Introducing IronSFTP
Almost all modern servers have SSH. Now any of those servers can be used to store encrypted files hassle-free. ironsftp is a drop-in alternative for command-line sftp that works almost identically, with one important difference: files stay secure after they’re uploaded, regardless of the SSH server.
Intellectual property, customer data, backups and other files are often copied between machines and left there unencrypted. This is a dangerous practice because it assumes that the servers are hacker-proof and that the network firewall will keep the bad guys out. If an intruder or a malicious insider has access to the server, then she could have access to sensitive files on the server. That’s a bad idea.
ironsftp transparently encrypts all files it uploads and decrypts all files it downloads that the user is able to unlock. ironsftp manages keys automatically and makes sharing with other ironsftp users easy. This is a tool for power users comfortable with the command line. It functions almost exactly like sftp except that files stay encrypted after upload.
[Storing files unencrypted] assumes that the servers are hacker-proof and that the network firewall will keep the bad guys out.
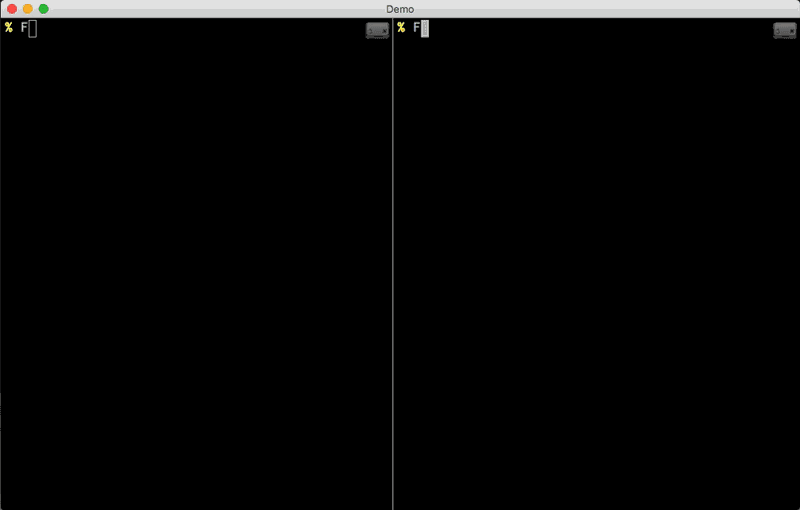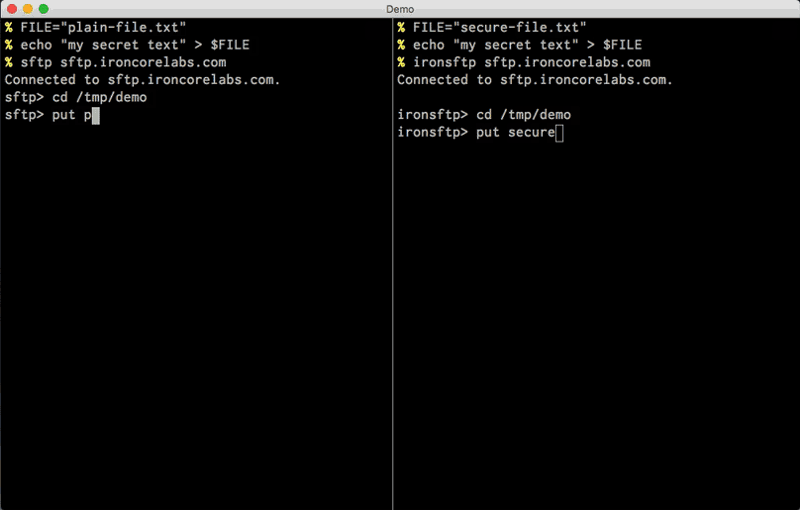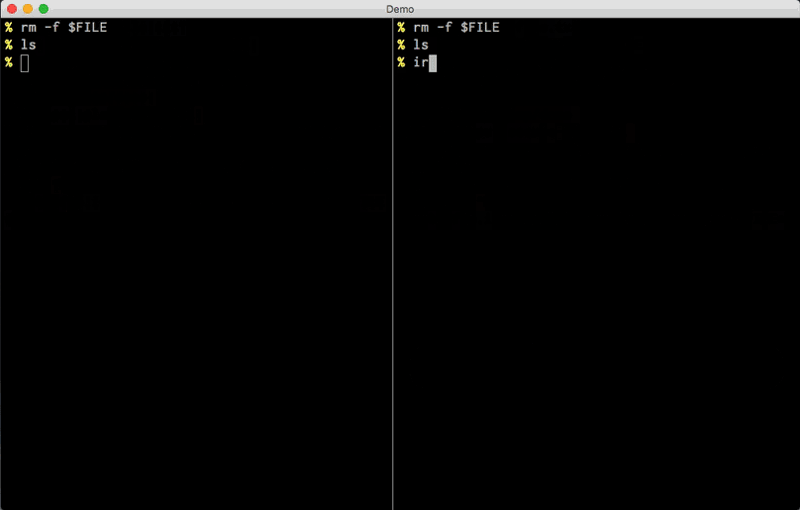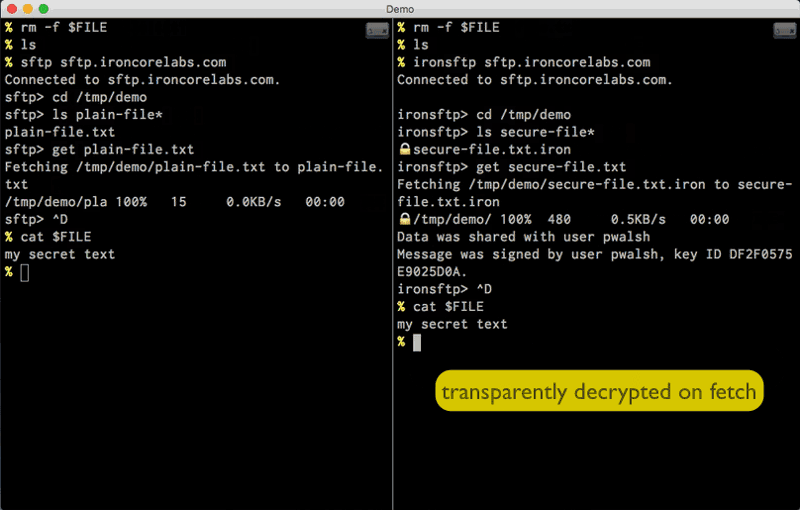 sftp vs. ironsftp example
sftp vs. ironsftp example
GPG Compatibility, Open Source and Free
The encrypted files are GPG 2.1.7+ compatible as are the generated encryption keys. This means that files can be decrypted without ironssh, because IronCore adheres to widely used standards instead of proprietary formats. In addition, the code behind ironssh is a fork of OpenSSH* and all new code is BSD licensed and available on Github. These enhancements will be free forever.
Crypto Geek Summary
Ironssh uses libsodium and Curve25519 for public key encryption of a file’s symmetric key and AES256-CFB for the file contents. GPG does not support ChaCha/Poly1305. The local encryption key is secured by the user’s SSH RSA key. When a user unlocks her local RSA key, that key is used to unlock (or to protect on initial create) her GPG-compatible encryption keys. This means after unlocking one key, the encryption and decryption capabilities are also unlocked.
Supported Operating Systems
For now, ironssh requires OpenSSL 1.0.2+ for its improved encryption and modern features. If there’s demand, these features could be backported to bring ironssh to older operating systems, although security conscious users should be using up-to-date machines.
Here’s a list of supported operating systems at initial release:
- CentOS 7
- Red Hat Enterprise 7
- Fedora 23, 24
- Debian Stretch
- Ubuntu Wily, Xenial, Yakkety
- MacOS will be available via homebrew shortly
- Other OSes supported via manual source code compilation
Installation details can be found on our website.
What’s Next?
This is an initial release and should be considered beta. Please submit suggestions and pull requests to help make it better. ironscp support will be added shortly so that those who prefer using scp can get the transparent end-to-end encryption features of ironsftp without the interactive session. The issues list on Github has a more complete roadmap for the ironssh project.
IronCore Labs has more products coming down the pipe, including enterprise tools for managing encryption keys and encryption policies. These tools will tie back to the ironssh tools to give enterprises better control over their encrypted files without sharing any private keys.
Links
* The OpenSSH project link is http://www.openssh.com. We chose not to inline the link since they don’t have an https version of their website.