Rally Software Leads the Industry in Data Privacy With Customer Managed Keys
Rally Software, an agile lifecycle management solution that is part of Broadcom, and IronCore Labs teamed up recently to present a webinar on how our two companies partnered to bring industry-leading data privacy to Rally’s customers. To watch the 30-minute webinar on-demand, click below. If you prefer to read instead of watch, the rest of this blog is for you.
Rally’s Customers Want Customer-Managed Keys
A year ago, some of Rally’s biggest customers started asking for advanced privacy features to better control their data within Rally. That’s when Rally started looking for a partner who had already built solutions to meet their customers’ demands — they found us.
IronCore Labs’ CMK solution is perfect to bring extra privacy and control to our customers. They’ve been a great partner to us.
— Michele Kubicek, Manager, Product Management, Rally Software
The IronCore Labs Customer Managed Keys (CMK) solution is part of IronCore’s larger SaaS Shield product, allowing SaaS businesses to differentiate and quickly provide their enterprise customers with advanced privacy and security features so they can keep close control of their data.
CMK Builds on Rally’s Already Aggressive Security Standards
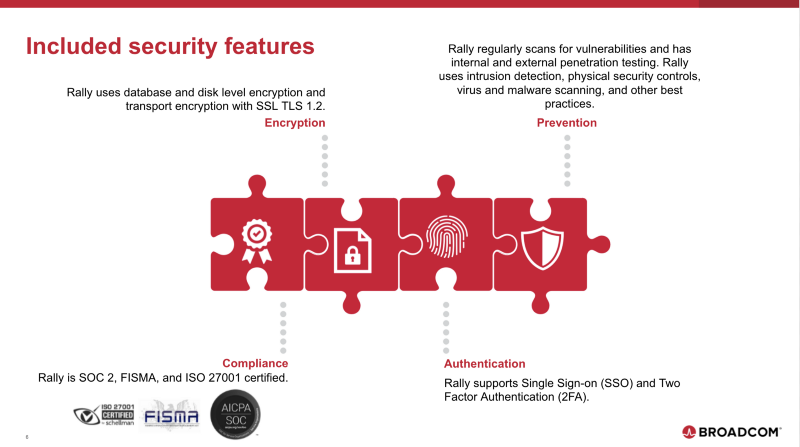
Rally offers customers a suite of security features with encryption, compliance, authentication, and prevention, which includes encryption at rest and in transit, two-factor authentication, single sign-on, and SOC 2 certification, among others. Rally’s enterprise-grade security is managed by a dedicated security team that is focused on keeping customer data safe.
But in addition to all this, Rally recognized the need for customers to increase control of their data.
We’ve found that some companies would like to retain control of their data stored within Rally and to be able to use their existing security tools to monitor, track and manage access to that data.
— Michele Kubicek, Manager, Product Management, Rally Software
Rally is the first and only ALM cloud software to offer CMK. Their approach gives customers with the CMK add-on the ability to hold their own encryption keys, view full audit trails of all access to their sensitive data, and to revoke that access.
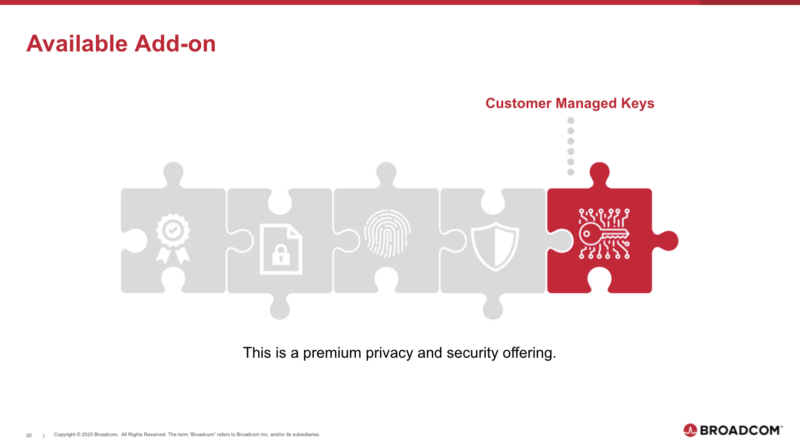
What is CMK?
CMK is a way for customers to use their existing infrastructure and policies to protect their data that’s held by partners.
Key features of CMK:
- Encrypt data with separate keys specific to each customer.
- The customers’ security team holds and manages the encryption keys. Any algorithm, key size, and rotation schedule can be used.
- The customer gets audit trails for data access that their security team can monitor with their existing event management tools.
- The customer can revoke access to data independent of Rally and even from Rally in a data emergency.
- Readily address many compliance requirements.
Rally’s CMK offering is a level above any of their competitors. Other ALM products hold encrypted customer data, but they also hold the key to decrypt it. They can look at the data at any time, which is a full-trust model.
Rally’s CMK brings a trust-but-verify model. Rally holds their customer’s encrypted data, but the customer holds the key to decrypt that data. So no one at Rally can decrypt and look at data without the customer. Customers can also revoke their key at any time, meaning they’re in full control. And they can monitor how and when that data is accessed.
How CMK Works Under the Hood
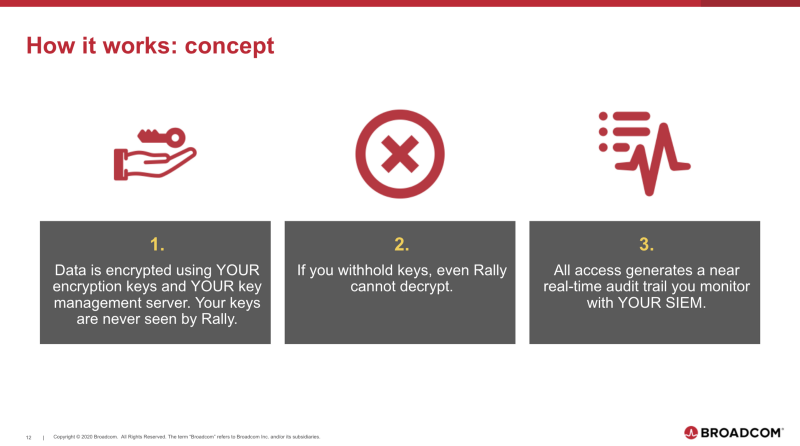
The Rally CMK offering allows customers not just to manage their own encryption keys, but to use their existing key management infrastructure and to hold their own keys.
The customer holds the keys. They decide the algorithms to use. They decide when to rotate and how best to manage and meet policies. And because they hold the keys, they can choose shut off access to them at any time. Doing this independently stops access to the sensitive data by everyone, including Rally.
And finally, Rally customers get full audit trails of data access that can be monitored by their Security Operations Center using their existing log and event management tooling.
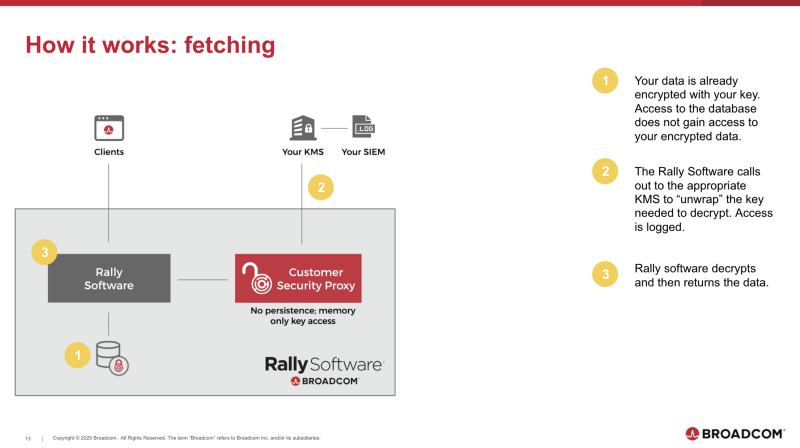
The data held in Rally’s database is encrypted with the customer’s key. Anyone with access to those storage servers still can’t see the contents of that data.
When an authorized user tries to fetch sensitive data, the Rally software fetches the encrypted data from the database, then unlocks the secure envelope surrounding the data by calling out to the customer’s key management server.
The data itself stays inside the data center and gets decrypted the rest of the way by the Rally software before being passed back to the user.
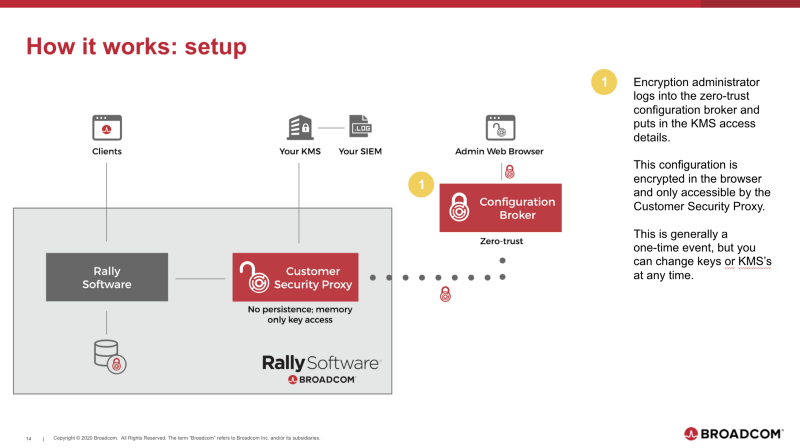
Before any of that can happen though, a security administrator needs to configure how that proxy talks to their KMS. This is done securely using the configuration broker. This configuration is different from other parts of Rally configuration because it’s encrypted in the browser before being sent to a server and stored.
Only the Tenant Security Proxy, as shown in the diagram above, and the customer’s security admins can decrypt the configuration. The setup process is generally a one-time event, but customers can log in and change KMSs or key slots as needed at any time. Actual key management and rotation are still handled by the customer’s KMS.
How Did We Get Here?
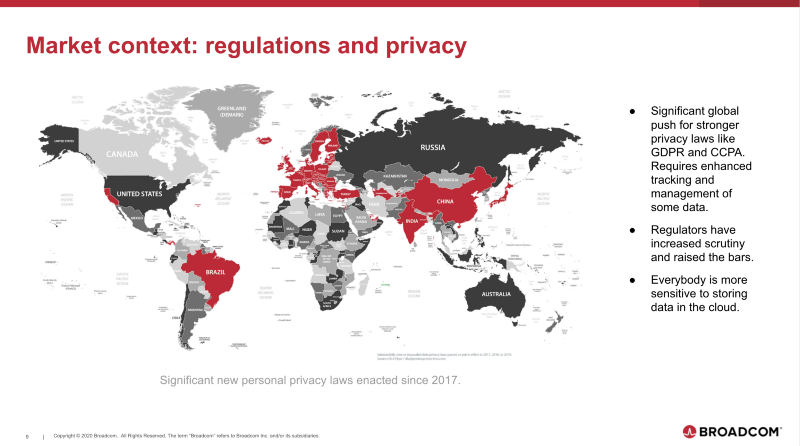
In the last five years, we’ve seen a general increase in sensitivity to storing data in the cloud. This has been fueled by news articles about companies like Facebook and Cambridge Analytica. And we’ve seen a backlash in the form of hundreds of new privacy laws around the world and increased scrutiny from regulators.
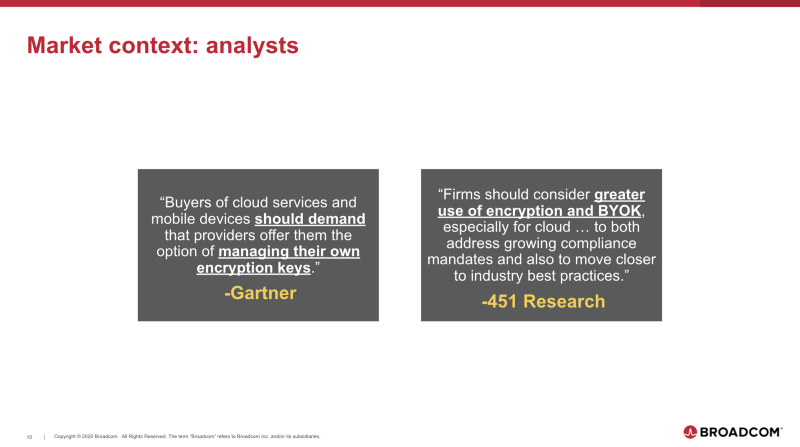
Analysts have aggressively pushed for solutions to these problems and a favorite approach is encourages companies to get control of their encryption keys — and by extension, their data.
In response to these trends and to customer requests, a few companies have risen to the challenge. Slack recently released their Enterprise Key Management feature. Salesforce has their Shield product. And now Rally joins them with their CMK offering powered by IronCore.
What’s next?
Data control is a hot topic among enterprise companies these days, and we’re continuing to see SaaS businesses turn to CMK to offer their existing customers enhanced privacy and security options. This also serves to attract larger and more data-sensitive customers and to get deals through security review cycles.
If that’s what you’re looking for, we’d love to chat. Our solution will quickly and easily integrate into your SaaS application. The do-it-yourself approach takes in-house expertise and, on average, 15 months. We can get you to market fast, help you upsell renewing accounts, win new deals, and differentiate from your competitors. Let’s talk.
$k=x^6$