Military Grade Encryption
Everywhere I look, companies say they protect data using “military-grade encryption.”
Wow! That sounds fantastic! Sign me up! If it’s good enough for the military, then it’s good enough for me!
Or that’s what they hope you think. Alas, this claim is more often the mark of poor security than of good protection.
So what exactly is “military-grade encryption”? That’s not a simple question since the military has different requirements for different sensitivities and these go well beyond the encryption algorithm used.
That said, the encryption algorithms considered to be usable by the military are in the NSA Suite B Cryptography list (soon to be replaced). One specific algorithm, AES, is on the list and widely used. In 99% of cases, this algorithm is what people mean when they claim they use “military-grade encryption.”
So what’s wrong with this claim? Is AES bad?
AES is fine (arguably, there are better options, but nevermind). AES is like a camouflage jacket. You can’t just put it on and call yourself military ready.
Using a strong encryption algorithm does not, by itself, mean data is safe. For example, the text you’re reading right now was encrypted on its way to you using AES. It’s a part of the secure connection you get because of the “https” in the URL. So this text you’re reading is protected by “military-grade cryptography.” And yet, anyone can view it. You didn’t have to authenticate, or have a key, or know a secret to see it.
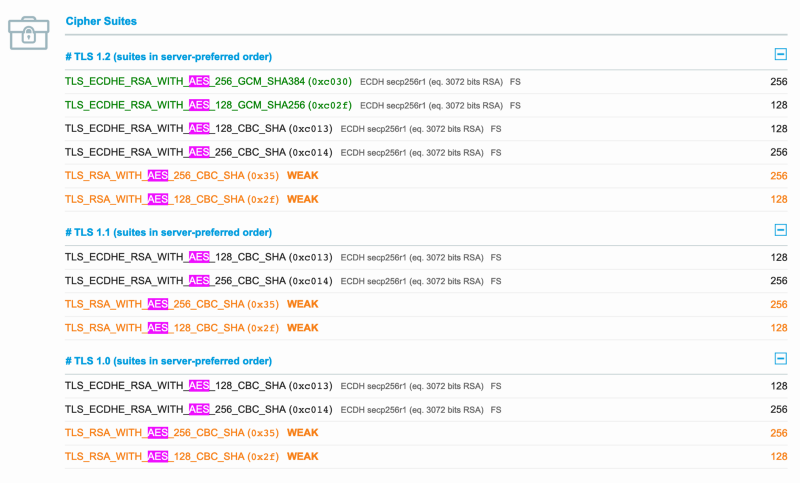 TLS cipher suites used by this blog; all utilize AES
TLS cipher suites used by this blog; all utilize AES
The protection you get from HTTPS keeps a passive network watcher from seeing what you’re reading and an active network intermediary from changing the contents of the data as it makes its way to you. HTTPS is essential for security, but it isn’t data protection. It’s connection protection.
What the “military-grade encryption” claim doesn’t tell you is:
- What access controls, if any, are in place to protect the data, nor where or how they can be bypassed (for example, by a database administrator).
- Whether the encryption is transparent or opaque: in many cases, transparent encryption is transparent to attackers, too.
- With AES, the decryption key is shared among all parties that need access. Which begs the questions: who can see the key(s)? Who has ever had access? How are the key(s) protected?
- With AES, there are quite a few modes with various tradeoffs. What mode (GCM, CBC, CTR, etc.) is being used and is it appropriate?
- Are keys rotated? Are initialization vectors (IVs) used correctly? What about the random number generation source? If it isn’t truly random, the encryption may be compromised.

Imagine a door to a vault. This thing can withstand sledgehammers and crowbars all day long. But it has a code panel on the front of it. Written above that is the entrance code (people can be so forgetful, you know). Does it matter how strong this door is? No.
Hackers attack systems, not algorithms, and there are many parts to these systems and many choices beyond the algorithm.
“At rest and in transit”
While we’re at it, there’s one more data protection claim that sounds good and gets used and abused all over the place. And most of the time, it’s basically meaningless. The claim looks something like this:
We protect your data with AES-256… Military grade encryption… at rest and in transit
So what does this mean? “In transit” almost certainly means HTTPS. Remember how earlier I said that the data you’re reading here was encrypted using AES? That’s what they’re saying here. They’re saying they use HTTPS. Don’t get me wrong, that’s great, but it doesn’t limit who can access the data.
The other part of this is the “at rest” bit. That sounds promising. So if a hacker gets into a server, they’ll find only encrypted data and be unable to access it, right?
Probably not.
Unfortunately, what this almost certainly means is that they use transparent disk encryption. That’s a technology that, like HTTPS, is super important to use and should be used by everyone. But it’s nothing to brag about.
With transparent disk encryption, if the machine is running, it’s as if there’s no encryption at all (hence “transparent”). When the computer is off, the hard drive data is meaningless random garbage.
So what’s the point? Two things:
- Anyone stealing a hard drive out of a computer will get a nice hard drive, but none of the data on it.
- If a hard drive fails for some reason, it no longer needs to be resuscitated to wipe the data or else physically destroyed before throwing it away.
Just as with “military-grade encryption,” what you have here is people bragging about doing the basics — the minimum possible in this day and age — and making it sound like it is a layer of protection that would keep hackers or others from viewing your data.
Conclusion
You could dismiss these phrases as something generated by unsavvy marketing people but for one thing: security and cryptography companies are some of the worst offenders. In my mind, this is an intentional move to blow smoke in the face of customers.
[Note: we decided shaming companies here would be a distraction, but you can Google easily enough.]
Anyone who brags of encrypting “in transit and at rest” and/or using “military-grade encryption” is bragging that they lock their front door. Such a person probably doesn’t have a good lock, an alarm system, and it’s likely they have a key under the mat. Because who brags about doing basic things? If you see these claims, you should be worried about the security of the company making them. I am.