Private Communications for Email and Text Messages
Patrick’s Privacy Practices Part 2
This is one of a series of posts on how you can protect yourself and your privacy online to the extent it’s within your power (links will be added as new parts are published):
- Part 1: Identity Theft Protection Checklist
- Part 2: Private Communications for Email and Text Messages (this blog)
- Part 3: Privacy Guide to Apple Intelligence with ChatGPT
- Part 4: Recommended Privacy Settings and Alternatives for Google, Search, and YouTube
- Part 5: Recommended Privacy Settings for iPhone and MacOS
- Part 6: Privacy and Social Media
- Part 7: Basic Security
In this part, we consider the next questions I’ve been asked recently: “Should I close my Gmail account?” and “Should I move to WhatsApp or Signal?”
Why It Matters
Motivating these questions are worries that, in the U.S., a more authoritarian government is coming and with it, increased invasions of privacy to identify and punish opposition and protesters, to track women’s health and reproduction, to find and round up illegal immigrants, and so on.
And while there’s precedent for abuse of surveillance powers in the previous Trump administration, it’s worth noting that it was the Biden administration who used geofence data (identification of anyone whose phone was in a certain area at a certain time), social media scraping, facial recognition identification, and subpoenas to a ton of private software companies who make mobile apps in order to track down January 6th rioters. These tools can be used by any government and can be aimed at any group.
I choose private communications not out of a distrust of the government or a worry about criminal investigations, but on principle. Protecting your privacy regardless of who the president is is good practice. Mass surveillance (as opposed to targeted and court-approved surveillance) is wrong, and anything that undermines it is good. Companies don’t do a good job of keeping our data out of the hands of hackers, so I choose to pick technologies that reduce the chances that my data will leak.
When I have a private conversation with others – via voice, video conference, in person, email, text message, or whatever – I expect the conversation to stay private. We all make that assumption. But these days, those conversations are often being captured, stored, and analyzed by private companies, which makes them susceptible to subpoenas from the government, theft from hackers, leaking from new AI models, and so on.
Companies that promise not to use your info today can change their minds tomorrow. Startups often begin with strong ideals before they shift to proven tactics for making money that erodes their original consumer-friendly policies. This is an oft-repeated process now widely called “enshitification” (see this talk by Cory Doctorow to learn more – it’s worth your time).
It doesn’t matter who’s president, what country you live in, or whether you’re a law-abiding citizen. You should fear the corporate overlords, the hackers, government overreach, bad data that leads to false accusations, and more. Ensuring your private conversations are actually private is something everyone should do on principle.
Private vs. Secret Conversations
Before we go any further, let’s distinguish between private and secret conversations. A private conversation is like stepping away from a party into a backyard that’s otherwise deserted to have a conversation. Anyone can look out and see who you’re talking to, but they can’t hear what you’re talking about.
However, sometimes, you don’t want others to know you’re having a conversation with someone. You want to have a conversation where no one can see you’re having it. That’s a secret conversation where both the contents and who you’re talking with are private from everyone. This is most important to people like whistle-blowers, dissidents, and journalists.
While you and I may not need the level of protection provided by secret conversations, it can be good to aim for this level of privacy anyway. For one thing, you provide cover for the whistle-blowers and dissidents who do need it and for your future self if something changes.
If you lived in the U.S. in 1945 and you were curious about more egalitarian methods of government, you might have attended a communist party meeting. At that time, such attendance would be completely innocuous – the war just ended, and Russia was an ally. But a few years later, President Truman created a loyalty test for federal employees, and by 1950, anyone who had ever attended a communist meeting was being accused of disloyalty to the United States. These people were being fired, put on blacklists, and arrested. Even people who were merely friends with the accused came under suspicion.
Here’s where it gets frightening: McCarthy, Truman, and the others hunting for communist sympathizers didn’t have a fraction of the tools of surveillance governments possess today. If fear and populist rhetoric ignited a new McCarthyism, the government would be able to utilize social media, digital photos, pervasive security cameras, facial recognition, and digital location histories kept by your telco, your phone, and its many apps. They could buy information from data brokers and ad companies on people who have particular political leanings. And they could trivially assemble lists of associates. Those tools in the hands of a McCarthy are a scary prospect.
The Woes of Email
When it comes to privacy and security, email is the worst. When you send an email, there are multiple records of who you are emailing, and even if you delete an email, it still exists in the mailboxes of the other recipients. Even your own copy of the email may be duplicated across the server and one or more mail clients (desktop, mobile, etc.), and the same for the other end of the conversation.
Often, email gets relayed through multiple servers. Many servers support secure TLS encryption to protect the mail as it travels between mail servers, but quite a few still don’t support it, so you can’t even know if your email will be protected from passive snooping at Internet routers. And that’s the tip of the iceberg.
Attempts to secure email have generally been bolt-on approaches using S/MIME or PGP to encrypt message contents. I’ve used both of these for years for signing emails and for encrypting them, but few correspondents can handle these secure emails and even then, implementation incompatibilities create issues. For example, I stopped signing all my emails when I got multiple reports of emails being discarded by recipient email systems. It turns out the recipients used mail-server level anti-virus scanners that modified emails to add a message saying the email was scanned, but this changed my message, which broke the email signature, which caused a downstream server to discard the mail. Security is important, but deliverability is also important.
So, what’s the best option for email privacy and security? We’ll get there, but first, let’s look at the most popular email system in the world.
Is Gmail Okay to Use?
Google’s email service is actually pretty good in a number of ways. They do a fair bit to detect phishing attempts, spam, and viruses and to keep users’ accounts protected (all with mixed success). They can optionally auto-categorize your emails and surface “priority” emails above the regular noise, which is a great feature. Additionally, you can use almost any email client with Gmail if you don’t like using a web browser. And you can’t beat the price (free).
However, Google’s business model is advertising, and they make more money when they know more about you. Google puts ads into your inbox to make money off their free service. But if they are low-key, we can live with ads, and if you use your own mail client, you don’t even see them.
And despite their advertising model, Gmail help says your messages are not used for ads:
We will not scan or read your Gmail messages to show you ads.
The Gmail Dark Side Part 1: Advertising Data
In fact, that’s an improvement over most of Gmail’s lifetime. They only stopped mining people’s emails in 2017 after lawsuits and a ton of bad publicity. Yet, in 2019, they were caught extracting purchase information from emailed receipts). Hmmmm.
Here’s the thing I find suspicious: if you parse their words carefully, there’s some ambiguity. They promise not to read the “message” of the email, but does that include the metadata such as the To and From addresses?
If we look at their privacy policy, it has these interesting bits:
We collect information about your activity in our services, which we use to do things like recommend a YouTube video you might like. The activity information we collect may include:
- Terms you search for
- Videos you watch
- …
- People with whom you communicate or share content
- Activity on third-party sites and apps that use our services
…
We don’t show you personalized ads based on your content from Drive, Gmail, or Photos.
(emphasis added)
I suspect they’re carefully parsing their words to make you feel confident in your mail’s privacy while at the same time mining the envelopes of your emails. Their policy allows them to watch who you email with and to use that information to build advertising profiles on you.
If you get a lot of emails from Zappos, they can surmise you like to buy shoes. If you get emails from REI, they can infer that you’re interested in outdoor products. If you get emails from a particular political party, they can infer your political preferences, and so on. All without reading “your Gmail messages.” I don’t have proof that they’re actually doing this, but they’ve at least left the door open to doing so.
The Gmail Dark Side Part 2: Unencrypted Data
Irrespective of how they build profiles on you, it’s indisputable that Google doesn’t encrypt your stored emails – at least not in a way that’s meaningful on a running server. They use low-level encryption that protects your data when they throw out hard drives, but they don’t use encryption that prevents their employees, hackers, or governments with lawful requests from reading your data.
If Google receives a request from a government for your emails, Google hands your information over, often without you knowing. Google’s transparency report, which is laughably thin on information compared to other companies, shows that in the second half of 2023 alone they received 217,000 requests covering 441,000 accounts and handed over the requested information around 75% of the time globally and 86% of the time in the U.S.
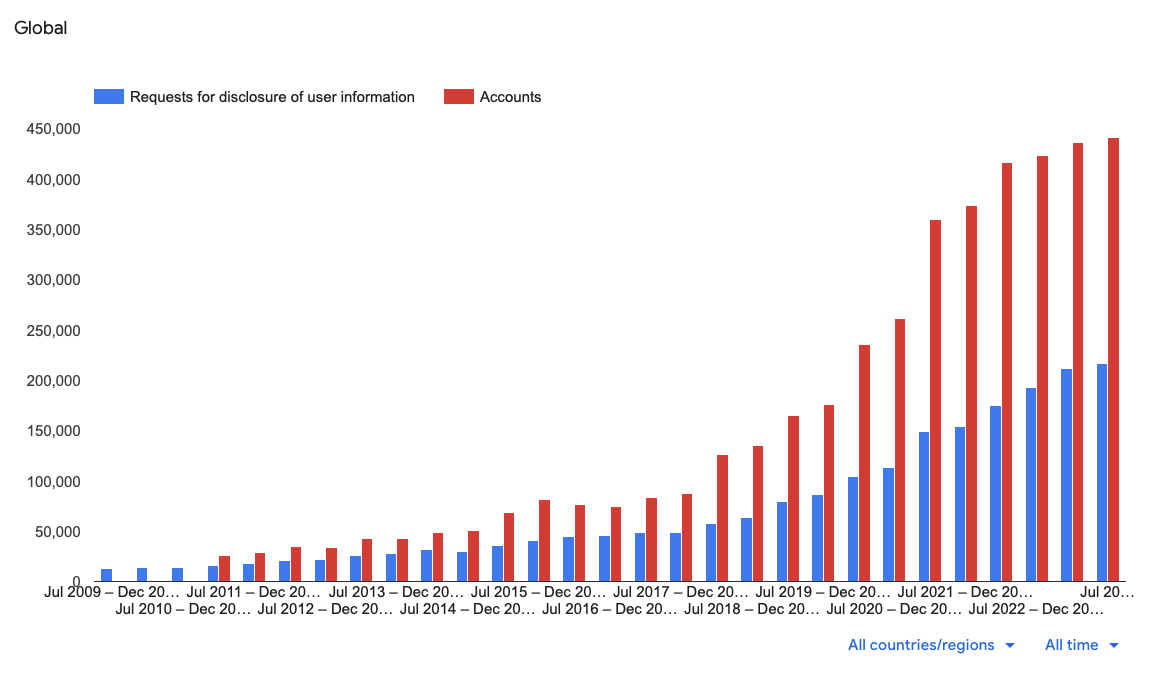
Law enforcement catches and convicts numerous criminals in this way, but let’s be clear: if Google protected that data such that they couldn’t read it and couldn’t deliver readable emails to law enforcement, then law enforcement would still be able to collect evidence by getting a warrant directly for the suspects’ devices. That’s a harder path, but justice can still be served. Fishing expeditions, however, get curtailed.
The Gmail Dark Side Part 3: Artificial Intelligence
And then there’s the question of AI. Google has been pushing AI into all of its products and nagging people to adopt it with messages like, “Unlock new levels of efficiency with AI.” (Oddly, they don’t learn when I repeatedly say no - maybe that’s Artificial Ignorance.)
Google makes it very hard for you to opt your data out of their AI models. According to WaPo:
Unless you turn it off, Google uses your Gmail to train an AI to finish other people’s sentences. It does that by analyzing how you respond to its suggestions. And when you opt in to using a new Gmail function called Help Me Write, Google uses what you type into it to improve its AI writing, too. You can’t say no.
(emphasis added)
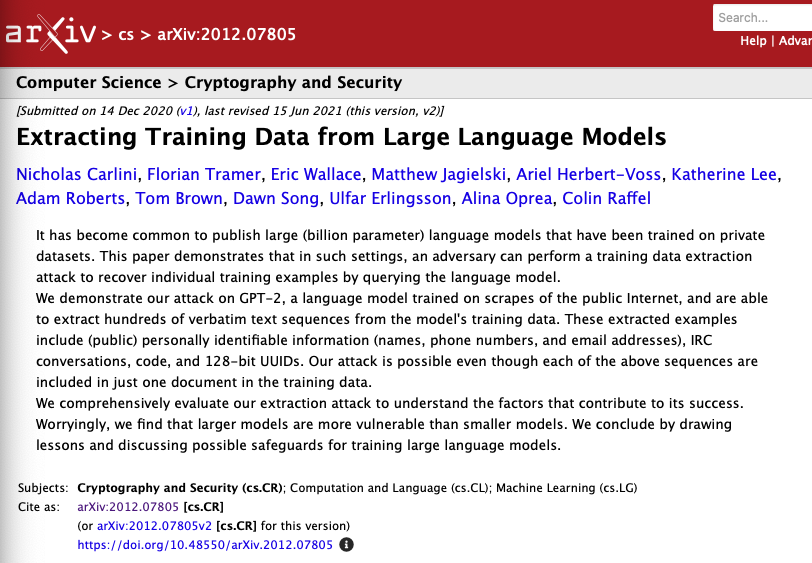
So, while they say they won’t read your messages “to show you ads,” they do use your emails to train their AI models. And training data can be extracted back out of these models, which is hugely problematic for privacy (we linked one paper here, but there are now thousands of papers showing how to attack these models).
You can opt out of some AI training by disabling the “Gmail Smart Features” option, but turning that off also disables all the best Gmail functionality like automatic categorization of emails. This is typical for Google. They say you can turn off the privacy invasions, but then they punish you for your choice by making your experience with the product as bad as possible until you relent and let them mine your data.

Your choices: help them train models or use a crippled product.
The Gmail Dark Side: Conclusion
The bottom line is that Google is sneaky about using your data while telling you it’s private and safe. It’s misleading, and they do that because their business hinges on their ability to use your data. Gmail provides a good user experience and has some great features, but private and secure communications are not among them. (Note: the paid version of Gmail aimed at businesses, Google Workspace, has better privacy policies, but the same security drawbacks.)
Confession time: I still have a Gmail account. I mostly use it for junky emails like newsletters and as a vendor contact, though I do get some personal correspondence there. But I’m planning to wind down my account over the holidays this year. The process of changing an email address and getting people to use the new one isn’t quick, but the AI stuff is the final straw for me. It’s time.
Secure Email Alternatives
What you need is a private email service that encrypts your data such that you can read it, but the service provider can’t. This way, if a hacker gets into either of their environments or law enforcement asks for copies of emails, they can only share garbage data.
Secure Email Type 1: Encrypt Select Messages Only
One approach to securing email harkens back to the days of PGP and S/MIME (if that means anything to you) as a bolt-on to other email services including Gmail. These let you click a button when composing an email that encrypts that email. The recipient has to have an account with the service, or you have to share a password for the email with them using some other mechanism, like a phone call. This isn’t great for usability, and you’re not likely to use it for the bulk of your emails.
There are two leading services that fit this description today: Preveil and Virtru. Both of these are good, but they only protect expressly confidential emails that you flag for encryption, which is probably 0.01% of your email. That’s why I’m not recommending them.
Secure Email Type 2: Encrypt Your Stored Messages, Intra-Service Messages, and Select External Messages
The better alternative is a service that always encrypts your data on their servers so they can never read your stored email. Emails to other users of the service stay secure for their entire lifecycle. Emails to outside users, like your accountant, can optionally be encrypted using a previously shared password. These are imperfect when you communicate with people using, for example, Gmail, but it’s still a huge step up in privacy and security.
The two leading services in this category are Proton and Tuta.

These two services have similar features – both offer secure email, calendaring, email aliases, and easy-to-use security. They’ve both published their source code for their mail clients, which shows transparency, which is important for this type of security.
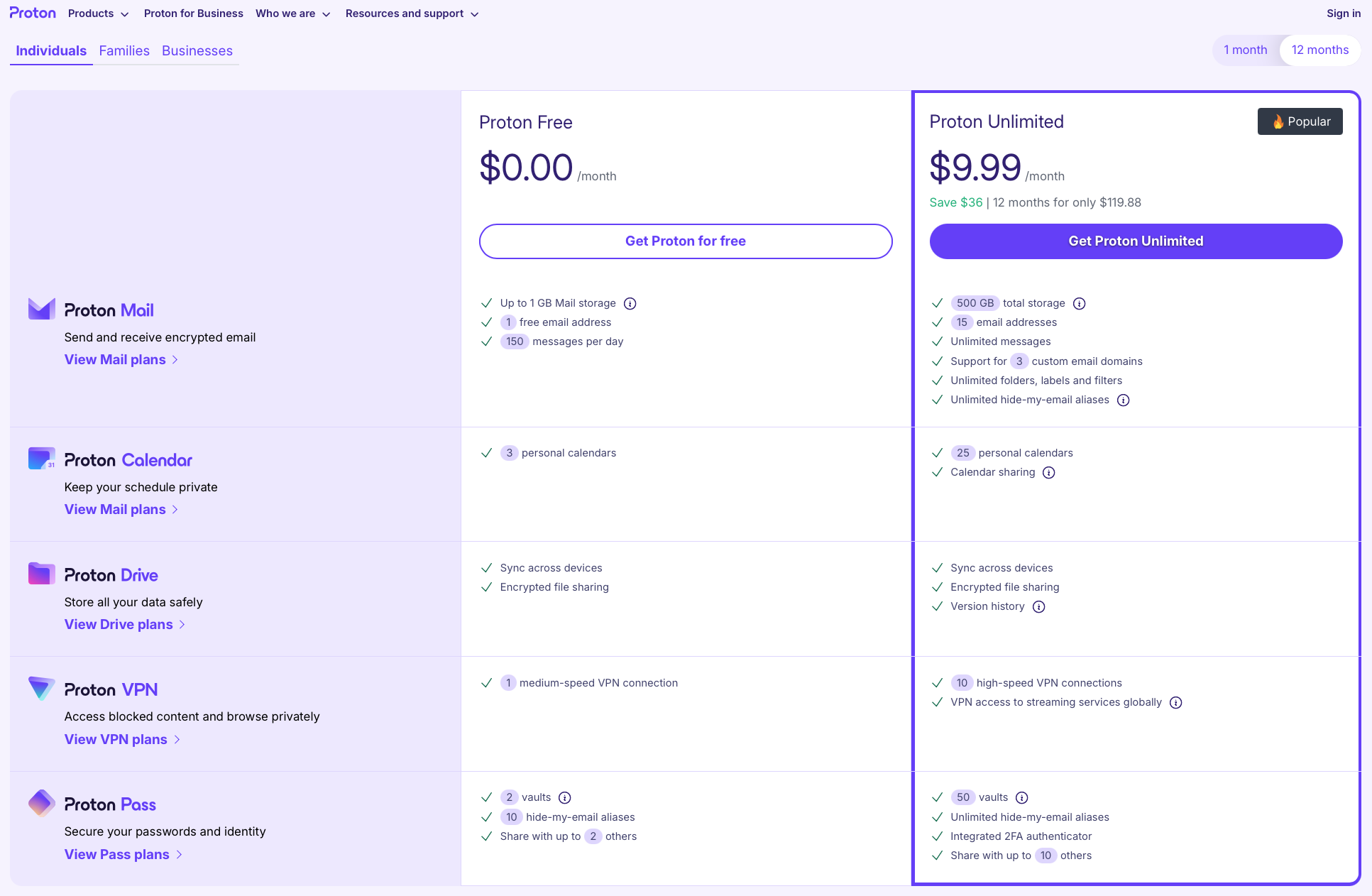
They’re both good services. Proton bundles a larger software suite, so you can also store files securely and use a VPN. They both have free tiers that allow up to 1GB of storage but include some other limitations (Proton’s is slightly more restrictive with a per-day email limit of 150). For paid options, Tuta has a $3/mo tier and a $8/mo tier, depending on your needs. Proton is more expensive and only has one paid tier option for individuals at $10/mo (there are family and business pricing options, too).
I find the usability and power of Proton to be slightly better, though Tuta has slightly better security, particularly around how they handle email subject lines. That said, I recommend Proton for these reasons:
- The usability is better
- I prefer the Proton interface over Tuta, but I like to use the Apple Mail client on my laptop, which I can only do with Proton.
- They both require their own mobile apps unless you get into some advanced proton setups.
- Proton has a great help section and terrific documentation for all levels of users.
- It’s easier to migrate
- Proton offers a migration tool to ease on-boarding.
- More functionality
- Proton Drive for securely storing and sharing files.
- Private AI, which offers AI writing assistance without worries about your data being seen or getting used for training.
- Many more options, customizations, and creature comforts.
- The popularity
- Proton has 10x more users at 100 million versus Tuta’s 10 million.
- This means more emails to more people will be completely secure, which is a big deal.
- Good anti-spam, anti-phishing, and anti-virus
But both are good with trade-offs either way. Pick one of them or try them both.
Alas, moving to Proton or Tuta is not a perfect solution. You will lose some features like a priority inbox (though you can create rules to file emails) and further, email is just fundamentally broken. If you want to protect who you are and who you communicate with (secrecy), you shouldn’t use email at all.
Also, with both of these services, the free accounts are pretty limited, which means you’ll probably have to pay for your email. And that’s pretty typical in this world: you often trade off privacy and security when you use free services. Better-off individuals will be able to afford better privacy and security than others. It’s deeply unfair, but it is what it is. If you can afford it, you should do it.
SMS Text Messaging – A Disaster
That’s email, but now what about text messages? It turns out standard text messages (aka SMS messages) are a privacy disaster. Your mobile operator probably stores the content for all of your messages, possibly for a very long time. Nearly all telcos in the U.S. were recently hacked by China, and all of those text messages were available to the hackers. You really shouldn’t trust telcos with your data, as they’re getting hacked all the time:
Sources include firewalltimes.com and recent news reports.
The Walled Gardens: Apple vs. Android
But these days, SMS messages are being used less, particularly if a user is texting someone or some people who are on the same platform.
Apple Messages
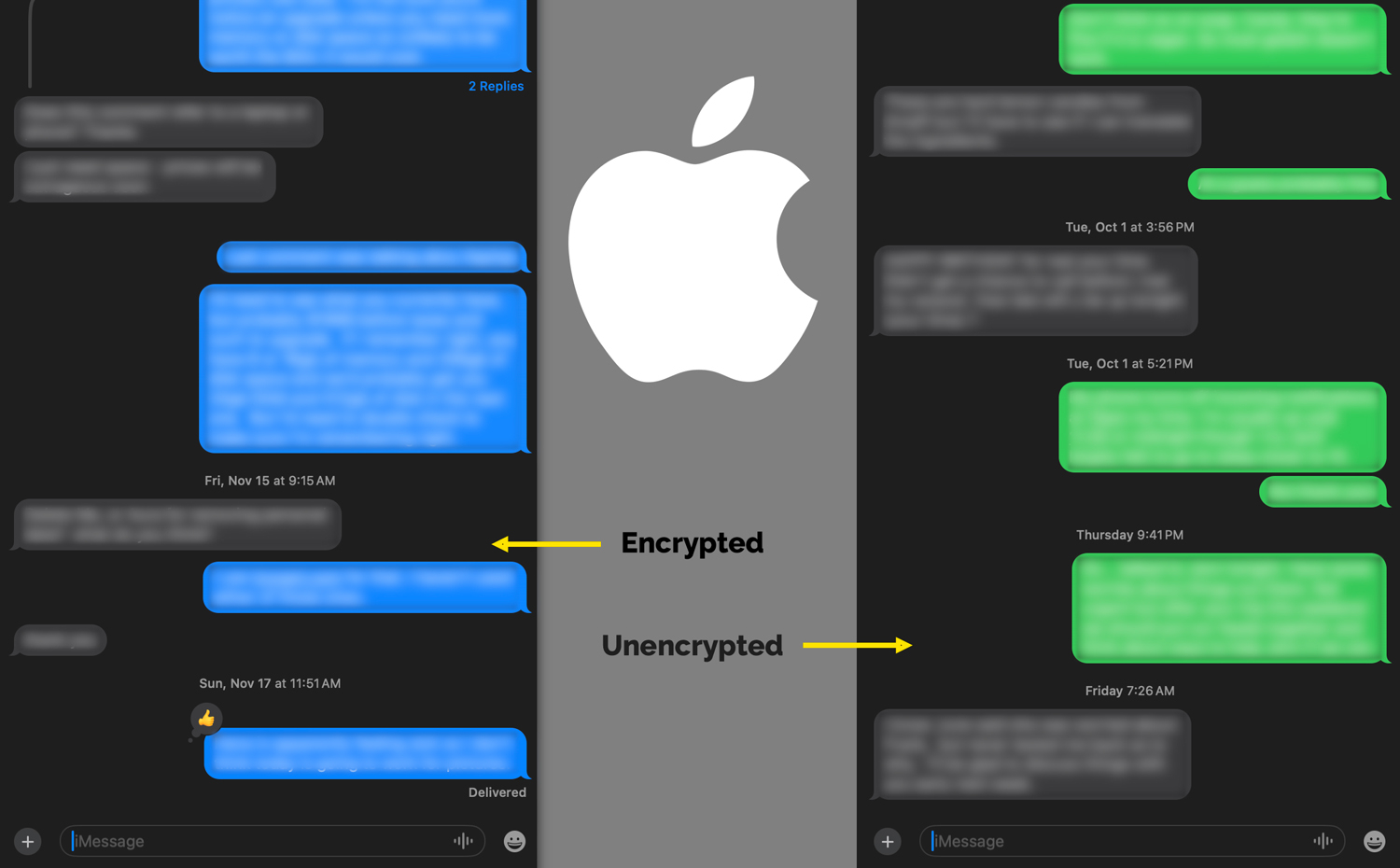
For example, there’s the Apple Messages app on Apple devices. This app is fantastic when communicating with other Apple devices. If you’re using an iPhone and you send a text message that’s blue, then that text message is end-to-end encrypted, and even Apple employees can’t see the contents. A breach of Apple wouldn’t uncover your text messages, and law enforcement can’t get access to your messages through Apple (though they can through you).
Apple has made its Messages app secure from almost the beginning, and it deserves a lot of the credit for pushing the industry (and competitor Google) forward on privacy and security.
Unfortunately, Apple Messages are decrypted on your phone and also decrypted in your phone’s backups if they’re stored in iCloud unless you’ve enabled “Advanced Data Protection” on your account. Law enforcement knows this and subpoenas Apple for iCloud backups as a way to get at people’s otherwise encrypted text messages. Even if you turn on Advanced Data Protection (see a later article in this series for instructions), you can’t know if the people you communicate with have turned it on or if they store their backups with Apple, which means your messages could be accessed by someone (an Apple employee, law enforcement, or a hacker) looking at the records of your friends.
Finally, Apple’s services, even when configured properly, bring privacy, but not secrecy. They don’t protect who you communicate with, only what you’re communicating.
Google Messages
Android is even more complicated: if you use Google Messages and are on the most recent version, then you may have the ability to use RCS (Rich Communication Services, a standard that’s slowly replacing SMS). But this will depend not just on your phone and version but also on your carrier, which may or may not support RCS. And RCS can be encrypted, but that isn’t guaranteed. Google finally enabled encryption by default, but it only works when all participants have the ability to use encrypted RCS and their settings are correct. You’ll know if you won the lottery and have an encrypted conversation if you see this tiny little icon with an even tinier lock icon on it:
![]()
Lack of Secure Interoperability
And if you’re text messaging between Android and iPhone users, then messages will NOT be encrypted at all, at least for now. On Apple you’ll know this because you’ll see messages that are colored in green, which indicates that they are not encrypted and that telcos and others can read them, store them, and cough them up to hackers and governments. Apple is adding RCS support, but because the encryption portion isn’t yet a standard, they aren’t adopting encrypted RCS any time soon.
The Better Approach: Cross-platform Encrypted Text Messaging Apps
We’re lucky here in 2024 because there are now quite a few popular options for encrypted messaging including:
I talk about Telegram vs. Signal in another blog post, and I won’t retread that here. My bottom line is that I prefer to avoid Telegram. Read the blog for details.
WhatsApp has some great tech (it borrows some of it from Signal, in fact), broad usage, and is a generally good solution. But it’s now owned by Facebook parent Meta and I have a deep-seated distrust of their intentions when it comes to privacy. Even if it is secure and private today, there’s absolutely no guarantee that will be the case in the future.
And that leaves us with just one encrypted messenger still standing: Signal.
Recommendation: Use Signal
While all of these apps bring the ability to encrypt messages across platforms, the one I recommend is Signal. For one thing, they’re a non-profit dedicated to protecting privacy. They’ve pioneered some fantastic encryption, and their protocols have become standards. They’re open-source and fully transparent. I’ve poured over the technical papers describing the underpinnings, which are well designed and executed.
Signal is the only app that brings secrecy as well as privacy; that is, Signal goes to lengths to avoid knowing who you are or storing anything about who you talk to. And since it’s free, they never have accounts that are tied to credit cards.
This is the app to use (together with disappearing messages) if you’re secretly talking to reporters or whatnot.
And it has a great user experience. In addition to secured text messages, it supports voice and video calls and has a social-media type feature called stories, which provides an ephemeral way to share photos and videos with friends and family, which auto-delete after 24 hours.
If you message someone with Signal, you don’t have to wonder if it is private. It is. Always. You don’t have to worry about the contents of those messages or who you’re talking to leaking to an authoritarian government because Signal doesn’t store the data that those organizations want.
In addition, it’s quite popular, particularly among technology, privacy, and security professionals. Unfortunately, it isn’t something you can assume all your cousins and aunts and uncles have installed already. Which means you might need to evangelize (point them to this blog?). If you can get your group chat participants to use Signal, you’ll create a big privacy and security win for you and for them.
- Switch to an encrypted messaging service such as Signal
- Encourage people you text with to also switch to Signal
Conclusion
Private communications are a human right. Governments and private companies should have compelling reasons to read your emails and chats, but the typical services don’t treat your data with the care they should.
On the email side, there are some highly usable free email services, like Gmail, but their attractiveness is surface level only. The underbellies are disappointing. Using a more private email service like Tuta or Proton comes with trade-offs in cost and functionality, but the benefits of knowing your assumptions about private emails actually being private are priceless.
On the text message side, the default Google and Apple Messages apps support good privacy in limited circumstances. Everyone needs to have the right settings enabled, and everyone has to be using the same app and platform before the security kicks in fully. To be sure all of your conversations are private, you should adopt Signal and push your friend circles to adopt it, too. At least signup and send messages to some of your contacts to let them know it’s an option.
The more of us who choose to use privacy-preserving services, the more normal it becomes, and the better off society is. Just having Signal is no good if I’m communicating with someone who doesn’t have it. Ditto with Proton Mail. We all need to remind our friends and family that we value privacy because we’d feel utterly violated if our emails or our text messages were hacked and made public (or obtained by law enforcement and put in public court filings or sold in summary form to advertisers, etc.). It doesn’t matter how innocuous those messages are, it’s fundamentally violating when messages we intended for specific people are seen by others.
Stay tuned for the next part, covering what settings you should turn on or off in your Google account and what to do about search.





