- Docs
- SaaS Shield
- What is CMK?
What is Customer Managed Keys?
Controlling Sensitive Data in the Cloud
Large enterprises want to protect the sensitive data they store in SaaS applications. SaaS providers want to continuously deliver value.
How can application developers give data control to their enterprise customers, while retaining the access required by the features of their software/ SaaS app?
One approach is Customer Managed Keys (CMK, also called Bring Your Own Encryption or Bring Your Own Keys). Major SaaS logos like Microsoft, Box, Slack, ServiceNow and NetSuite offer CMK as part of their solutions. A report from 451 Research cites that more than 40% of enterprise IT organizations are implementing CMK, and an additional 50% have intent to implement.
In this article, we’ll explore CMK and discuss how SaaS providers can ship advanced data controls faster and give enterprises they work with consolidated CMK vendor management.
How Does CMK Work
In a CMK solution:
- SaaS providers encrypt the sensitive data that they store
- Enterprise customers control and manage decryption keys
- Encryption and decryption requests are sent from SaaS provider infrastructure to customer infrastructure
Data is encrypted using envelope encryption - instead of sending the entire chunk of data to the customer’s infrastructure for encryption / decryption, the data is encrypted in the SaaS provider’s system using a random key, and that key is sent to the customer KMS to be encrypted. This keeps the request request size small and keeps the sensitive data in the SaaS provider’s infrastructure.
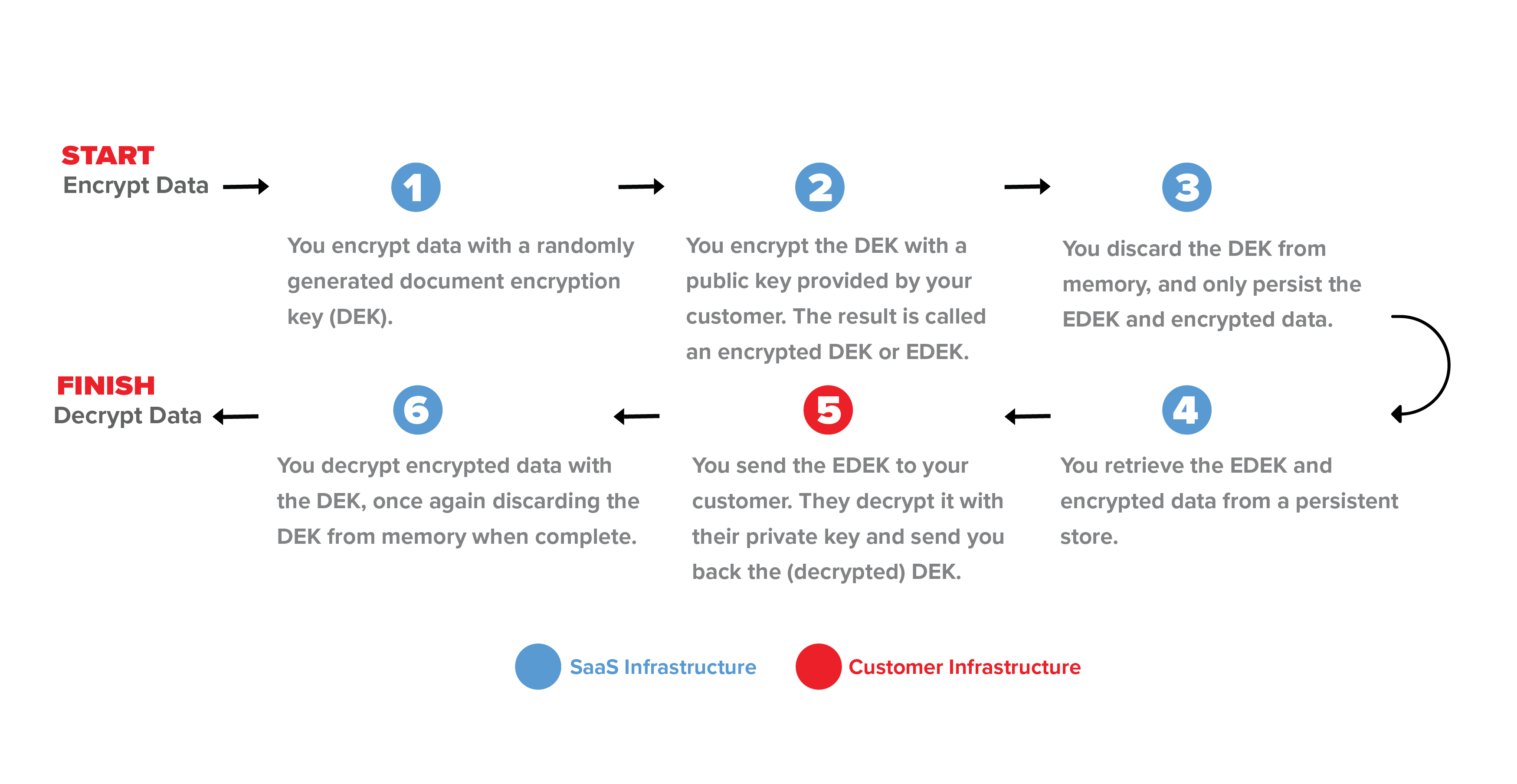
One of the challenges of CMK is that today’s implementations are ad-hoc and specific to a particular type and configuration of enterprise key management infrastructure. It’s common to see Gemalto (HSM), AWS KMS/CloudHSM, Microsoft AD/KMS, or Google Cloud KMS in the market. For enterprises, the average number of SaaS applications is 300, leading to a combinatorial explosion of integrations.
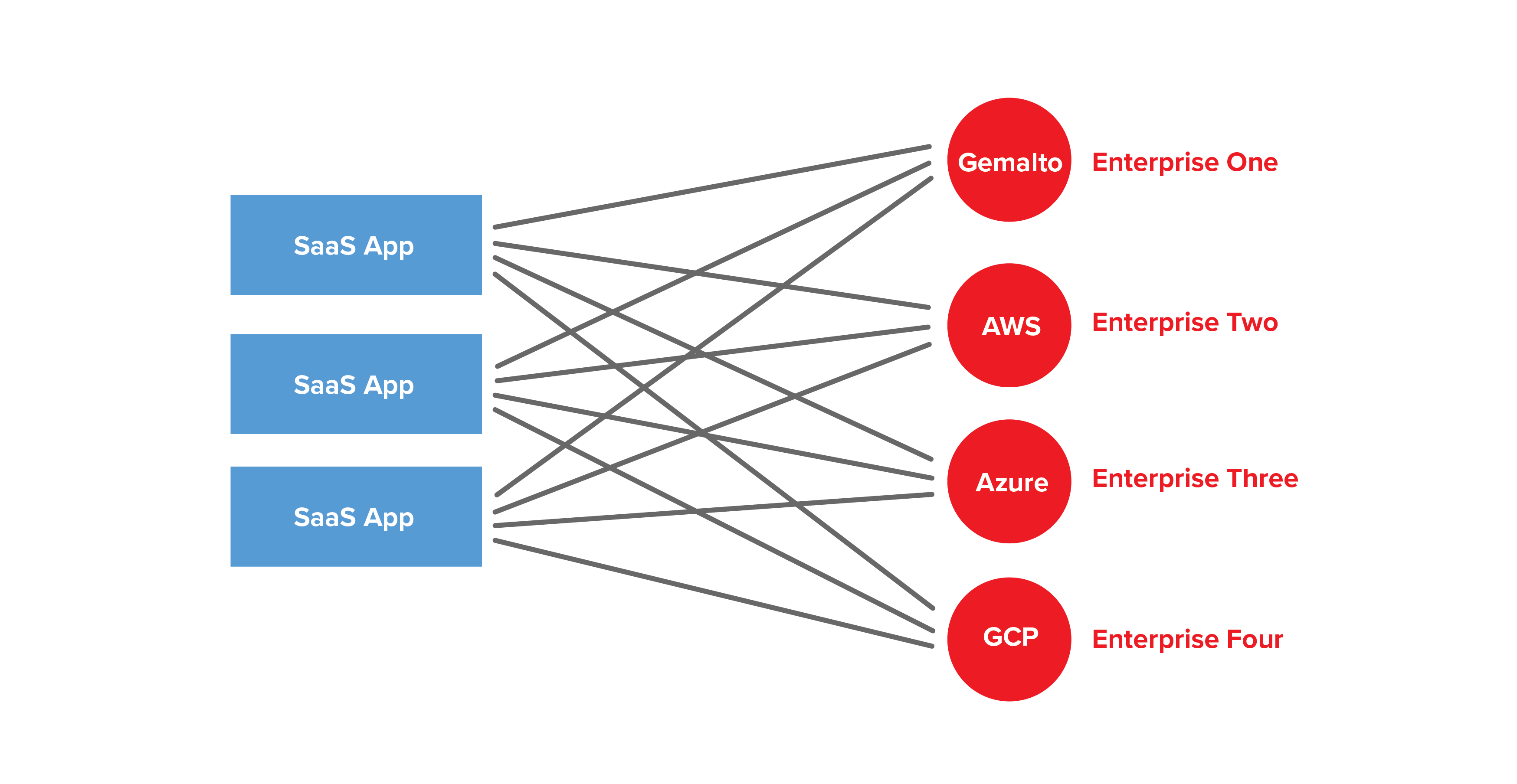
This type of bespoke implementation leads to high integration complexity, slow deployments, and poor reliability.
Reducing Integration Complexity
IronCore’s CMK solution provides a more rational implementation approach, introducing a small SDK that is integrated into the SaaS provider’s software.
JavaEncryptedDocument ciphertext = client.encrypt(documentMap, metadata); PlaintextDocument plaintext = client.decrypt(documentMap, metadata);
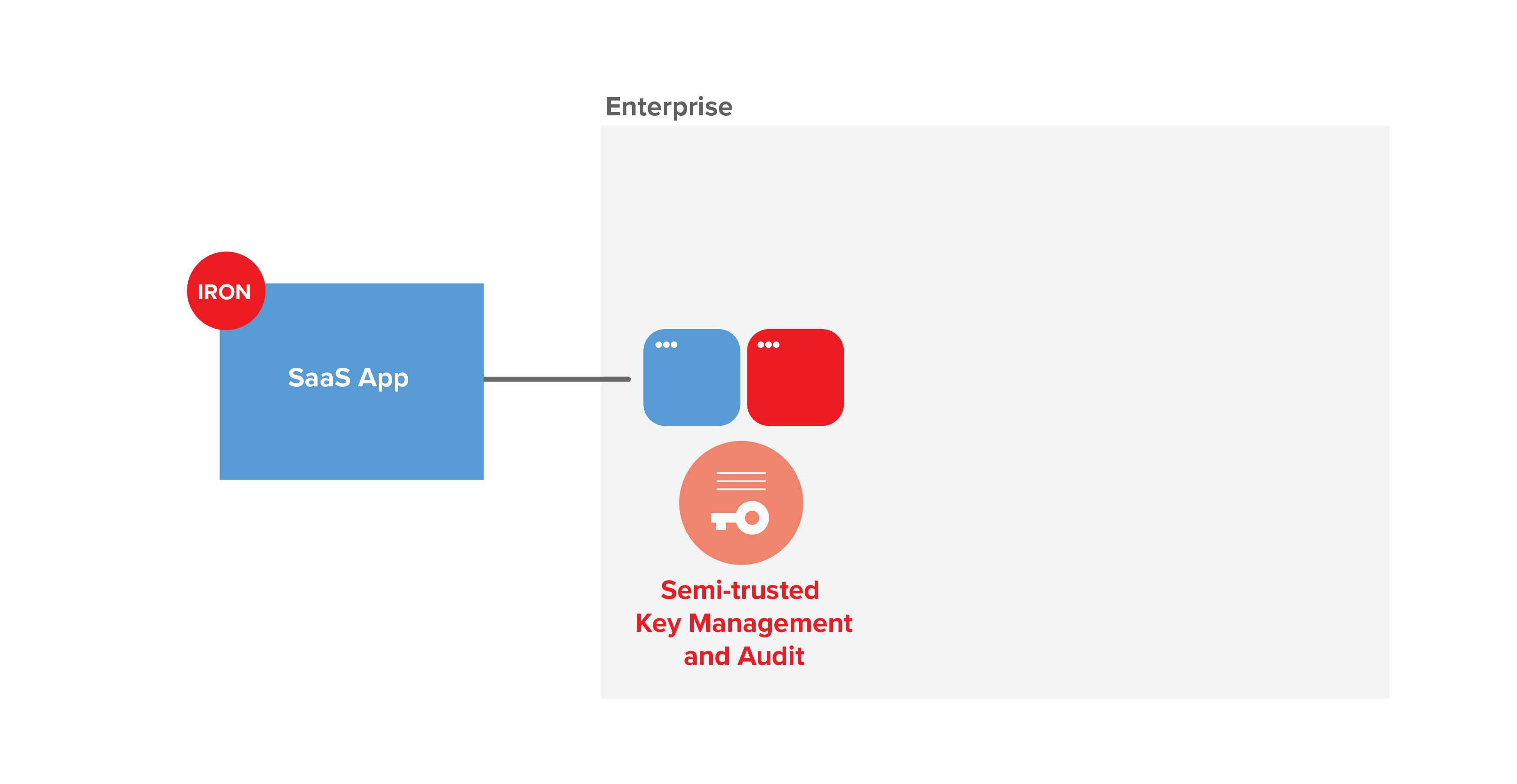
The SaaS provider and the enterprise each supply configuration information via a purpose-built administrative console. Log events are fed to standard logging and monitoring systems (e.g. Splunk, Cloudwatch). SaaS providers ship faster and enjoy lower integration complexity, while enterprises gain consolidated vendor management, advanced monitoring, and data control.
IronCore does the heavy lifting of abstracting the KMS infrastructure.
Multiple Deployment Options
Enterprises’ risk tolerance varies based on their size, industry, and regulatory requirements. It’s important that CMK be flexibly deployed. IronCore’s CMK solution provides public cloud, hybrid cloud, and on-premises data-center deployment options. IronCore also offers a key management and audit system based on transform encryption. This approach improves the trust model and lowers adoption friction.
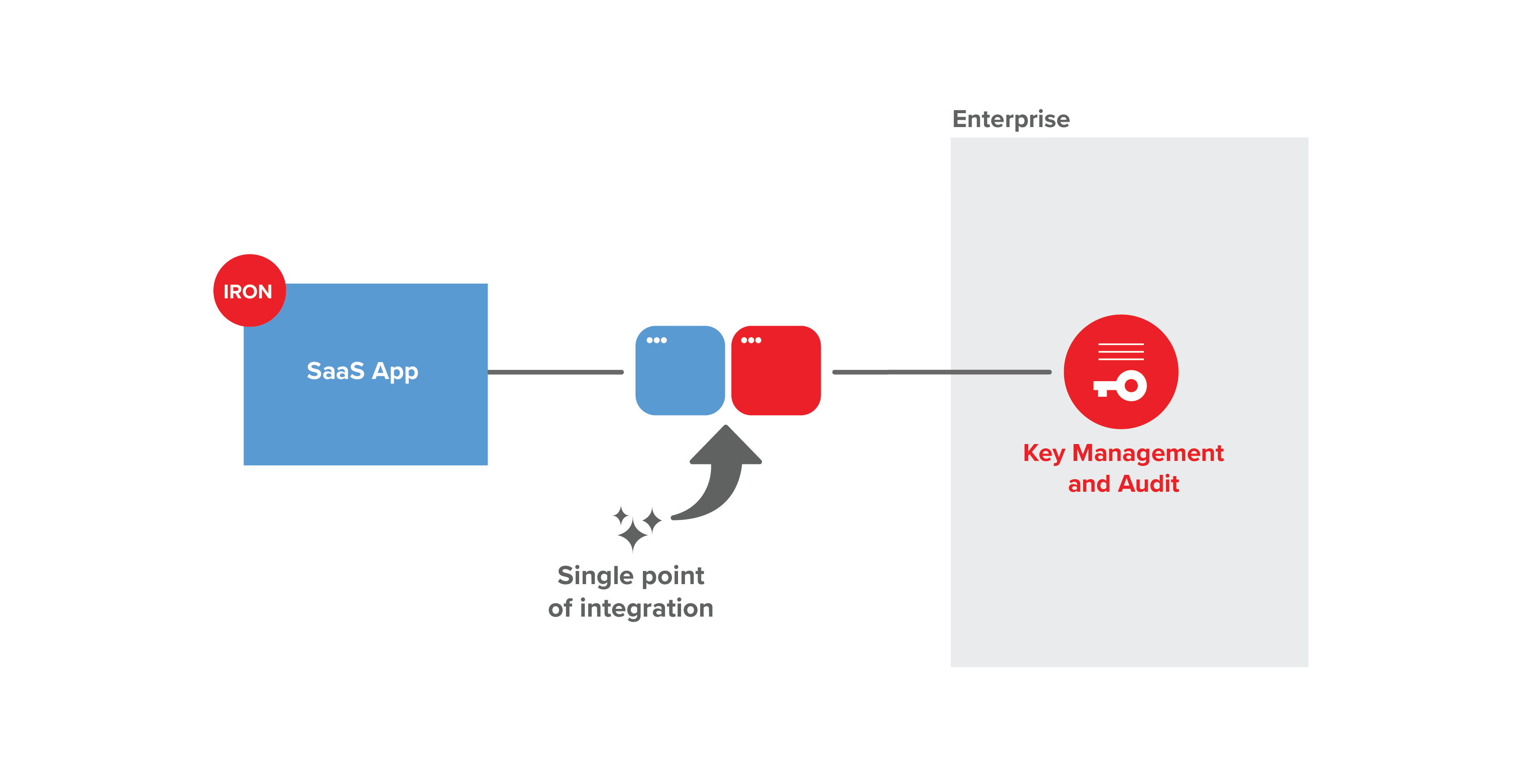
An SDK + Configuration simplifies integration.
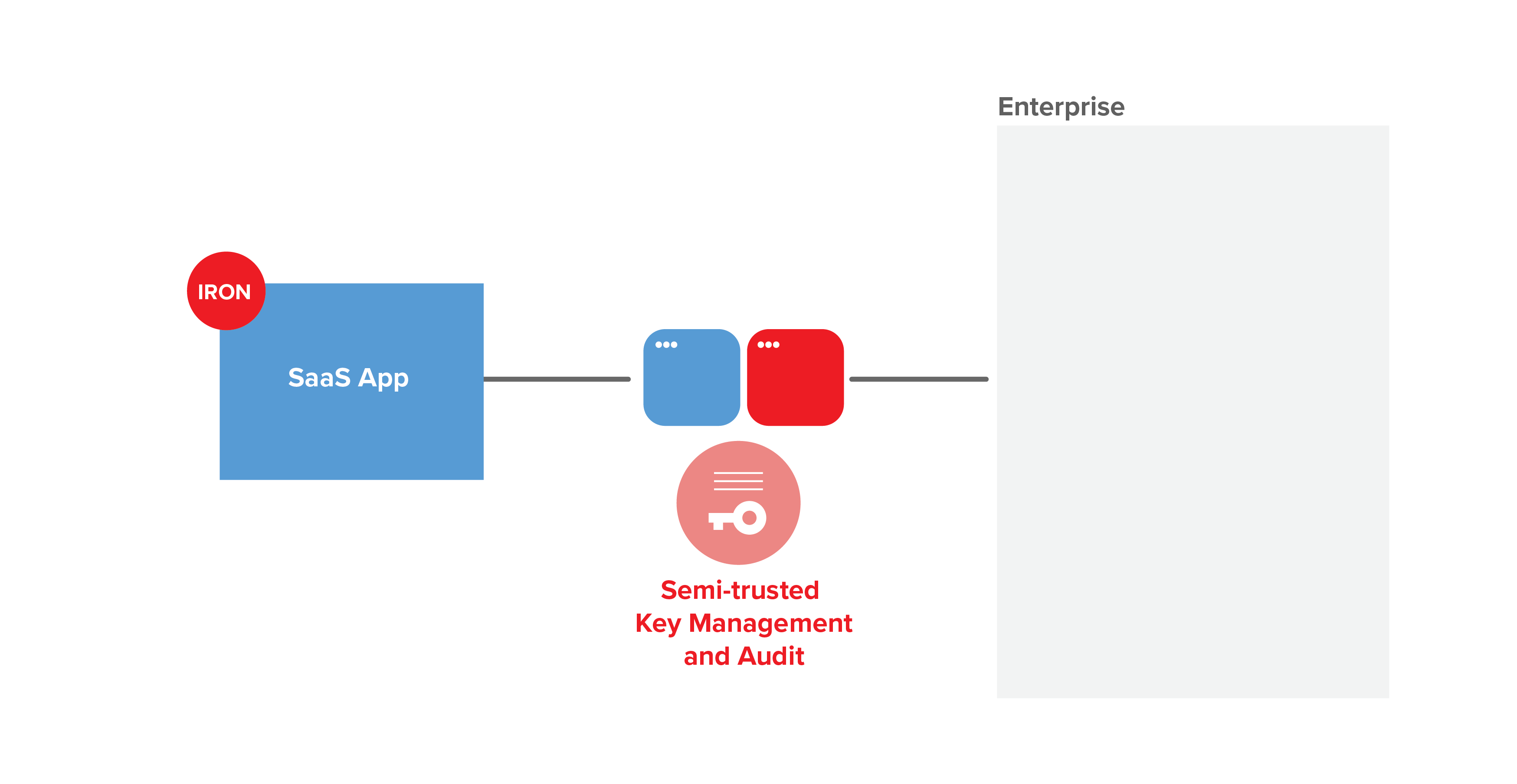
A cloud key management option lowers adoption friction.
Public cloud, private cloud and on-premises deployment options.
A Technical Path to Advanced Data Control
CMK is an effective compromise, but many CISOs prefer true end-to-end data control. One advantage of IronCMK is that the same integration can provide data control to the service or client. This is a mix-and-match proposition, with the ability to provide strong controls based on data classification and sensitivity.
IronCMK offers advanced data residency capabilities. Meaning, there is no longer a need to stand up separate in-country cloud infrastructure; as long as encryption keys stay within country, data residency requirements are met.
And IronCMK supports privacy rights as defined by the GDPR and the California Consumer Protection Act. In particular, right to transparency and right to erasure are seamlessly supported.
Summary
For many large enterprises, Customer Managed Keys are a baseline requirement for cloud software. Ad-hoc CMK implementations have high integration complexity using technologies that are unfamiliar to many SaaS product teams. IronCMK provides a streamlined approach that allows SaaS applications to ship faster with advanced data controls. Enterprises gain consolidated management of SaaS providers, with full monitoring and revocation.