layer encryption and data sovereignty to your teams.
Step 3: Talk with an encryption expert
We’re here to help your rollout of data sovereignty go as smoothly as possible. Let’s talk!
Key holder: get started
Key holders are typically companies with SaaS vendors that hold your sensitive data in the cloud.
Step 1: Find your entry point
Thales CipherTrust Manager
Key holders start by using the Thales CipherTrust Manager to hold the encryption keys to their data held by SaaS vendors.
Step 2: Take action
Email your SaaS vendors
You likely have several SaaS vendors that don’t yet offer encryption or BYOK solutions, which are required to address your data sovereignty concerns. You can be a powerful force for change by reaching out to your Saas vendors and telling them this is a priority.
View our email template and checklists you can use to reach out to your SaaS vendors and help them connect with IronCore Labs.
Step 3: Refer us to your SaaS vendors
We will get your SaaS vendors to offer you the advanced protection and data sovereignty you need.
Did you know you can also search on encrypted data?
Read more about Cloaked Search and how encryption works for you.