Securing Gen-AI White Paper Download
The ultimate guide to AI security: key AI security risks, vulnerabilities and strategies for protection. 61% of companies use AI, but few secure it. This white paper covers the key AI risks being overlooked from LLMs to RAG.
White Paper Sample
Get the white paper now, for free
Chapter 01
Attack surface of Gen-AI
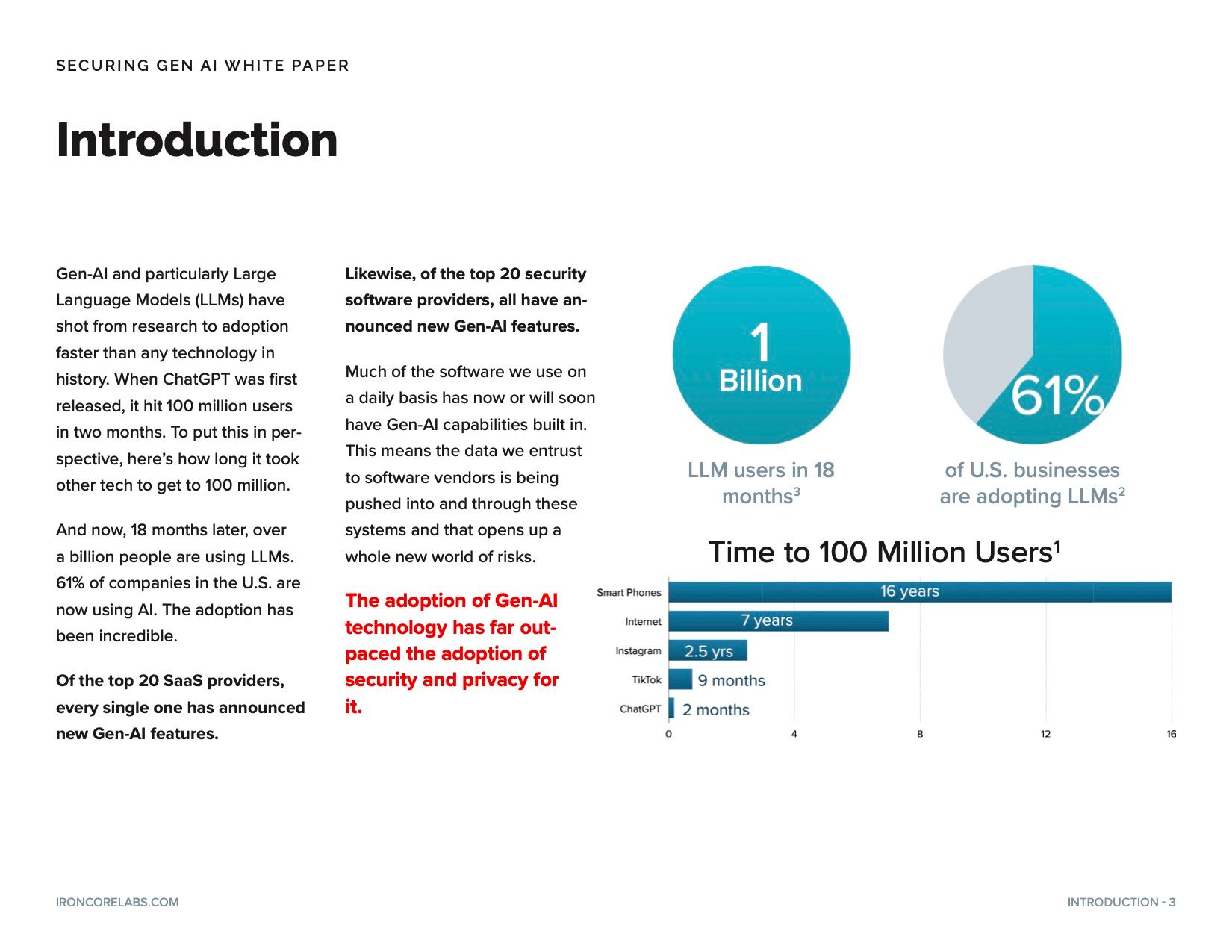
Covers where we are in handling AI security as an industry, where we have major gaps, and the dilemmas faced by security professionals as new AI features are introduced via existing vendors, new vendors, internal dev teams, and individuals.


Chapter 02
The AI ecosystem
Chapter 03
LLM-specific risks
We walk through the OWASP Top 10 giving brief descriptions of each item and addressing whether or not it concerns those who aren't making large language models since roughly half of the issues covered by OWASP are fairly specific to the big LLM producers like OpenAI and Google.


Chapter 04
RAG risks
Chapter 05
AI security solutions
Inspired by the Awesome AI Security GitHub repository, this chapter goes into detail on each type of AI security measure on the market today. It calls out the subvariants, what to look out for, how they're confused, and example vendors for each type of solution.


Chapter 06
Vendor questionnaire
Fifteen questions to help you evaluate your software vendors as they add AI features. This questionnaire will help you to assess their level of maturity in securing the data that flows through their new AI systems to help you make decisions about risk and reward and to see where data may be at risk across your infrastructure.
Chapter 07
Recommended AI security approach
This section gives opinions on the policies that security teams should set for any use of AI within their organization including, and especially focusing on the types of mitigations and security tools that should be in place before experimental AI features are working with live data in real environments.

Other Resources