- Docs
- Data Control Platform
- Further Reading
- Data Control
Data Control
Security and/or privacy concerns continue to be the top inhibitors to public cloud adoption.
- Gartner
If your product is sold to security sensitive industries like finance or healthcare (or increasingly to any industry), you know that large companies demand extensive information security reviews, with lengthy spreadsheets. In many cases, companies decide not to purchase a service that might otherwise make them more competitive. IronCore believes that the root cause of long review cycles is data control, or the perceived lack of it.
Data control is the ability for data owners to know how their data is being used and by whom and to be able to independently revoke access, even from cloud service providers, at any time.
Who is a data owner and what do we mean by knowing how data is being accessed and independently revoking access?
Imagine you grant your doctor access to your medical records. You notice that your doctor is sharing your data with insurance firms, billing companies and outside research institutions. You decide that you are not comfortable with this sharing, so you click a button and instantly revoke access. You are the data owner in this scenario. Your doctor is your service provider. The insurance, billing and outside research institutions are third-party providers. Monitoring is your ability to always see who data is being shared with and how and when they use it. Revocation is your ability to click a button and instantly erase your data from those systems.
Now imagine that you offer this capability to your customers. As data owners, they would have data control - the ability to monitor how their data is being used and by whom and to independently revoke access at any time. Data control is mathematically provable - built into the underlying cryptography. It is not dependent on application software with its inevitable flaws.
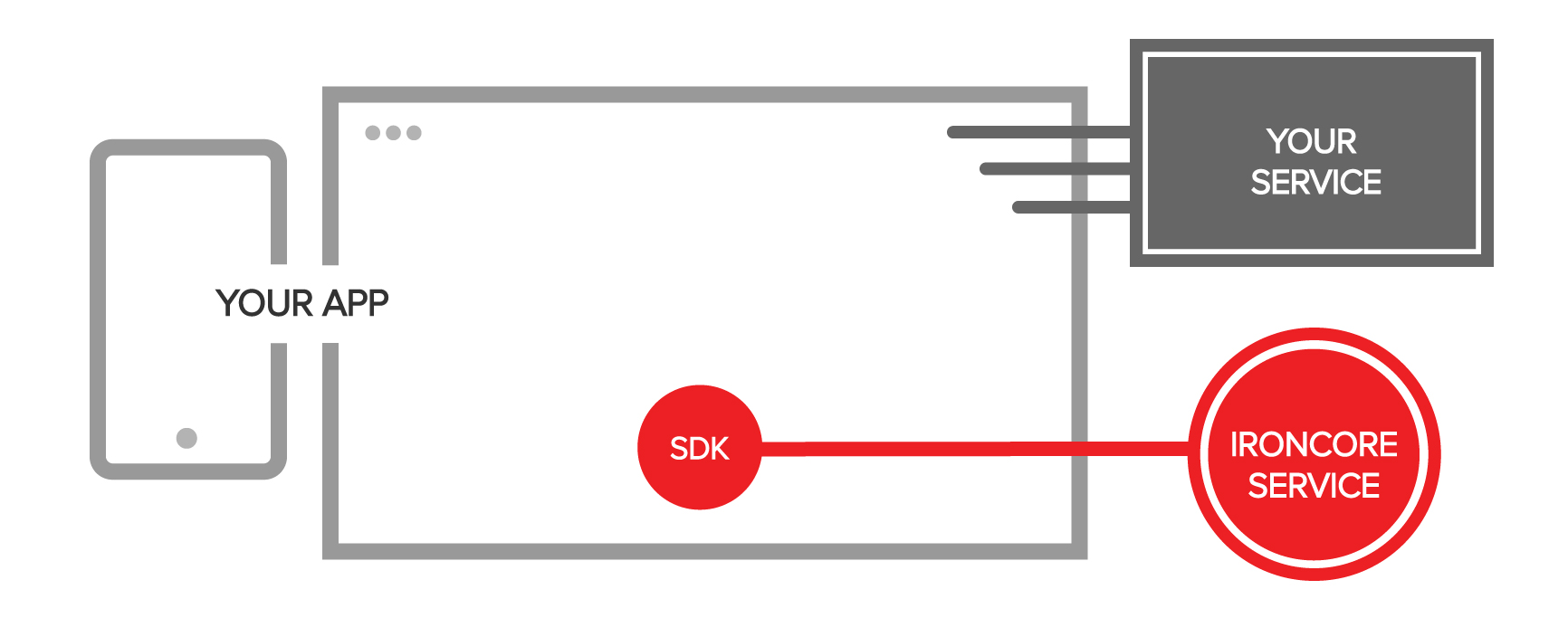
IronCore adds privacy and security to your application
So how does this work? In transform encryption, encrypted data must be transformed before it can be decrypted. You embed an SDK into your application that communicates with the IronCore service. The IronCore service manages the transform keys that convert group ciphertext to member ciphertext. Monitoring is straightforward, as IronCore logs every access and every transform. Revocation is also straightforward and is achieved by deleting the transform key that links a group to a specific member.
No longer do data owners need to literally hand over the keys to their most valuable resource. Any piece of data can only be read by users and services who are authorized to unlock it, with no risk of breach by someone who exploits a bug, hacks a database, or steals a password. Data owners know exactly how their data is being used and by whom, and they can revoke that access, even from their vendor, at any time. This is Data Control.