SaaS Security: How To Handle Sensitive Data
Why SaaS Companies Should Offer Customer Managed Keys
It costs around two cents per gigabyte per month to store data in the cloud today[1]. But the cost of losing that data is around $150 per record [2], which means that you’re looking at a cost of $150,000 per gigabyte of customer data that’s compromised — more if your records are smaller than 1MB, which is likely.
For companies that store huge amounts of contact information, uploaded files, chat histories, and other personal data, a breach can be catastrophic.
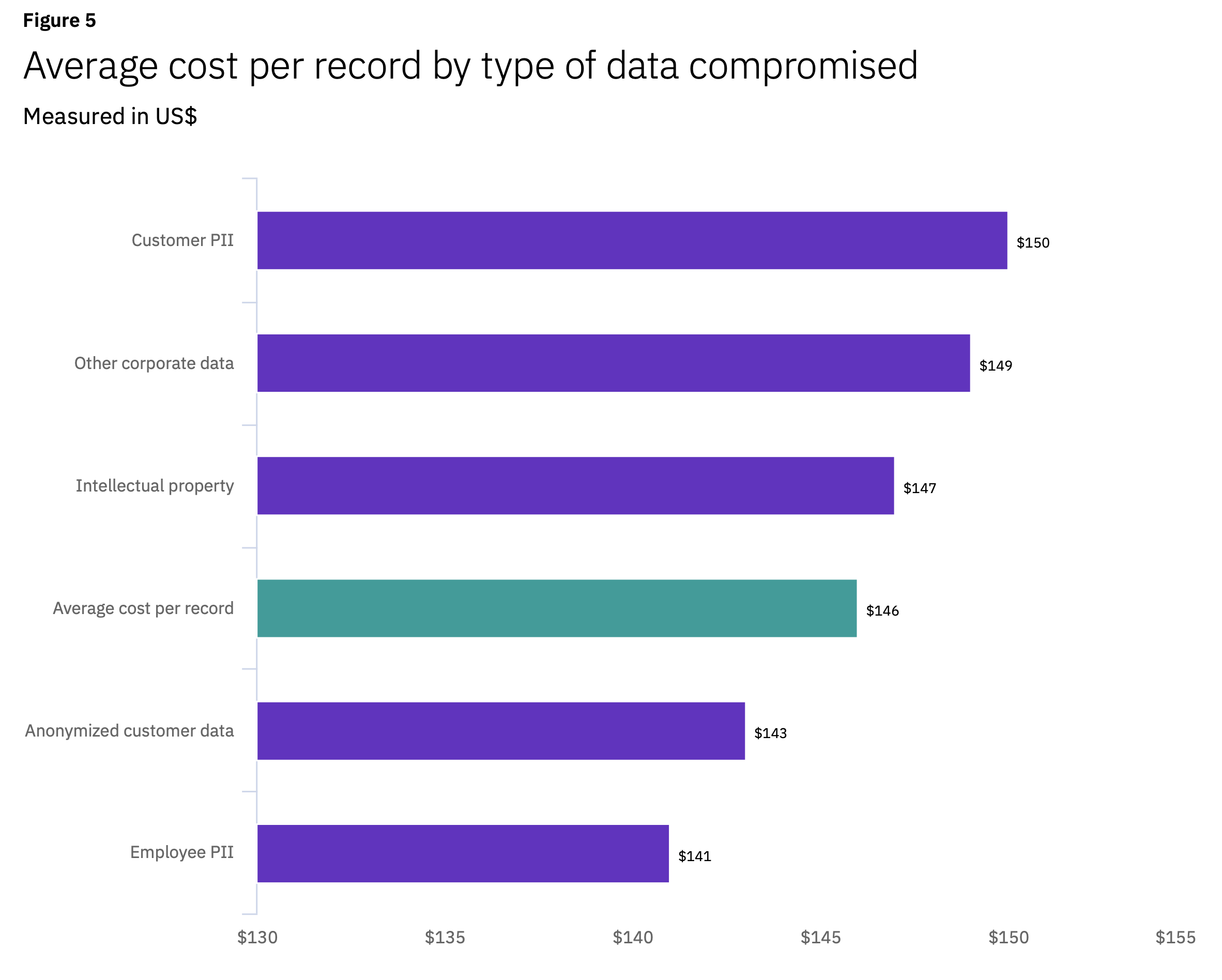 Source: Ponemon IBM Cost of a Data Breach Report 2020
Source: Ponemon IBM Cost of a Data Breach Report 2020
So how can application developers ensure that personal data is well protected? And in doing so, how can they demonstrate to their customers that they’re doing the right thing (vs. those lazy competitors who take all the shortcuts)?
The Trust-Me Dance
To earn business as a SaaS provider, you have to first earn trust. For larger business customers and regulated customers, the bar for that trust may be quite high and may include rounds of review by an infosec team involving long questionnaires.

Most SaaS companies handle this by putting together a song and dance that incorporates commonly requested data points, including the following:
- 3rd-party SOC 2 audit reports (or PCI or similar)
- Results of external pen-tests
- Statements of security measures including descriptions of the use of HTTPS and transparent disk encryption
- Authentication and identity options like SSO and 2FA
- Descriptions of access controls for users and access controls for SaaS employees (if any)
This trust-me dance is par for the course and absolutely required for enterprise sales. The dance is successful when the customer’s infosec team perceives the business value to be worth the risks to the data, provided those risks don’t run afoul of any regulations or compliance requirements.
Or that’s how it’s historically worked.
With new privacy regulations, increasing costs for breaches, and the fallout from supply-chain attacks like the SolarWinds hack, security-conscious customers need more.
It’s time to move beyond the trust-me dance and to offer guarantees that give the customer a security model that goes beyond the classic full-trust model.
Premium Privacy and Security
A number of major SaaS vendors from Snowflake to Slack to Salesforce offer application-layer encryption options where the customer can hold the key. This pattern is often called CMK or BYOK and the most recent company to announce planned support is Atlassian.
Different companies use different names for this and we’ve compiled a list of sample companies with their feature names and design approaches in an infographic.
One thing these companies have in common is that they charge customers extra for this level of security. At best, it’s part of their enterprise offering and at worst, it comes at a significant premium.
The idea of SaaS companies charging a premium for strong security might be disappointing to some, but it provides incentives for companies to invest in these features. If these incentives are effective then eventually these premium security and privacy features will become a standard part of all SaaS offerings.
The major incentives for SaaS providers:
- Make the sales process with security-conscious customers smoother;
- sell into regulated verticals;
- move up-market and win deals with larger companies;
- differentiate against competitors;
- and increase account lifetime values.
If you could be more secure and also have the market reward you for it, wouldn’t you do that tomorrow?
What’s This Magic Feature?

Typically called Customer Managed Keys (CMK) or Bring Your Own Key (BYOK), it’s an architectural pattern that encrypts customer data with per-customer keys controlled by the customer.
In a B2B SaaS context, this means Business A’s data is encrypted with Business A’s key, and Business B’s data is encrypted with Business B’s key. This encryption is done in the application, so by the time the data gets to persistent storage, it is just garbled bits. Even if a hacker gets access to storage on a running server, there’s nothing to steal.
More importantly, many of the CMK patterns give customers transparency into how their sensitive data is accessed with audit trails that they can use for monitoring or compliance.
Why Should SaaS Companies Offer It?
1. Mitigate damage in case of a breach.
All SaaS software has vulnerabilities or uses components that have vulnerabilities. Every day is another roll of the dice to see whether one of those becomes the vector of a breach. According to Ponemon’s 2020 report, the average breach takes nearly a year to detect and mitigate, which is why many security professionals presume their network is already compromised.

But if the data is encrypted and the attacker doesn’t gain access to the keys or the decrypted data, then the breach is a non-event. It doesn’t need to be publicly disclosed.
Encryption can massively reduce the damage if and when a breach happens.
2. No more “on-prem”.
Large enterprises continue to ask for “on-prem” options (even if “on-prem” frequently means “my cloud infrastructure”). This is because their risk of losing data expands with every new cloud application.
But delivering, updating, and providing support for on-prem software is costly and fraught with problems. Everything from the initial rollout to updates to support is painful. CMK gives companies that demand on-prem software a feasible cloud-based alternative.
3. Satisfy security-conscious business customers .
Many SaaS companies, regardless of industry, are hearing these requests from their biggest customers. These requests typically originate with the InfoSec team rather than the business buyer, endangering sales. With CMK, the business sponsor can overcome the internal infosec hurdles and complete the purchase.
4. Add to the bottom line.
More sales. Bigger sales. Higher deal values. The ROI on Customer Managed Keys makes it one of the most impactful things you can do for your product today. And if you use IronCore’s SaaS Shield product, you can deliver to your customers quickly and with minimal to no impact on your engineering team.
What does the customer get out of it?
1. Data access transparency
One of the biggest concerns coming from large customers is how much access curious insiders on the vendor’s staff have to customer data. Customers can spend a lot of time asking about how many people and what job titles have access and what gates exist to protect data. Ultimately, the best assurance you can provide your customers is data access transparency, which allows customers to see the who, what, and where of access to their data.
When CMK is combined with real-time audit trails that go directly to a customer’s SIEM or logging infrastructure, all data access becomes transparent. Not only does it prevent a curious database admin from browsing through the database, but if that admin manages to get access to the encrypted data, a rich audit trail is generated and sent directly to the customer.
Note: this isn’t a feature of all CMK approaches, but is fundamental to IronCore’s approach.
2. Revocation / Remote Delete
When a customer holds their own encryption keys, they can choose to withhold them. Without access to those keys, the SaaS vendor will not be able to access that customer’s encrypted data. Crucially this includes backups and other copies, too.
Customers want to be able to pull back their data if a vendor gets breached or if they want to migrate to another solution and make sure they aren’t leaving sensitive data behind.
3. Compliance
Every jurisdiction and every industry has its own set of rules. Most companies have to navigate numerous regulations across jurisdictions.
In the United States, for example, public companies need to worry about non-public information that could impact a stock price such as forward-looking plans. If they don’t, Sarbanes Oxley could bite them. Other data may be covered by the EU’s privacy laws or by privacy laws from individual states.
No matter the specific regulations, compliance is made easier when data is encrypted and all access is logged.
4. Data Locality, Privacy Shield, and Schrems II
A focus on data residency is cropping up in an increasing number of countries. And with the Schrems II decision, maintaining data residency within a locale is not guaranteed to protect a U.S. company holding E.U. citizen data.
Interestingly, allowing a customer to hold their own keys, as long as they keep them within their country of residence, satisfies many residency laws and addresses the Schrems II decision as well.

Conclusion
So how do you handle sensitive data in the cloud? Very carefully.
And preferably with strong encryption and a stronger key management and access transparency story. IronCore Labs provides some fast paths to add these features, and there can be huge upsides to getting them deployed quickly. Get a trial started with IronCore today.




