Infographic: The Customer Managed Keys Buyer's Guide
Updated September 2021
More and more companies are securing sensitive data with application-layer encryption (ALE) and customer managed keys (CMK). But both ALE and CMK are often confused and misunderstood within the security industry. Let’s look at what each one is and how CMK is being used.
What is Application-layer Encryption?
With application-layer encryption, data is encrypted before being stored, which prevents someone with direct access to a database from being able to browse the encrypted data. It also adds an important layer of security between an application and the data store, which can block or minimize damage from some application vulnerability attacks.
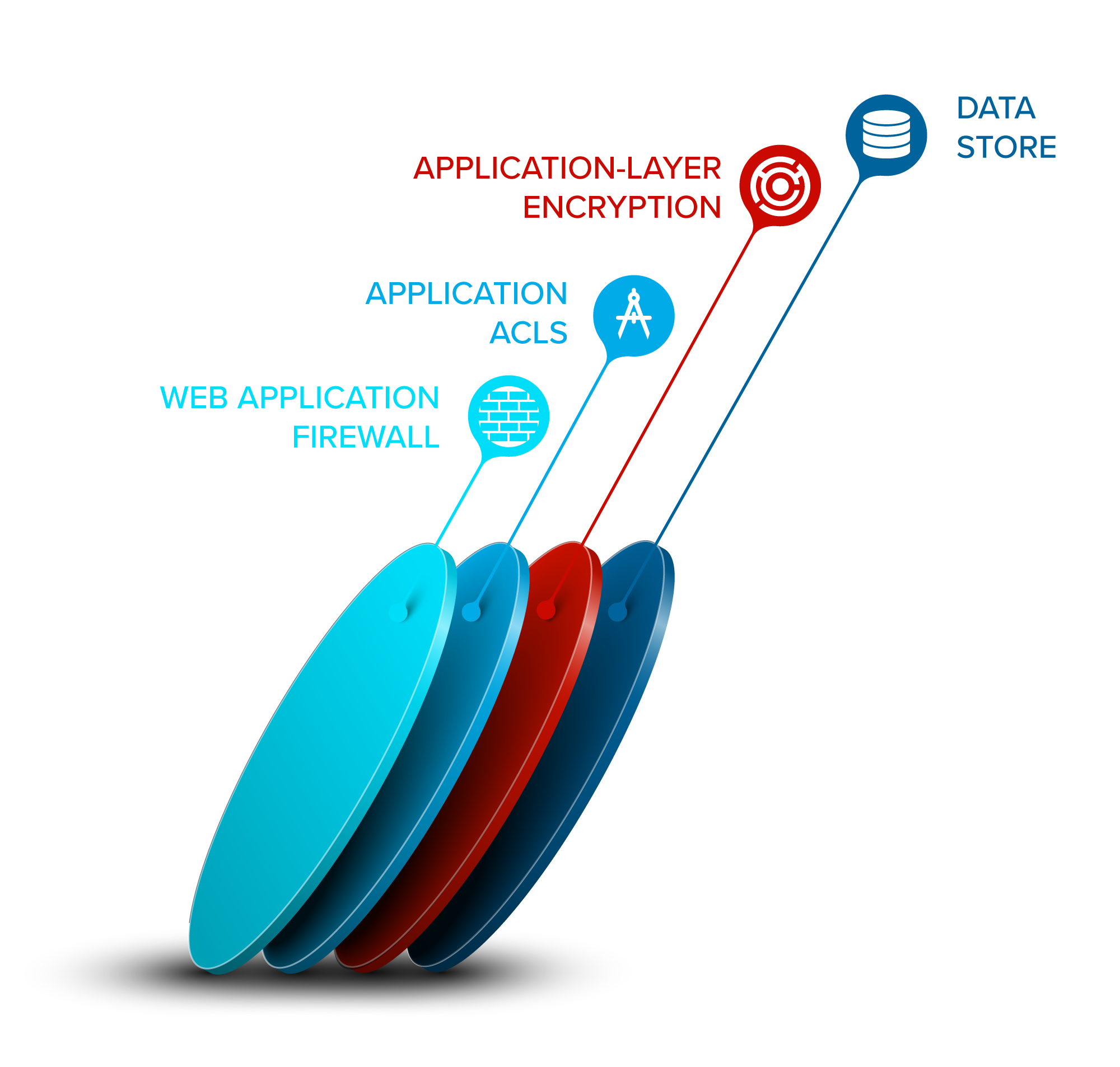
When CMK is used in combination with application-layer encryption, customers are able to manage their own keys, monitor how their data is used, and revoke access to sensitive data if required. You hold the master keys for your less sophisticated customers, while your more sophisticated Enterprise customers are able to retain control of their sensitive data by holding their own keys.
What is CMK?
Let’s start with a simple definition from our CMK overview page.
Customer Managed Keys, or CMK, is a cloud architecture that gives customers ownership of the encryption keys that protect some or all of their data stored in SaaS applications. Your customers can independently monitor usage of their data and revoke all access to it if desired.
Ownership of keys is one of the key points that differentiates CMK from other similar security architectures. If the customer doesn’t have full ownership of the keys and the SaaS vendor can see or access those keys in any way, that’s not what we call CMK.
Many variations of CMK exist within the industry. Here’s an infographic comparing some of these approaches.
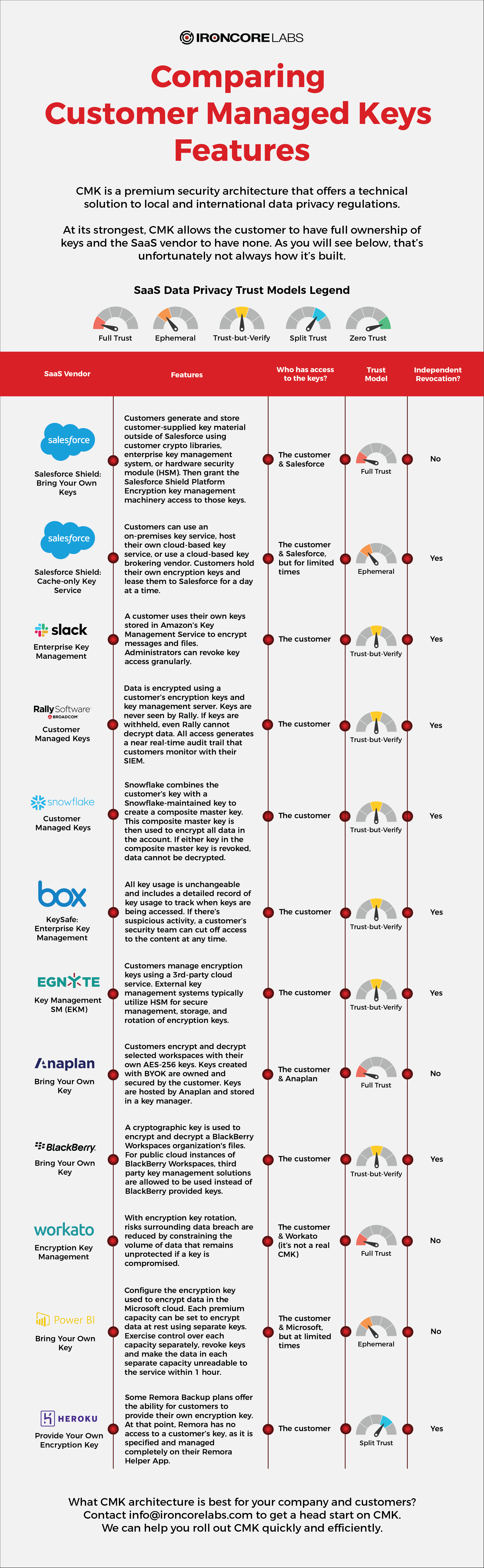
To learn more about the trust models mentioned above, read our trust models blog.
Things to Consider When Researching CMK
We’ve talked with a lot of Security Architects, CISOs, CTOs and CEOs about CMK, and here are some of the most common questions they ask.
1. What data privacy regulations do you or your customers need to comply with?
CMK meets the needs of most compliance regimes by giving full audit trails on data access. It can also help with tricky cases like holding EU data post-Schrems II.
Standard contractual clauses and updated privacy policies aren’t a sufficient basis to allow U.S. companies to hold the data of E.U. citizens. New privacy regulations and rulings mean that companies must use technical measures to protect data or else risk lawsuits and fines.
https://blog.ironcorelabs.com/you-dont-need-the-privacy-shield-to-hold-eu-data-775440a23e52
CMK architectures where your customers hold their own keys allows you to hand over data that’s encrypted if a Government so compels you. Many thorny regulatory requirements are eased using CMK with customer held keys.
2. How much effort is it to get started and what are the tradeoffs?
The most important thing to understand is that application-layer encryption and CMK are not an all-or-nothing approach. There’s a lot of flexibility with CMK to make it what you need it to be based on the requirements of your app. Usually, this means starting with a small subset of data, shipping the feature so your customers get the benefit of data control, and then adding more slices of data later as necessary.
But let’s be real. Encrypting data creates barriers to working with that data and sets up some tradeoffs. But these tradeoffs typically aren’t as big of a deal as many people fear. Here are the most common concerns we hear.
- Performance: Will this slow down our app? Usually not. There is some performance overhead, but if you architect it well, your users won’t notice any difference.
- Analytics: Can we still query on this data? It depends. If the data is in a standard SQL database, then you probably can’t query on the encrypted fields. But with CMK you can decrypt on the server, so you have the option of fetching and post-filtering or summing or whatever it is you need to do. There are also options for finding data such as using search.
- Search: Can I search on an encrypted field? Yes! We’ve launched a product called Cloaked Search that allows you to encrypt and search on encrypted data. You can learn more about it on the Cloaked Search product page.
- Scope: What do I need to encrypt? You likely need to encrypt things like social security numbers, names, and street addresses. You probably don’t need to encrypt things like preferences and purchase histories and state and country. Start with the most sensitive data and build from there.
3. What will this cost me?
Probably nothing. In most cases, CMK produces large returns in the form of new business, larger customers, and, if you choose to sell it for a premium, new revenue streams from existing customers.
If you add CMK, it’s critical that your product marketing, sales, and renewal teams are out touting it to your customers and prospects. It will make their jobs easier and their commission checks larger.
There are ways of getting started that require almost zero up-front costs and little time. And for bigger changes, it’s better to get a product on the roadmap when your team realizes CMK is a feature your customers will pay a premium for. We cover this more in a blog on Salesforce’s CMK product.
How much does Salesforce charge customers for premium data control like this? They charge 30% on top of the current contract. It’s an expensive feature, but your enterprise customers are willing to pay for premium privacy to protect their data (and their reputation/revenue).
For most data privacy or security features, SaaS vendors have to absorb the cost of implementation and any commercial tools as overhead. CMK is different. This is a premium privacy feature. And it pays for itself.
Let’s Do This Together
With extensive experience in data privacy, enterprise security, and cryptography, we’ve got a team ready to get you started with application-layer encryption and CMK today. Companies can spend years creating CMK from scratch, but we built the SaaS Shield CMK Kit and SaaS Shield CMK for Amazon S3 products to make life easier for you and better for your customers.
IronCore Labs' CMK solution is perfect to bring extra privacy and control to our customers. They've been a great partner to us.
Here’s what your security features could look like with IronCore, with us giving you the tools to create the premium layer of security.
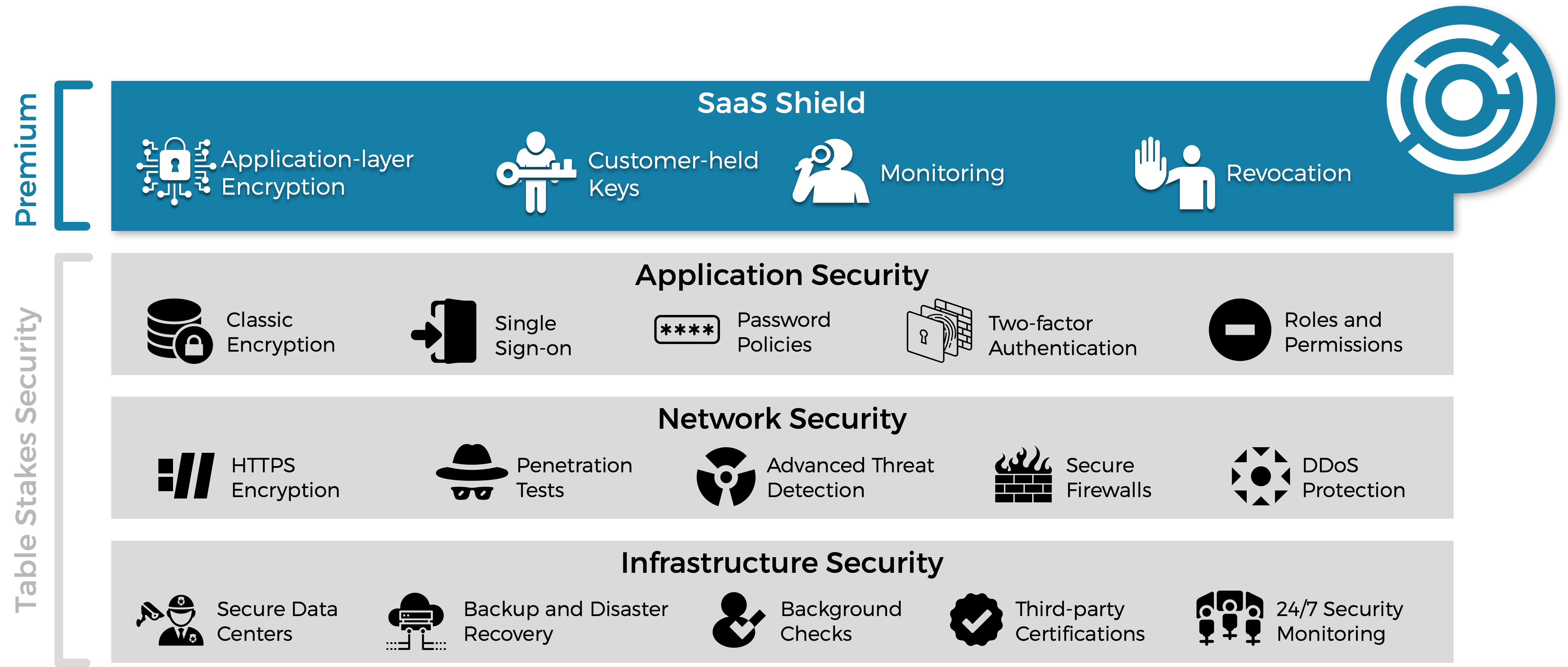
Ready to get started? Let’s talk.
We help you cut through the noise to focus on what’s relevant to you and your data privacy needs.




