- Docs
- Data Control Platform
- Further Reading
- Orthogonal Access
Cryptographic Orthogonal Access Control
All problems in computer science can be solved by another level of indirection.
- David Wheeler
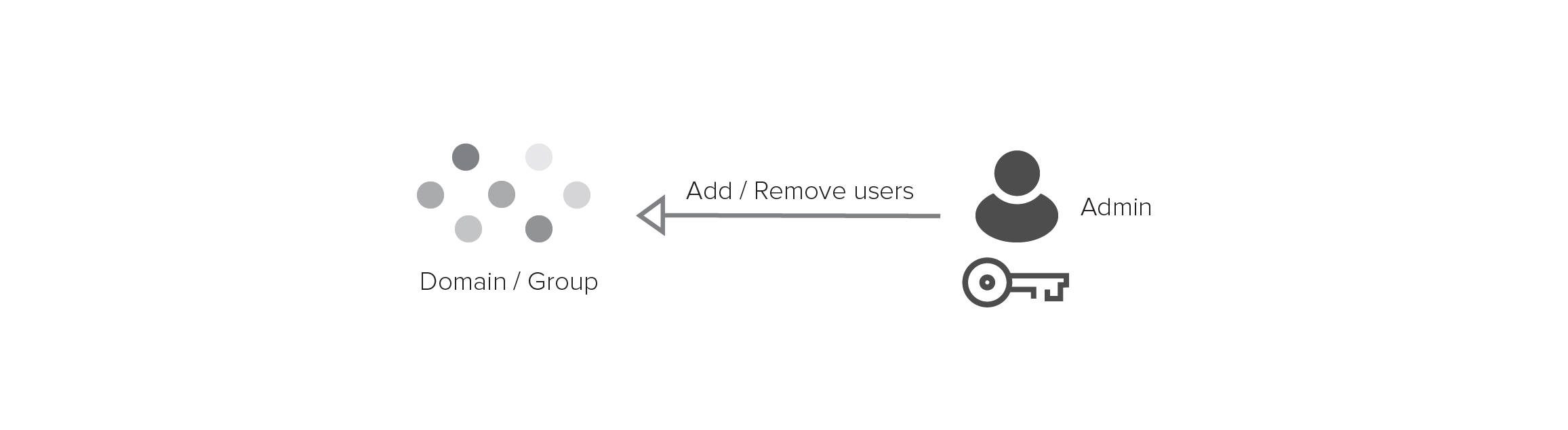
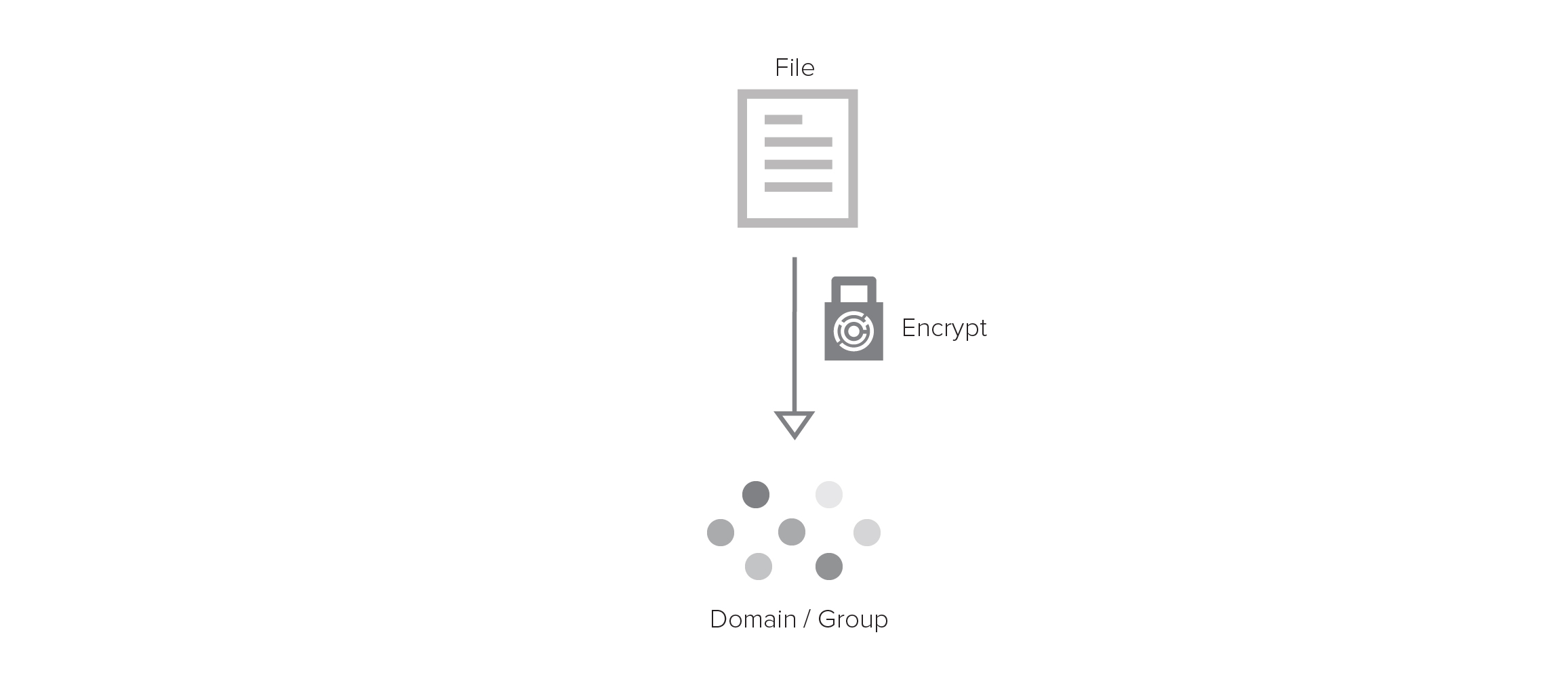
With orthogonal access control, your decision of who to encrypt to is separate from your choice of who can decrypt. You abstract classes of users and services into groups and then encrypt data to the group. At any point in time, you specify who is currently a member of the group. Only the group members’ private keys can unlock data encrypted to the group.
You encrypt data to a group.
You can add or remove group members at any time, without changing encrypted data. Groups can be any size, even millions of users, and adding and removing members are constant time operations regardless of how many documents or users there are. There is no need for shared secrets or trusted servers.
Example
The Starship Enterprise has a sickbay to provide healthcare services to crewmembers. Starfleet regulations require that any personal health information (PHI) be restricted only to onboard medical personnel. The Starship Enterprise team uses transform encryption as follows:
Step 1
Dr. McCoy creates a PHI-Readers cryptographic group.
Step 2
Dr. McCoy encrypts PHI and intake records to the group.
Step 3
Dr. McCoy adds Nurse Chapel as a member of the PHI-Readers group.
Step 4
Various biomedical scanners read and create PHI records. These scanners detect blood anomalies, look for viruses, etc. Dr. McCoy adds the service accounts for the scanners as members of the PHI-Readers group.
Step 5
As medical staff join and leave, group membership is modified. The decision of what data to decrypt is separate from the choice of who can decrypt.