Inside the CIA's "Vault7" Cyber Treasure Chest
Wikileaks is publishing the CIA’s catalog of cyber weapons for the world to see. Or more specifically, they’re publishing a cache of documents that talk about these exploits.
Some 8,761 documents have been made public so far, and more are promised. Wikileaks has redacted any actual exploit code (for now), which leaves us with documentation and project notes, but not implementation details. However, Wikileaks claims that the full set of unredacted documents are making their way around some hacker circles. They also claim that this is the first release in a series.
The documents appear to be from an internal CIA wiki with commenting turned on. It is likely from a Confluence instance.
Below are some gems from inside the stash.
Posting Passwords For The Win
This page contains passwords for laptops:
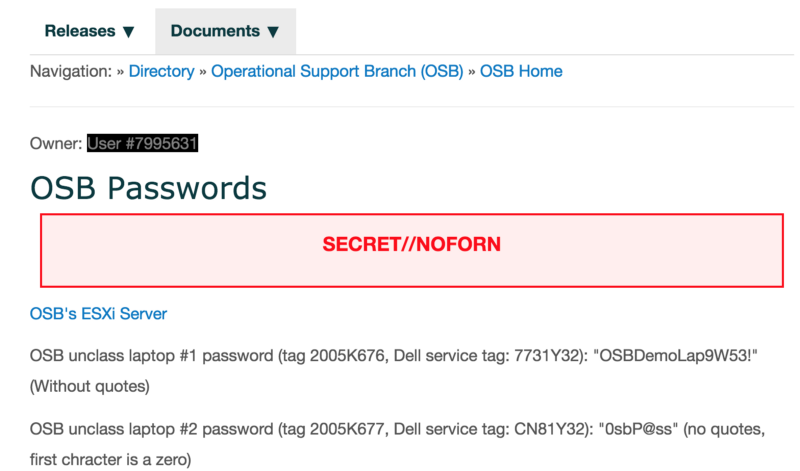 Someone posted laptop passwords to a wiki. In the CIA. #securityfail
Someone posted laptop passwords to a wiki. In the CIA. #securityfail
Further down, other CIA employees commented on the page. One said it was no big deal since only the Operational Support Branch (OSB) could view it. (Well, the OSB and now the whole world.) Another commenter wondered if the security team would have a heart attack to see passwords posted:
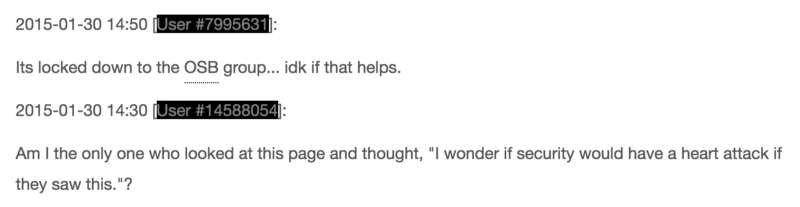 Part of the debate by CIA employees about whether posting passwords to a wiki is a good idea
Part of the debate by CIA employees about whether posting passwords to a wiki is a good idea
Allow me to chime in here: yes, the security people would flip out if they saw this. Primarily because you work for the CIA and aren’t sure if posting passwords to wikis is a bad idea.
Random Sampling of Tools
Here are some tools of interest, either because they have great names or interesting uses:
- ShoulderSurfer — extract data from an Exchange Database without the need for credentials
- Fight Club — Wrapper for trojaning common programs and delivering a payload to duped users.
- Weeping Angel — Turns a “smart” TV into a persistent eavesdropping device.
- Comodo Gaping Hole of DOOM — Comodo fixed a usability problem in v5 by allowing any SYSTEM level code to run in v6, making a formerly hard to circumvent security tool trivial to get around.
- Philosoraptor — A dropper for getting malware onto a computer.
- Time Stomper — Tool to change file access and modification times.
- RoidRage — Android implant
- McNugget — Command and control server for Macs.
- Adderall — A tool to flash an iOS device to make it receptive to exploits.
- DRBOOM — Persistent iOS malware that requires a physical connection to install.
- SparrowHawk — BSD keystroke logger that also works on other Unix-like platforms excluding Linux.
Tips and Tricks from the CIA
It turns out that some of the tips for writing exploits are also really good tips for writing any secure software. For example:
(S//NF) DO explicitly remove sensitive data (encryption keys, raw collection data, shellcode, uploaded modules, etc) from memory as soon as the data is no longer needed in plain-text form.
DO NOT RELY ON THE OPERATING SYSTEM TO DO THIS UPON TERMINATION OF EXECUTION.
Other tips are best ignored. For example, on the tips and tricks for git page, one developer suggests turning off https verification:
# Issue: When attempting to clone (or any other command that interacts with the remote server) git by default validates
# the presented SSL certificate by the server. Our server’s certificate is not valid and therefore git exits out with an error.
# Resolution(Linux): For a one time fix, you can use the env command to create an environment variable of GIT_SSL_NO_VERIFY=TRUE.
$ env GIT_SSL_NO_VERIFY=TRUE git
# If you don’t want to do this all the time, you can change your git configuration:
$ git config — global http.sslVerify false
Virus removal?
The CIA apparently sometimes buys software as “Affinity Computer Technology,” according to this list of Sublime Text licenses. That seems to refer to a computer repair shop in Virginia. Their website says that, among other things, they provide computer virus removal. Whether it’s a CIA front or a legitimate business, the irony here is thick.
Conclusions
That the CIA has teams of folks building and using exploits is unsurprising. In fact, that’s their job. To me, the big surprises were the many documents that seemed borderline unprofessional and certainly unsophisticated. To be sure, some of the referenced tools do very sophisticated things, which suggests a mix of skill levels and maturity levels that you would likely find in almost any organization.
All of these tools have to be considered burned now even without released code. That is a potentially big blow to American cyber spying and offensive strategies. In my random digging through documents, I found nothing of real public interest. Sure, it’s fascinating to get a glimpse of what they can do and how they do it, but at the end of the day, this data dump holds little value for Americans, but a lot of value for America’s adversaries.
Photo credit Sinisa Botas via 123rf




