Infographic: How to Get Started With Application-layer Encryption
Best practices for practical SaaS data security
We recently wrote blogs defining application-layer encryption and explaining why SaaS businesses need to be using a layered security approach. This blog is the next step to help you get started.
Application-layer encryption (ALE) is the best way to keep the data you hold safe, but there are a lot of pitfalls to doing it yourself from scratch, which is why few companies have historically used ALE. Thankfully, that’s changing as it becomes more accessible.
The ALE solutions we’ve built are made to drop-in, scale, and provide you with a huge amount of flexibility so the solution fits your business’ needs.
You choose what works for you. We’ll make it easy to get started.
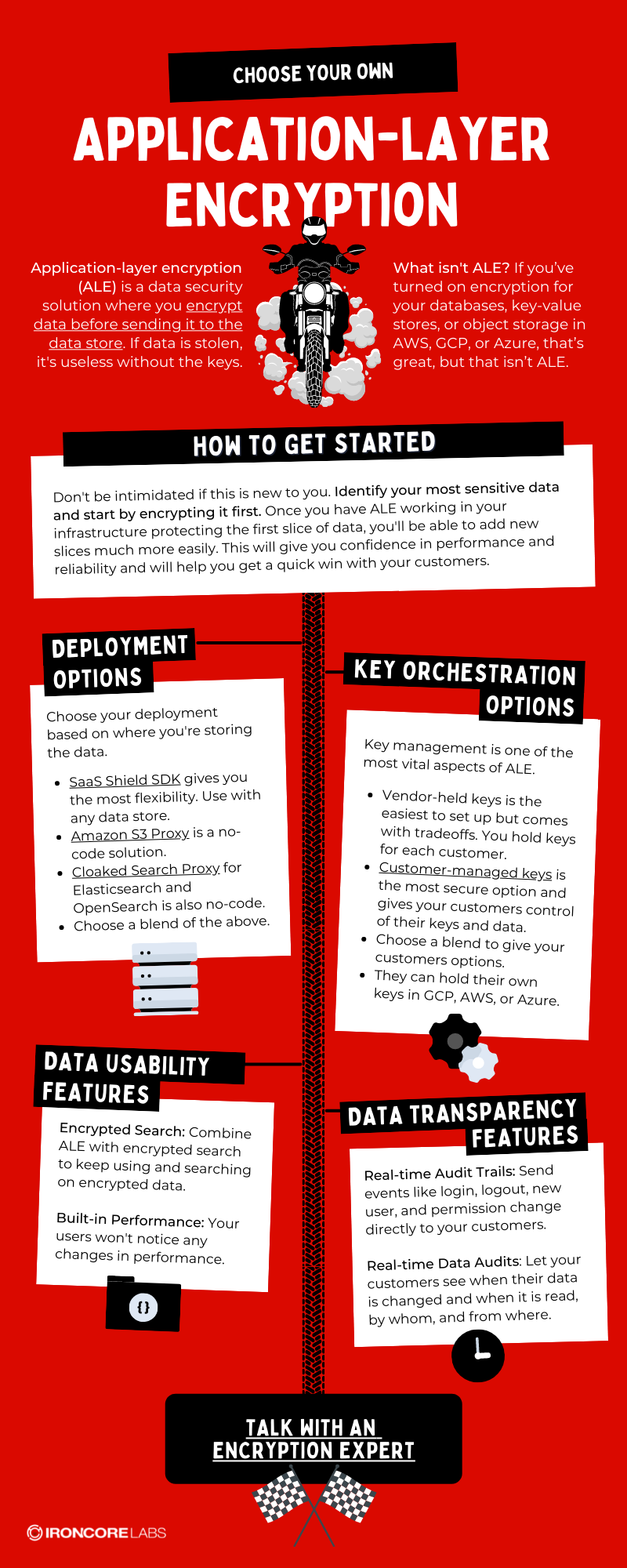
How to Get Started
Don’t be intimidated if this is new to you. Identify your most sensitive data and start by encrypting it first. Once you have ALE working in your infrastructure protecting the first slice of data, you’ll be able to add new slices much more easily. This will give you confidence in performance and reliability and will help you get a quick win with your customers.
Deployment Options
Choose your deployment based on where you’re storing the data.
- SaaS Shield SDK gives you the most flexibility. Use it with any data store.
- Amazon S3 Proxy is a no-code solution.
- Cloaked Search Proxy for Elasticsearch and OpenSearch is also no-code.
- Choose a blend of the above.
Key Orchestration Options
Key management is one of the most vital aspects of ALE.
- Vendor-held keys is the easiest to set up but comes with tradeoffs. You hold keys for each customer.
- Customer-managed keys is the most secure option and gives your customers control of their keys and data.
- Choose a blend to give your customers options.
- They can hold their own keys in GCP, AWS, Azure, or Thales.
Data Usability Features
Encrypted Search: Combine ALE with encrypted search to keep using and searching on encrypted data.
Built-in Performance: Your users won’t notice any changes in performance.
Data Transparency Features
Real-time Audit Trails: Send events like login, logout, new user, and permission change directly to your customers.
Real-time Data Audits: Let your customers see when their data is changed and when it is read, by whom, and from where.
Talk With An Expert
Talk with one of our application-layer encryption experts today. We offer a free consultation to all new customers.




