- Docs
- SaaS Shield
- Integration Guides
- Thales CipherTrust Manager
Thales Integration Guide
 IronCore’s SaaS Shield product supports the use of
Thales CipherTrust Manager as the Key Management System (KMS) that
a key holder uses to manage and secure the keys used to protect customer data in the data holder’s system. CipherTrust Manager can
be run by an organization in their own computing infrastructure or in a hosted cloud service like the
Thales Cloud Key Manager.
IronCore’s SaaS Shield product supports the use of
Thales CipherTrust Manager as the Key Management System (KMS) that
a key holder uses to manage and secure the keys used to protect customer data in the data holder’s system. CipherTrust Manager can
be run by an organization in their own computing infrastructure or in a hosted cloud service like the
Thales Cloud Key Manager.
The key holder’s admins can use the following steps to configure CipherTrust Manager.
If you are an admin preparing to manage keys using SaaS Shield, you should get your instance of CipherTrust Manager ready to work with SaaS Shield, using the following steps:
Log into your CipherTrust Manager console.
We recommend that you create a new user to be used by SaaS Shield to access CipherTrust Manager. This user will be created in the current authentication domain set in the console. If you are not in the domain in which you would like to create the user, you can change the domain by clicking on the user in the top right corner, then clicking Switch Domains.
 If there is no domain displayed, you are in the default root domain. You can read more about domain management in the
Thales Documentation.
If there is no domain displayed, you are in the default root domain. You can read more about domain management in the
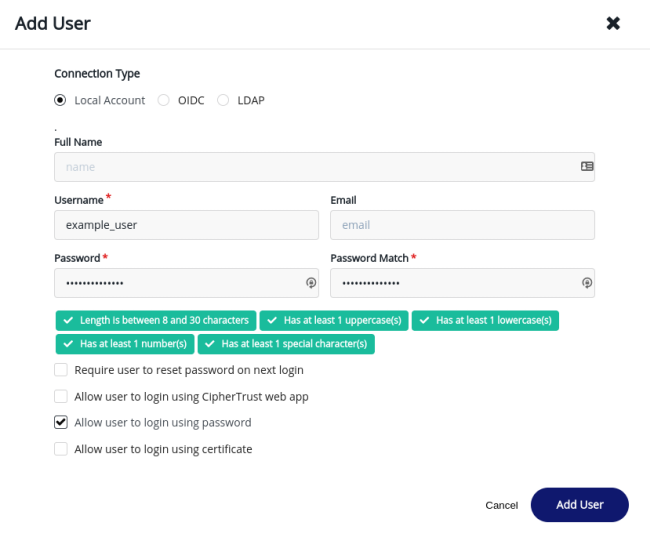
Thales Documentation.To create a user in the curent domain, navigate to the Access Management > Users page and click Add User. You must provide a username and password for the new user, but you can leave the full name and email fields blank. To increase security, we recommend only allowing the user to login using the password. Setting the user’s Connection Type to Local Account will fix the value to local_account.
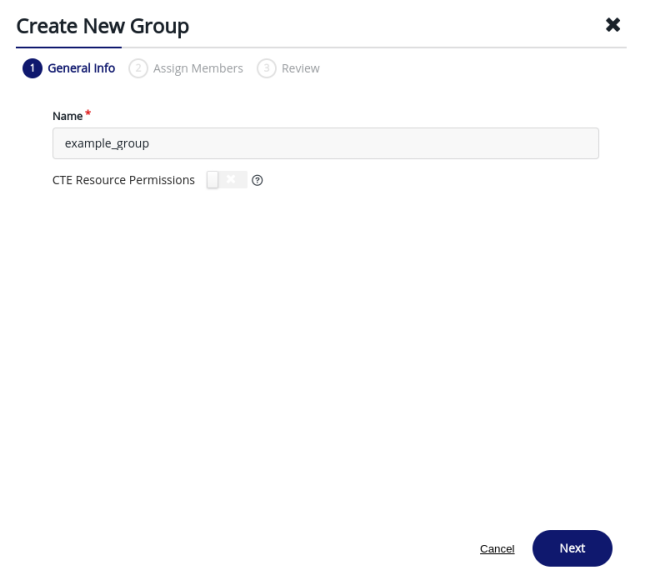
Next, we recommend creating a group to associate to the new user. From the Access Management > Groups page, click Create New Group. You must provide a name for the group.
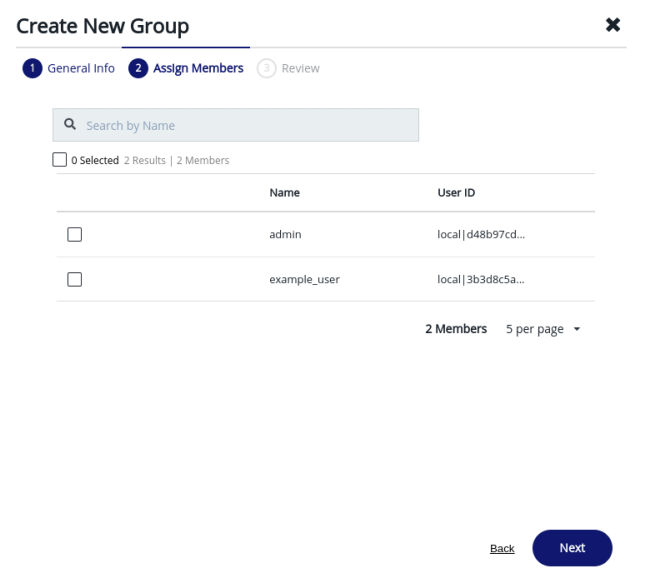
 If you click Next, you can assign the new user you created to the new
group. Locate the user’s Name or User ID in the list and check the corresponding box to assign the user to the new group.
Click Next, review the group’s name and assigned member, and click Add Group to finish.
If you click Next, you can assign the new user you created to the new
group. Locate the user’s Name or User ID in the list and check the corresponding box to assign the user to the new group.
Click Next, review the group’s name and assigned member, and click Add Group to finish.
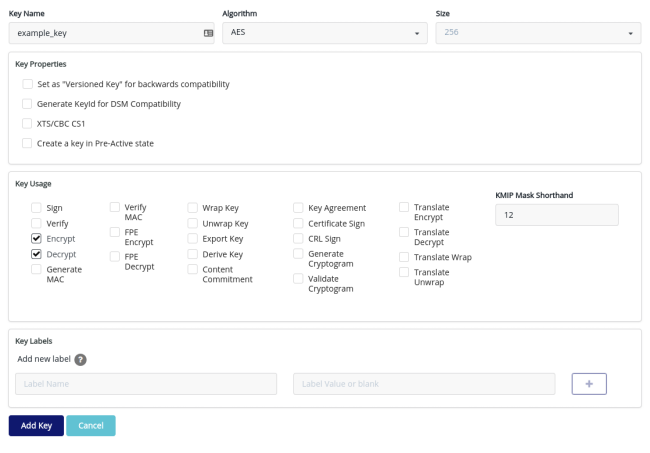
The next step is to create a key to use to protect your data in the data holder’s applications. Go to the Keys page and click Add Key. You can supply a Key Name for the key. We suggest setting the Algorithm field to AES and the Size field to 256. Under Key Usage, select KMIP Mask Shorthand of 12 - this will select the encrypt and decrypt key permissions. Click Add Key to complete this step.
Once you have created a new key, you must allow the new group to use the key. From the key’s View/Edit page, expand the Key Access section. Enable Show All Groups, then enter the group’s name into the Search Groups box. Find the new group you created, and assign it Read, Use, Encrypt, and Decrypt permissions, then click Update.
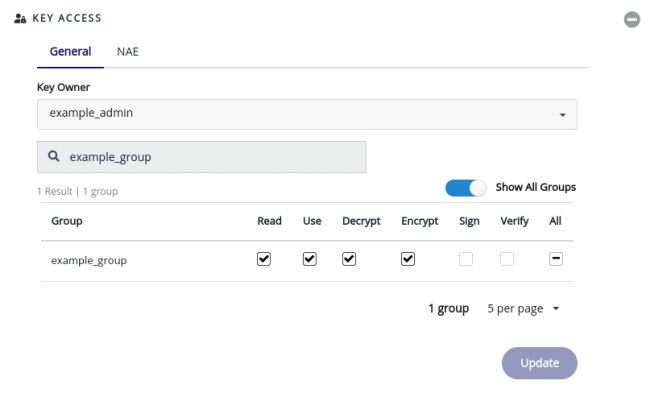
Once the key has been fully configured, copy its key ID to the clipboard - you will need it in a following step. Make sure you copy the key’s ID, rather than its name.
Now that you have a key ready in CipherTrust Manager, you can configure SaaS Shield to use the key by following these steps:
- Log into the Configuration Broker
- Select KMS Configs from the left menu
- In the Add Config box, click the Thales logo

- Enter the username of the user you created in CipherTrust Manager
- Enter that user’s password
- Enter the name of the auth domain that was in effect when you created the user (defaults to root)
- Enter the Connection - defaults to local_account
- Enter the CipherTrust Manager Service URL used to connect to the CipherTrust instance, e.g.
https://manager.ct.my.com - Paste the Key ID that you copied earlier
- Click Encrypt and Save
The information you provided is immediately encrypted in your browser, then sent to the Configuration Broker for storage and dissemination to the Tenant Security Proxies (TSPs) running in the data holder’s infrastructure. The information is encrypted to the key holder’s admins and to the TSPs, but not to the data holder’s staff, IronCore Labs staff, or random thugs on the Internet.
The TSP uses the provided information to access your CipherTrust Manager instance to wrap and unwrap the keys used to encrypt your data in the data holder’s applications. More details about the SaaS Shield architecture and how it protects data are available here.