- Docs
- Data Control Platform
- Further Reading
- Envelope Encryption
Envelope Encryption
Envelope encryption is a technique that combines symmetric and asymmetric encryption to improve performance.
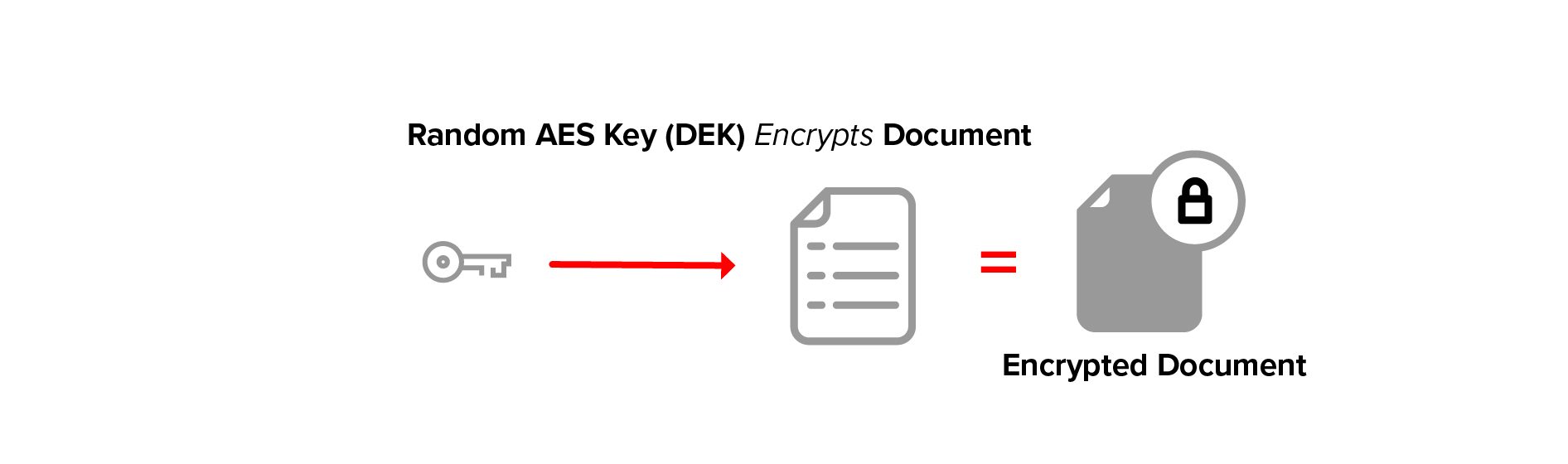
A key value suitable for use with a symmetric encryption algorithm such as AES is chosen randomly, then it is used to encrypt plaintext. This plaintext is referred to as the document, and the key is called the document encryption key (DEK).
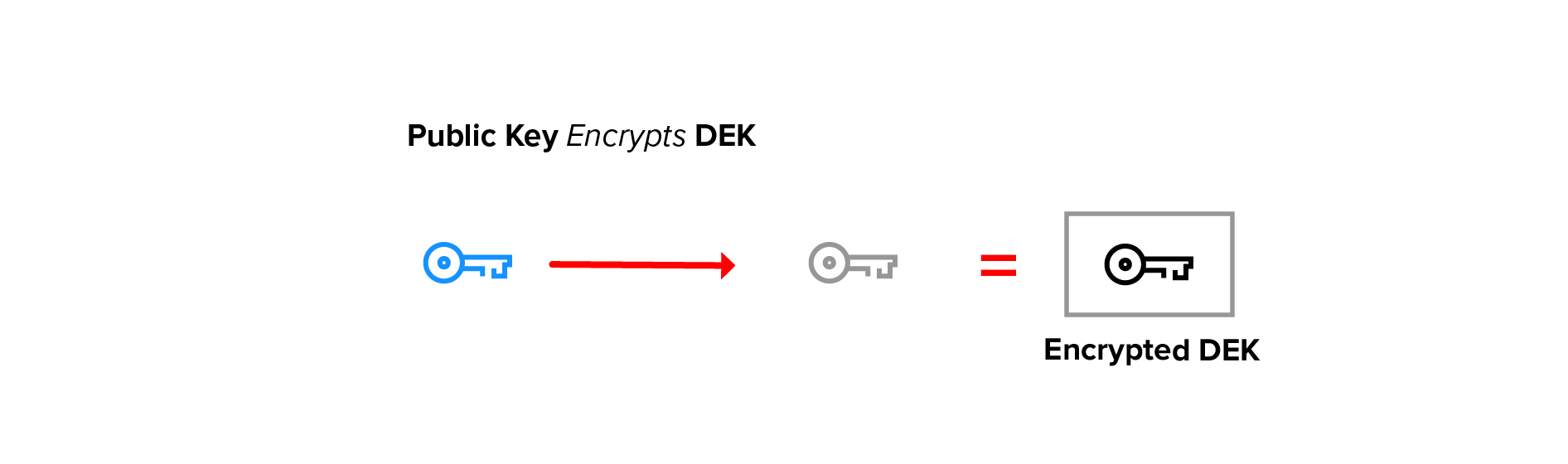
The DEK itself is then asymmetrically encrypted with a user’s public key. The resulting encrypted DEK can be stored with the data or elsewhere.
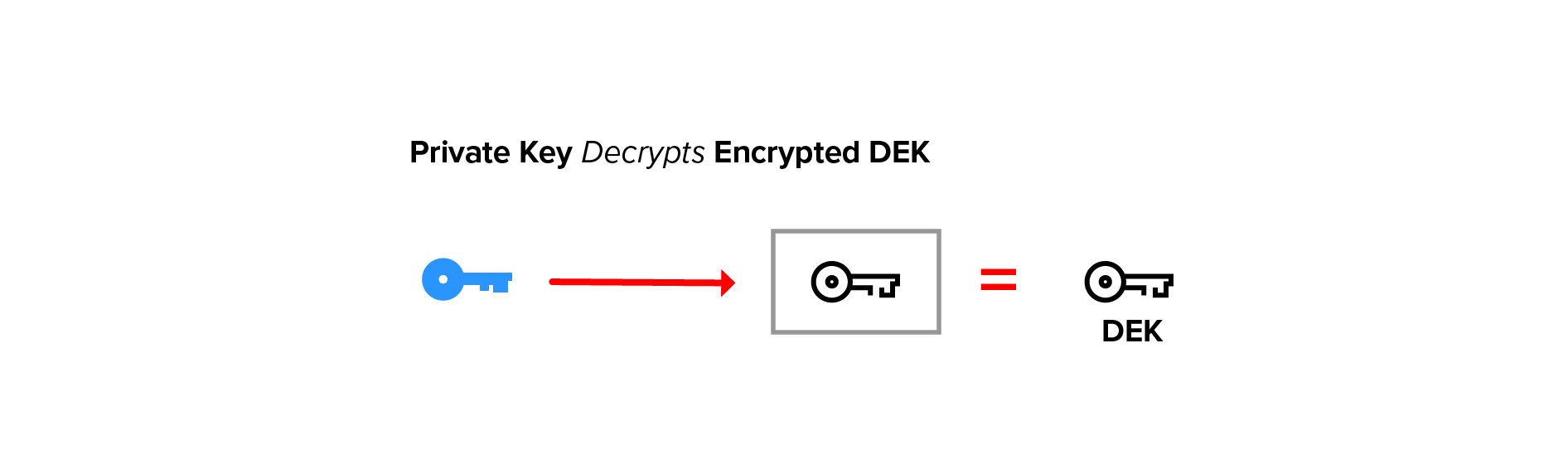
To recover the document the encrypted DEK is first decrypted using the user’s private key.
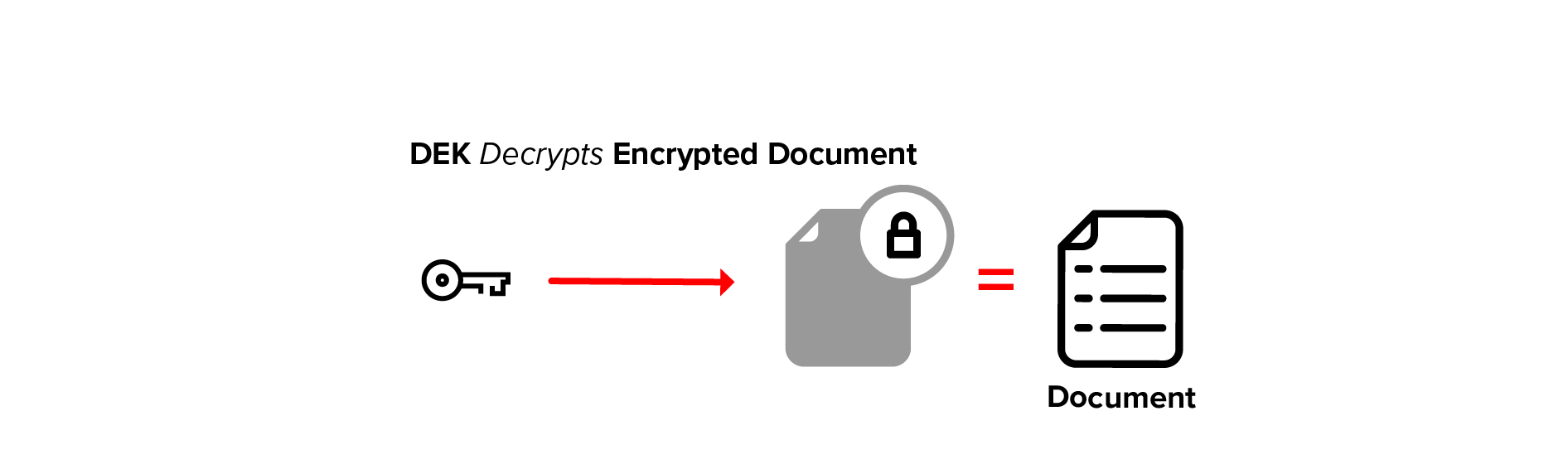
Once the DEK is recovered, it can be used to decrypt the underlying document data.
Glossary terms:
Symmetric Encryption
Symmetric encryption uses one key for both encryption and decryption. It is fast and very secure. The main drawback is that the encrypter of the data and each user that should be allowed to decrypt must find a way to share the symmetric key securely.
Asymmetric Encryption
Asymmetric encryption uses two keys that are mathematically related (generally called a key pair). Plaintext or document data is encrypted using the public key, and the resulting ciphertext is decrypted using the corresponding private key.
Public Key Encryption
Public key encryption is another name for asymmetric encryption. It is called public key cryptography because the encryption key can be shared publicly, while the decryption key must be kept private.