Resource Center
Videos
AI Is Eating Your Data: Here's The Privacy Tech Fighting Back
Your vendors can read your data. That means hackers and governments can too. This video explains the three biggest risks to data privacy today — security failures, government access, and the AI data pipeline — and introduces encrypted search, a privacy-enhancing technology that lets applications search and operate on data they can't decrypt. We cover how vector embeddings can be reversed, why 'encrypted at rest' isn't enough, and what businesses should require from their technology providers.
Newsletters
AI is killing Data Privacy Day (or privacy, anyway)
We've drawn a clear engineering "line in the sand" for AI use. Here's the policy, the why behind it, and what we're refusing to trade for AI speed.

Blogs
AI Coding Agents: Our Privacy Line in the Sand
How IronCore draws the line on AI coding agents: our policies for protecting customer data, secrets, and source code while still leveraging AI's power.
Newsletters
A Year-End Reflection on Security, Advocacy, and Human Error
You can’t eliminate mistakes, but you can design for them. What 10 billion exposed records taught us about "fast vs. correct."

Blogs
One Unchecked Box, One Billion Records: The Human Error Problem
One unchecked authentication box exposed 1 billion Chinese police records. Studies show human error is rising as a cause of breaches. Here's how you can survive mistakes.

Videos
OWASP Global - Hidden Risks of Integrating AI
This talk explores the hidden risks in apps leveraging modern AI systems—especially those using large language models (LLMs) and retrieval-augmented generation (RAG) workflows and demonstrates how sensitive data can be extracted through real-world attacks. It touchpoints back to OWASP principles and the LLM Top 10 while demonstrating attacks for extracting data and for abusing MCP servers and agents.

Blogs
Illuminating the Dark Corners of AI (annotated presentation)
Full annotated transcript of my DEF CON 33 presentation on exploiting shadow data in AI models and embeddings. Learn how attackers extract training data, system prompts, and private information from vectors, plus practical defenses.

Videos
LASCon - Hidden Risks of Integrating AI
This talk explores the hidden risks in apps leveraging modern AI systems—especially those using large language models (LLMs) and retrieval-augmented generation (RAG) workflows and demonstrates how sensitive data can be extracted through real-world attacks. It touchpoints back to OWASP principles and the LLM Top 10 while demonstrating attacks for extracting data and for abusing MCP servers and agents.
Newsletters
Planning for 2026? Here's some food for thought...
Some thoughts on planning for a year when AI and security intersect more deeply and data is more at risk than ever before.

Blogs
MCP Servers Are Electric
MCP servers promise magic, but one prompt can blow up your GitHub, Salesforce, or entire stack. Here's why LLM integrations are far more dangerous than vendors admit.
Newsletters
Building AI That Respects Data Privacy
Every customer says the same thing: don’t train on our data; plus attack demos, new videos, and how to use privacy-preserving AI.

Blogs
Privacy-Preserving AI: The Secret to Unlocking Enterprise Trust
Enterprises are blocking vendors from training AI on their private data. Learn how privacy-preserving tech like encrypted models can restore trust, win deals, and enable AI features.
Videos
DEF CON 33 - Exploiting Shadow Data in AI Models and Embeddings
This talk explores the hidden risks in apps leveraging modern AI systems — especially those using large language models (LLMs) and retrieval-augmented generation (RAG) workflows — and demonstrates how sensitive data, such as personally identifiable information (PII) and social security numbers, can be extracted through real-world attacks. We demonstrate model inversion attacks targeting fine-tuned models and embedding inversion attacks on vector databases, among others.
Newsletters
From AI Rush to AI Reality: Why Enterprises Are Hitting Pause
AI adoption has shifted from hype to hesitation—here’s how to move forward securely

Blogs
The Terrifying Takeaways from the Massive OAuth Breach
Massive Salesforce, Google & Salesloft hacks expose OAuth risks. Learn why tokens are dangerous and how SaaS vendors are screwing up security.

Blogs
IronCore Named a 'Cool Vendor in Data Security' by Gartner
IronCore Labs is a Gartner Cool Vendor in Data Security 2025 for its ability to encrypt large amounts of AI data.

Press Releases
IronCore Labs Named a Gartner® Cool Vendor in Data Security 2025
IronCore Labs named a 2025 Gartner Cool Vendor for pioneering data security for AI systems.
Newsletters
Hackers, CISOs, and GenAI: What Everyone's Asking About
Lessons from DEF CON and the AI Risk Summit; new trends with large financial companies; and new conference dates.

Blogs
The Rapid Evolution of Bank-Grade SaaS Security
Financial institutions are demanding SaaS vendors adopt application-layer encryption and hold-your-own-key solutions. Here's what's driving the increase in pressure.
Newsletters
The Age of AI Breaches Has Begun (and we have the stats to prove it)
New stats on AI breaches are dismal and only just beginning; new blog explains why; plus a bunch of upcoming conference talks and other news.

Blogs
When Randomness Backfires: Security Risks in AI
LLMs produce different results every time and sometimes those results are outliers that can be used by hackers to exploit systems.

Press Releases
IronCore Labs Announces Breakthrough with Cloaked AI: Encrypted Training Data Makes AI Models Safe and Private
IronCore Labs’ Cloaked AI now encrypts training data and models, ensuring AI privacy and security of production AI systems.

Explainers
Training AI Without Leaking Data White Paper
Learn how to train AI on sensitive data without compromising privacy. This paper introduces one-way vector encryption as a practical technique for securing training data and the models built on that data. This paper explains how it works, when to use it, and why it’s a powerful tool for building privacy-first AI systems.
Newsletters
The AI Privacy Dumpster Fire Rages On 🔥
Meta’s AI is leaking user prompts, we’re talking encryption standards, and Defcon is around the corner.

Blogs
Vector Encryption, AI, and the Slow Pace of Standards
Why DCPE may be the best option for securing AI data while NIST standards for privacy-preserving encryption remain years away.
Newsletters
Hacking AI data and lamenting the lack of security resiliency
New content, new talks, and new thoughts on security, encryption, and hacking AI.

Blogs
Breaches Happen — But Data Theft Shouldn't
Major breaches expose the data of millions of people and all due to single failure points and a lack of security in depth.
Newsletters
ALE for training models plus Q's for AI vendors at RSA
Tips for evaluating AI features in security products at RSA, upcoming events, and a new blog on protecting AI models with private data.

Blogs
Training AI Without Leaking Data
Learn how to protect sensitive data in AI training by using encrypted vector embeddings. This blog explores privacy risks in AI and presents secure methods like approximate-distance-comparison-preserving encryption to enable private, efficient machine learning without exposing personal or business information.
Newsletters
Mandates for ALE and the proliferation of AI gremlins
We have a new white paper on AI shadow data and a new blog on PCIv4 data security requirements. This newsletter talks about the new content and the gremlins lurking in AI systems.

Blogs
PCI v4 Now Mandates Application-layer Encryption
What's new in PCI v4 and what it means for protecting account holder data. Dives into the specific requirements and suggestions as well as the extra requirements directed at multi-tenant SaaS companies.

Explainers
AI Shadow Data White Paper
There are three major areas of untracked and unprotected shadow data in AI systems where copies of sensitive data accrue. Learn about the areas of AI shadow data and how to manage them.

Blogs
AI Security Risks Are Real -- Here's 12 Questions to Ask Your Software Vendor
Before trusting vendor's new AI feature, ask these 12 critical security questions to protect your data, prevent breaches, and ensure compliance.
Newsletters
Making adoption of AI features easier for security teams
We've released new content aimed to help security teams who are handling internal AI rollouts and enablement of external AI features.

Blogs
10 Essential Security Steps Before Launching Your AI Feature
Stay ahead of threats like prompt injections, data leaks, and model manipulation with proactive measures every company should take before rolling out AI features.
Newsletters
New year; new OWASP LLM Top 10
The new OWASP LLM Top 10 covers security risks with RAG workflows and vector embeddings, among other things; it's worth checking out.

Blogs
OWASP's Updated Top 10 LLM Includes Vector and Embedding Weaknesses
OWASP released their second version of the Top 10 for LLM Applications, and it now includes vector and embedding weaknesses among other major new issues that go beyond the LLM model itself

Videos
Vector Encryption Mini Explainer
Quick discussion of AI security problems focused on vector inversion attacks (see new OWASP LLM Top 10 #8), how they work, what can go wrong, and how to use encryption to stop them.

Blogs
Privacy Guide to Apple Intelligence with ChatGPT
Apple has done a lot to preserve privacy when you use their AI, but all of their privacy promises evaporate when you use Apple's ChatGPT integration.
Newsletters
Data privacy tips for every stocking
We've started a new blog series perfect for the new year with tips on how to protect personal data and communications in this era of non-stop breaches.

Blogs
Private Communications for Email and Text Messages
A checklist of things to do to better protect the privacy of your emails and text messages as a guard against hackers, surveillance capitalism, and overreaching and authoritarian governments.

Blogs
Identity Theft Protection Checklist
A privacy checklist series covering what people should do to keep themselves safe online. This first part covers steps to take to prevent identity theft.
Newsletters
ALE encryption decisions: here there be dragons!
From MySQL to DIY ALE systems, we go deep on what not to do. Plus our Defcon talk on AI encryption is now live.

Blogs
Build Your Own Application-Layer Encryption?
A discussion of how to design a system to use application-layer encryption and the non-obvious considerations that add complexity

Blogs
Using MySQL's Built-in Encryption: A Terrible Idea
6 reasons to avoid MySQL's native encryption functions from bad cryptographic choices to terrible side effects, we explain why you should think twice.

Blogs
Application-layer Encryption (ALE) Demo Using a Notes App
We walk through a demo using a notes app clone that's normal on the front end, but entirely encrypted in the backend including search and AI chat functionality.
Newsletters
Fresh encryption demos and how to talk to the business about AI risks
We made something of an Evernote clone where all the notes are encrypted, search over the notes is encrypted, note attachments are encrypted, and even the AI is encrypted.

Videos
DEF CON 32 - Attacks on GenAI data & using vector encryption to stop them
As the adoption of GenAI tools has soared, security has done little to keep up. New classes of data, and especially vector data, is flooding into new and untested data stores. Vector databases are getting copies of health data, financial data, HR data, emails, and everything else, but they have no intrinsic security. What's worse, the vectors themselves can be reversed in embedding inversion attacks that turn those vectors back into faces, sentences, and even pictures. We discuss these new attacks and a new branch of cryptography, vector encryption, which allows for privacy preserving searches to happen over the encrypted vectors.

Explainers
Securing Gen-AI White Paper
The ultimate guide to AI security: key AI security risks, vulnerabilities and strategies for protection. 61% of companies use AI, but few secure it. This white paper covers the key AI risks being overlooked from LLMs to RAG.

Blogs
How To Talk To The Business About AI Security Risks
Get budget to secure your AI systems and drive conversations with your vendors before AI insecurity bites you and your company.

Videos
SaaS Shield Application-layer Encryption Demo
In this video we walk through a toy app that is an evernote clone showing how such an app can make heavy use of application-layer encryption without changing any part of the experience for the user. We demonstrate ALE in SQL, in search, in S3, and in AI.

Videos
OpenSearch Unconference Talk: Bob Wall – Securing Hybrid Search
Bob discusses the why and how of securing hybrid search where search results come from a blend of vector search (semantic search) and classic keyword search.

Videos
OpenSearch Unconference Talk: Patrick Walsh – Attacks on AI Search
Patrick talks about attacks on AI search, how AI is a magnet for copies of data, how that data can be extracted from search engines like OpenSearch, and what to do about it.
Newsletters
New blog, new white paper, and we'll be in SF later this month
Just back from Defcon and we're releasing a huge new white paper plus we just published a new blog on preventing insider access to data using ALE.

Blogs
Using Application-Layer Encryption to Restrict Insider Access
SaaS companies are often asked whether their employees, like their database admins, can see customer data. The answer is almost always yes. But it doesn't have to be. ALE provides stronger security guarantees.
Newsletters
Sometimes security solutions are the problem, how ALE would have saved Snowflake customers, and upcoming conferences
It isn't just CrowdStrike causing problems. In the last year, several major security vendors have been the cause of breaches. And with AI, this is getting worse.

Press Releases
IronCore Labs Named to "Awesome Security Solutions for AI Systems" List
The list curates the companies that are innovating and leading in the emerging area of security for AI systems including Gen AI, LLMs, and RAG systems. IronCore Labs was recognized in the Encryption and Data Protection category.

Blogs
Snowflake and AT&T Breaches Were Preventable With Application-layer Encryption
The attacks on Snowflake and the recent successful attack on AT&T customers via their Snowflake data lake shows yet again how major enterprises are failing to secure the data they hold and why application-layer encryption and security by default are so very important, though so often overlooked.

Videos
RMISC 2024 - Exploitable Weaknesss in Gen AI Workflows: From RAG to Riches
This presentation was delivered at the Rocky Mountain Information Security Conference (RMISC) in June 2024, but the talk was not recorded. This session will demonstrate attacks on the "memory of AI," vector databases, which are used in countless ways from RAG to facial recognition to medical diagnoses. The AI data is a treasure trove for attackers. We'll end by showing how to mitigate these completely new attacks.

Blogs
Analysis of Apple's New AI Private Compute Cloud
Apple announced they're adding OpenAI support to their devices, but they're going to run the large language models in a privacy-preserving way. We analyze their approach and break it down.
Newsletters
Application-layer encryption, the GenAI security tech stack, and upcoming conferences
We've researched the many vendors now offering GenAI security, compiled them, sorted them, and made it easy for you to understand what you need.

Blogs
Securing AI: The Stack You Need to Protect Your GenAI Systems
We explore the different vendors that are producing solutions for GenAI security, group them into categories, look at which categories are necessary and when, and make recommendations on a professional, enterprise-grade secure AI stack.

Blogs
The Encrypted Messenger Wars
The Telegram vs. Signal debate is a smokescreen for what really matters and while there's a clear winner in the debate, the thrown accusations are a losing proposition for us all.

Explainers
BYOK Infographic eBook
This visual explainer covers the key concepts around Bring Your Own Key (BYOK) functionality using visual infographics for audiences of all technical levels. Note: requires contact info to download.
Newsletters
Pitfalls with BYOK and the latest on AI data protection
BYOK is getting more popular, but there's a confusion of approaches and some are better than others. And AI infra maturity is... lacking.

Blogs
Testing End-to-End Encryption Claims
Claiming end-to-end encryption is becoming commonplace, fortunately testing claims can be easy.

Blogs
5 Things SaaS Companies Get Wrong with BYOK
BYOK or Bring Your Own Encryption gets interpreted in many different ways and delivered to customers many more ways yet. There are five ways that software providers often get it wrong when delivering BYOK to their customers.
Explainers
Qdrant: A vector database security assessment
A look at the Qdrant vector database from a privacy, security, and risk management perspective.
Newsletters
Security risks with RAG architectures
RAG is all the rage, but how do you make it secure? We delve in across video, blogs, and explainer pages.

Explainers
Pinecone: A vector database security assessment
A look at the Pinecone vector database from a privacy, security, and risk management perspective.

Explainers
Security Risks with RAG Architectures
There are huge risks with the RAG architectures used to power today's AI chat bots so they can safely work over private and up-to-date data. These risks can easily become a security and privacy nightmare to those who don't build with security-by-design.

Videos
ISSA: Cybersecurity considerations for AI: comparing U.S. and EU approaches
This is a recording of an ISSA webinar where IronCore Labs CEO Patrick Walsh and privacy lawyer Scott Giordano talk about cybersecurity risks to AI systems and the regulatory responses.

Videos
Encrypting Vector Databases: How and Why Embeddings Need to be Protected with Colt and Patrick
Not sure how to protect sensitive data in a vector database? Colt and Patrick discuss why and how you can encrypt data you store in a vector database while maintaining usability.

Videos
Facial Recognition Risks with Murph and Craig
Hacking facial recognition embeddings is surprisingly easy. Craig and Murph discuss the process of attacking facial embeddings, the results (which are very accurate), and the implications of facial recognition attacks.

Videos
Retrieval-Augmented Generation (RAG) Architecture Security Risks with Patrick and Bob
Patrick and Bob discuss retrieval-augmented generation (RAG), its purpose, how it works, and its potential security and privacy issues, particularly with vector databases.
Newsletters
Unmasking Facial Recognition Security Threats
We expose some risks of data leakage that your facial recognition systems likely are being exposed to right now.

Blogs
There and Back Again: An Embedding Attack Journey
Reversing text embeddings is so easy, even your grandmother can do it. Encrypt them to avoid leaking all your sensitive data to the internet.

Blogs
The Hidden Dangers of Face Embeddings: Unmasking the Privacy Risks
Is your facial recognition system leaking faces like a sieve? Yup. Can you stop it? Yes.

Blogs
7 Predictions for 2024
The hype machine is in full swing, but our predictions ignore the baloney and focus on what's likely.
Newsletters
Happy Holidays
We take a look at how our year is wrapping up, capped by the release of Cloaked AI

Videos
IOPD: Vector Databases: AI Uses, Privacy Risks, and Mitigations | Privacy Engineering & Technology Education Discussion (PETed) Recording
This was a Q&A with Institute of Ooperational Privacy Design members on the dangers of shadow data flowing into vector databases. The intro and conclusion were recorded, but the Q&A was not to preserve privacy of the members.

Videos
Cloaked AI Demo: Part 1
This is a demo of Cloaked AI, the first and only encryption solution that gives you the power to protect sensitive data in your vector database of choice. This demo includes a walkthrough of code showing how to change a standard AI app into an encrypted one with deep explainers on embedding inversions and how vector encryption works.
Newsletters
Unlock gen AI potential with data protection from Cloaked AI
Announcing the launch of a product that helps you protect data stored in AI systems
Press Releases
Introducing Cloaked AI: The IronCore Labs encryption SDK for protecting AI embeddings in vector databases
Privacy and security concerns are some of the top reasons AI projects fail to launch, which is why companies are turning to Cloaked AI to protect sensitive AI data

Blogs
Forbes: AI Systems And Vector Databases Are Generating New Privacy Risks
With the right policies, questions and tools, organizations can take advantage of the transformative power of generative AI while also protecting sensitive customer data.
Newsletters
Privacy Risks in Your AI Tech Stack
We take a look at some of the places where your AI systems might be vulnerable
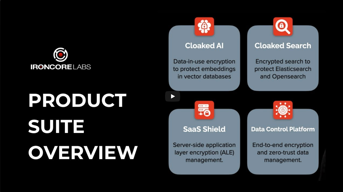
Videos
IronCore Labs Product Overview
Whether it's a cloud application, vector database, or a search service, protecting sensitive data is crucial. At IronCore Labs, we make it easy for you to build security into the core of your applications or wherever your data lives with encryption-in-use solutions.

Videos
OpenSearchCon Presentation on Securing AI Data
At OpenSearchCon 2023 in Seattle, Bob Wall gave a presentation titled "How to Secure AI Data Stored in an OpenSearch Vector Database". This is a link to OpenSearch's video recording of the talk.

Videos
ISSA: How to address privacy needs across the AI tech stack
This is a recording of an ISSA webinar where IronCore Labs CEO Patrick Walsh walks through the AI tech stack from a privacy and security perspective followed by a Q&A with privacy lawyer and moderator Scott Giordano.
Newsletters
Harmful AI Myths and Misconceptions
We debunk some misconceptions about the security and privacy weaknesses of embeddings produced by an AI model

Blogs
"Embeddings Aren't Human Readable" And Other Nonsense
The research and breakthroughs in embedding inversion attacks make it clear that embeddings are, in fact, reversible back into forms that are fully human readable.

Videos
How to protect sensitive data in generative AI systems
In this webinar, you’ll learn about modern AI systems and how to secure them, as well as an introduction to the role of vector embeddings and how to protect embeddings with encryption-in-use. Companies building AI systems on private data need to know how to keep the data safe without inhibiting the usefulness of new AI products

Videos
Post-quantum cryptography explained
Will quantum computers break cryptography? And what will happen once they do (yes, we see it coming)? In this talk, Patrick Walsh starts from the ground up and explains how developments in quantum computing are impacting cryptography standards and how we build software. He also discusses how the market is preparing and predicts how it will respond once the inevitable happens.

Videos
Software Resiliency in the Age of AI
In 8 minutes, you will feel the frustration of the nine T-mobile data breaches, the double-edged impact of data privacy regulations, and be introduced to the next wave of data security: protecting AI data. Find out how incentives are changing to pressure organizations and software developers to build more resilient software, especially as AI becomes a bigger part of the equation.

Videos
The Landscape of AI Security
AI has a security and privacy problem. What are people doing about it and which companies have created products that address each threat? In this video, we break down the landscape of products that protect AI systems, put them into a few buckets, and give examples of companies that are doing each of these things. Hopefully, this will help you understand what you should be thinking about as you build out production-ready AI systems that operate on private data.
Newsletters
AI Systems Have a Data Security Problem
We announce a new product to help secure sensitive data stored as embeddings produced by your AI model.

Press Releases
IronCore Labs launches beta for encrypting AI data
In response to mounting risks facing software companies with AI solutions, IronCore Labs announced a beta signup today for a first-of-its-kind product called Cloaked AI, which protects sensitive data stored in vector databases with encryption you won’t even notice, unless you’re a hacker.

Explainers
Security of AI embeddings explainer
Vector embeddings produced by machine learning tasks are a prime target for data theft. They're the memory of AI and just as sensitive as the data they derive from. Encrypting the sensitive data you store in vector databases is critical to protecting your company's sensitive data and reputation.

Blogs
Waitlist Now Open for New Encrypted AI Vector Embeddings Solution
Protecting the long term memory of AI is paramount as advanced capabilities become the norm.

Videos
What are AI vector embeddings?
An overview of the vector embeddings produced by machine learning tasks, sometimes called the "memory of AI".

Blogs
Rethinking the broken complexity of cloud security
Modern infrastructure requires a modern approach to security by protecting what matters most: the data.
Newsletters
Rethink Cloud Security
Complexity doesn't make things more secure! Think twice before piling on more and more security products.
Newsletters
New Data Sovereignty Product Feature
We have added a tagging feature to SaaS Shield to help you manage where encrypted keys are distributed.

Blogs
A Security Expert's Data Privacy Checklist
As a security professional, the top question I get is, "what do you do to protect your own privacy?" Here's what I recommend, along with a checklist at the end.

Blogs
Top 3 Ways to Justify Encryption to the Business
How to explain the importance of data privacy and data security before introducing encryption in a conversation.
Newsletters
Why Encryption Even Matters
We offer three ways to justify encryption to the business.
Newsletters
Six Cybersecurity Predictions for the New Year
Where is cybersecurity headed in 2023?

Blogs
6 Predictions for Cybersecurity in 2023
The hype machine is in full swing, but our predictions ignore the boloney and focus on what's likely.

Videos
The Market for PETs
A tour of privacy enhancing technologies and a setup of where they fit into the picture of privacy and security and how individuals can or can't use them.

Blogs
Product Showcase: Searchable Encryption in Elasticsearch and OpenSearch
Help Net Security spotlights Cloaked Search and what security personnel need to know.

Blogs
Meta Amasses $1B In GDPR Fines and Still Undeterred... For Now
Meta has had a bad year with privacy violations and sloppy data security coming home to roost. How bad is it? Really bad.
Newsletters
NEW Features: Encrypted Data is Now Easier to Search On 🔍
Cloaked Search gets more powerful with new features and improved performance.

Press Releases
IronCore Labs Launches Advanced Searchable Encryption Features
Today IronCore Labs announced the release of its next generation of Cloaked Search, the encrypted search proxy that secures data in Elasticsearch and OpenSearch.

Blogs
OpenSearch Partner Highlight: Using Cloaked Search to Protect Your Data
The data in your OpenSearch indices can be a big security hole. IronCore's Cloaked Search can plug that hole without shutting down search on the data.

Blogs
Forbes: How To Be Crypto-Agile Before Quantum Computing Upends The World
Change is coming to cryptography and some of that change will be extremely disruptive to the Internet and companies building software. Here's how to be ready.

Press Releases
IronCore Labs Mentioned in Gartner® Report on Preparing for the Quantum World With Crypto-Agility
IronCore Labs announced today that Gartner® has identified the company as one of the vendors in the public key infrastructure (PKI) and cryptography space in the 2022 report "Preparing for the Quantum World With Crypto-Agility."
Newsletters
Why Transform Encryption Is Better
Encrypt to groups with policy-driven encryption that works end-to-end.

Blogs
How To Neutralize Toxic Data In Custom Fields
Custom fields are a mainstay in B2B software, but they are often abused by customers who store sensitive data in them. Encrypting these fields reduces risk from privacy and security failures.

Explainers
Crypto-agility / post quantum cryptography explainer
Crypto-agility is the best way to prepare for quantum computers and post-quantum cryptography
Newsletters
Encrypt Your Toxic Data
Neutralizing toxic data in custom fields protects you and allows your customers to do more with your product.

Blogs
Key Management R Hard
Providing advanced encryption to all your customers is a win-win.
Newsletters
The U.S. Is Living Through A Digital Privacy Catastrophe
The U.S. lags behind the world, and we need a nationwide privacy law now more than ever.

Blogs
Forbes: We're Living Through A Digital Privacy Catastrophe: It’s Past Time For A Serious Nationwide Privacy Law
Companies can do almost anything they want with our digital data, including selling it to the U.S. government.
Newsletters
How to Future-Proof Your Encryption
Learn how to be crypto-agile so you can build cryptographic resiliency in the age of quantum computers.

Blogs
How To Be Crypto-agile: Building Cryptographic Resiliency In The Age Of Quantum Computers
Crypto-agility is an approach that allows you to pivot quickly when post-quantum computing becomes a reality.

Videos
Encrypted Search and Blind Indices Explained
Bob and Patrick talk about encrypted search and how it's different from what most people think of as encrypted data in a search system.
Newsletters
The Rise of Encryption Around the World
Learn about two technical measures that satisfy Schrems II with encryption.

Videos
Privacy Regulations, GDPR, and Schrems II
Patrick and Riah talk about modern global privacy laws and the challenges of handling personally identifiable information (PII).

Videos
Constant Time Crypto Explained
Colt and Patrick talk about constant time code, what it is, and why it's important in cryptography.

Videos
Why Use Application-layer Encryption (ALE)
Patrick and Wendy talk about application-layer encryption (ALE), what it is, and why it's important.

Videos
End-to-end Encryption and Private Key Rotation
Bob and Craig talk about how IronCore solves problems like needing to encrypt to users who haven't yet set up their keys and how to rotate private keys.

Videos
Proxy Re-encryption Explained
Bob and Colt talk about what Proxy Re-encryption is and some of the benefits and applications of the technology.

Videos
IronCore Labs' Founders Interview
Bob and Patrick talked about why they started IronCore Labs and what makes it meaningful.

Blogs
Forbes: The Rise Of Encryption In A Schrems II World
Companies can do almost anything they want with our digital data, including selling it to the U.S. government.
Newsletters
Are You Ready For Schrems III?
These technical measures allow U.S. companies to comply now instead of waiting for the next framework to be dismantled

Blogs
What You Need To Know About The New Trans-Atlantic Data Privacy Framework
How U.S. companies should think about this new proposed replacement for the EU-U.S. Privacy Shield Framework.

Blogs
The Trouble With FIPS: Encryption Standards Need a Makeover
FIPS 140 sets the standard for cryptography used in the United States, but it's got problems. Because of FIPS, we all have problems.

Blogs
Announcing Our Startup Program
Why It’s Important for Startups to Build Right From the Beginning
Press Releases
Startups Get Two Years Free Access To Encryption Tools With New IronCore Labs Startup Program
The IronCore Labs Startup Program Offers Free Multi-tenant Encryption to Qualified Startups For Two Years
Newsletters
Startups Get Two Years Free
The new IronCore Labs Startup Program helps startups address data security challenges early on.
Videos
Cloaked Search Getting Started Walkthrough | How To Search Over Encrypted Data
Patrick walks through the "Try Me" repo steps to show you how to locally install and use Cloaked Search to encrypt data flowing to Elasticsearch and OpenSearch.
Newsletters
6 Trends I'm Predicting For 2022
Here's what's trending and what's overly hyped up, plus why encryption at rest is crap.

Videos
Encryption At Rest Is Crap
The bottom line is this: encryption at rest doesn't tell you if the data is protected.

Blogs
A Contrarian's 2022 Tech Predictions
Once again, we'll see a huge rift between the hype and what the press covers versus where the real momentum is building.
Newsletters
AppSec Best Practices For 2022
Security vulnerabilities are a given and can exist for more than 10 years before they're discovered. Here are AppSec best practices.

Blogs
AppSec Fails and the Incredible Durability of Application Vulnerabilities
As companies mature, they often look to increase their application security. But more often than not, they ignore one critical piece.
Newsletters
Infographic: How To Get Started With ALE
Step-by-step guide on getting started with application-layer encryption.

Videos
How to Secure Your Sensitive Data in Elasticsearch and OpenSearch
Learn why and how to use encrypted search to protect sensitive data stored in Elasticsearch or OpenSearch. Watch the webinar replay.

Blogs
Infographic: How to Get Started With Application-layer Encryption
Application-layer encryption (ALE) is the best way to keep the data you hold safe, but there are a lot of pitfalls to doing it yourself from scratch, which is why few companies have historically used ALE. Thankfully, that's changing as it becomes more accessible.

Press Releases
Companies Can Now Search Encrypted Data With IronCore Labs' New Cloaked Search Product
IronCore Labs announced today the launch of Cloaked Search, a drop-in encrypted search solution to protect sensitive data held in existing search services, and a partnership with OpenSearch, a community-driven, open-source search service.

Blogs
Solving Search Over Encrypted Data
Encrypting data turns it "dark", but data is most useful when you can find it. And that's where encrypted search comes in.

Blogs
An Open Letter to Apple: Please, Please Replace Objective-C with Rust
Your iOS 15.1 update fixes 22 vulnerabilities. Thank you. But here’s the thing: of those twenty-two, at least sixteen of them were due to memory bugs.
Newsletters
How to Secure Sensitive Data in Elasticsearch and OpenSearch
Let's talk application-layer encryption and encrypted search.

Blogs
A Checklist to Quickly Evaluate SaaS Security
You don't need extensive infosec reviews to gauge the relative maturity of a SaaS company's security. You just need their website.

Blogs
Application-Layer Encryption Defined
It's a simple concept made complicated by security vendors. We dispel the fog of B.S. in this mini-blog.
Newsletters
What You Need to Know About SaaS Security Layers
Most SaaS solutions aren't properly layered to protect sensitive data from even the most common attacks.

Blogs
The Lack of Security Layers in SaaS
SaaS apps are systemically under-protected with laughably few layers to prevent a catastrophic breach.

Blogs
An Unpopular Opinion: Apple's CSAM Detection Is A Net Good
I don't agree with the "slippery slope" and "backdoor" arguments
Videos
SaaS Shield Configuration Management Demo
A walk-through of the SaaS vendor and SaaS customer experience setting up customer managed keys.

Blogs
How the Cyber Insurance Industry Can Stop Ransomware
Cyber Insurers can help the tech industry level-up their security. If they want to.
Newsletters
Encrypted Search & Critiquing Cyber Insurance
Learn about Cloaked Search and find out why the insurance industry should be doing more to stop ransomware.
Newsletters
Compelled Access Complicated Privacy
Government requests to Amazon for customer data rose by 472% in 2020.
Explainers
Application-layer encryption explainer
Application-layer encryption is the best way to protect data from hackers that get past your firewall or find a vulnerability in your application.
Newsletters
Your App Needs Better Encryption
Government requests to Amazon for customer data rose by 472% in 2020.

Blogs
Why Your SaaS App Needs Better Encryption
You can't afford to have customer data leak
Newsletters
Sensitive Data Will Bite You In The Ass
Do you know how much it costs per GB of data when your data is breached?
Newsletters
The Cost of Data in 2021
Have you considered the economic impact of holding data?

Blogs
Evaluating Newly Proposed Privacy Regulations
New privacy laws are popping up like mushrooms here in the U.S., which we love to see. But it can be hard to tell whether these proposed laws are meaningful or not.

Blogs
SaaS Security: How To Handle Sensitive Data
Why SaaS Companies Should Offer Customer Managed Keys

Podcasts
Lies You've Been Sold About Encryption
Jonathan and Mike welcome Patrick Walsh, CEO of IronCore Labs, to discuss transparent data encryption, data access and privacy, security in-depth, and how companies today are facing these challenges.

Blogs
The New Economics of Holding Personal Data in 2021
Hidden penalties buried in CCPA will radically change the cost of the next big data breach.
Press Releases
IronCore Launches Customer Managed Keys for Amazon S3 in AWS Marketplace
B2B SaaS Businesses Can Now Protect Files in Amazon S3 With Customer Managed Keys (CMK) from IronCore Labs.
Newsletters
Free Trial: CMK in AWS Marketplace
Get a free trial of our new CMK product now available in AWS Marketplace.

Blogs
What Ring Got Wrong With End-to-End Encryption
We'll dig into what they did, from usability through to the cryptographic choices they made.

Podcasts
IronCore's Call To Arms
Hosts Alex and Robb discuss CEO Patrick Walsh's recent Colorado Sun op-ed calling for our politicians to fix our nation's cybersecurity infrastructure.

Videos
ISSA Webinar: Pseudonymization vs. Encryption: Fight!
The user data you hold is now toxic -- meaning the penalties for losing control of that data are now potentially very costly. Technical measures must be taken to protect the privacy of that user data, which means you probably need to adopt a PET. But what PET is appropriate?

Press Releases
OPINION: Huge Cyberattack Shows It's Time To Fix Our Failing Cybersecurity Infrastructure
This op-ed originally ran in the Colorado Sun and advocates for a better approach to our nation's critical cybersecurity infrastructure.

Blogs
Opinion: Huge cyberattack shows it's time to fix our failing cybersecurity infrastructure
We live in an age of asymmetric cyber warfare where even small teams of attackers have an advantage over large and well-funded defenders.
Newsletters
Infographic: The CMK Industry Guide
Many variations of CMK exist within the industry, so we built an infographic comparing some of these approaches.

Blogs
Infographic: The Customer Managed Keys Buyer's Guide
More and more enterprises are offering customer managed keys (CMK), but not all CMK are created equal. This infographic compares CMK available from different companies.
Newsletters
Do you have a 2021 Privacy Strategy?
Full trust is not only losing popularity, it's also costing companies millions in data breaches and fines.

Videos
SaaS Shield CMK for Amazon S3 - Demo Video
Watch a demo of SaaS Shield Customer Managed Keys for Amazon S3.

Blogs
Privacy Was On The Ballot
The voters have spoken and they want laws protecting their privacy. Four states made progress this cycle.

Explainers
Technical measures for GDPR and Schrems II explainer
Encryption offers a peace-of-mind solution in a time when data privacy laws like GDPR are evolving and international transfers are being challenged as with Schrems II.
Newsletters
What Is Strategic Privacy?
A host of companies have recently been investing in privacy and leading their sectors with strategic privacy.
Newsletters
End-to-end Encryption Deep Dive
Get our latest eGuide on E2EE for video conferencing platforms and learn more about a new product releasing soon.

Explainers
The End-to-End Encryption Guide for Video Conferencing Platforms
An in-depth, technical look at how to make E2EE a reality for your video conferencing platform.

Videos
What Zoom Got Wrong With End-to-end Encryption
Find out what E2EE is and what it is not as we discuss the Zoom case study.

Blogs
Free Tool for Startups Getting SOC 2 Certified
IronCore Labs' team developed a SOC 2 internal dashboard tool that's available for public use.
Newsletters
Let's Talk About Zoom
What did Zoom get wrong with end-to-end encryption? A lot.

Videos
Choosing Rust - a Presentation by Clint Frederickson
Clint introduces some of the differentiating factors of Rust with a focus on the language's revolutionary "data ownership" concept.

Blogs
How to Handle EU Data Without the EU-US Privacy Shield Framework
Three Technical Approaches to Handling EU Data Without Privacy Shield
Newsletters
Twitter Has an Insider Threat Problem
Software companies need to rethink everything about employee access.

Blogs
The Cloud Needs More Sunshine
Twitter is just the most recent reminder of how broken the cloud remains

Videos
Why SaaS Businesses Are Turning to Customer Managed Keys
CMK is a privacy feature that gives customers control of their encryption keys.
Newsletters
Announcing Encrypted Search & New Platforms
How our products address modern privacy challenges and the CMK webinar.

Press Releases
IronCore Labs Announces New Data Privacy Product Features
Businesses with sensitive customer data look to IronCore Labs to empower application developers with SDKs for easy-to-implement encryption and customer-managed keys.

Blogs
New Ways to Address Modern Privacy Challenges
An IronCore Labs Product Update

Blogs
Rally Software Leads the Industry in Data Privacy With Customer Managed Keys
Customers want data control, and with IronCore Labs, that's what Rally offers

Blogs
Deidentifying Data: The Fool's Trap
Re-identification is trivial by joining other data sets

Blogs
SaaS Trust Models for Security and Data Privacy
You can't compare the privacy of SaaS offerings until you understand their trust model.

Blogs
Insights From Slack and Salesforce: Grow Your SaaS With Premium Data Privacy
Early adopters of premium data privacy are doing well. Here's one reason why.

Videos
SnowFROC 2020 - Rethinking the Enterprise Perimeter
The function of security tends to rest in IT and this drives a network-centric view of security. Partners' security is evaluated based on their perimeter controls and perimeter controlling technologies like IDS, firewall, and DLP, are the heart of data protection strategy today, but these strategies don't work in a world where data is everywhere, shared with many partners, scattered amongst vendors, and with development teams constantly building new things that access the data. But new tools are available for a zero-trust data world including BYOK, modern cryptographic access control, privacy and security by design application stacks, and more. This talk is a survey of the next generation of Enterprise security in complex environments.

Blogs
Warning: SaaS Privacy Debt Will Crush Your Roadmap
An open letter on why kicking the can down the road is catastrophic for the future of software
Videos
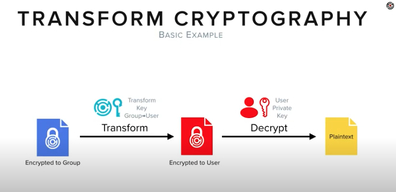
Transform Crypto Overview
An explainer breaking down Transform Cryptography and its relation to Proxy Re-encryption.

Blogs
How SaaS Companies Avoid Compelled Access With Encryption
A Look at Trust, Corporate Data, Government Prying, and Practical Defenses

Blogs
Welcome to the Revolving Door of Personal Data
Why Clearview AI even exists: U.S. government sells data to industry and then buys it back using a warrantless search loophole

Blogs
Highlights From Real World Crypto 2020
Things that made us go, "hmmmmmm"

Blogs
Agile Approaches to Privacy and Security for SaaS Vendors
Highlights From the Agile Amped Podcast With Rob Pinna and Leslie Morse

Podcasts
Baking Privacy and Security into the Technical Architecture
Rob is a 30-year high-tech veteran who is the Chief Product Officer at IronCore Labs. His passion is protecting the privacy of data stored in the cloud. Pinna says we shouldn't build software and then make it secure. Instead, you want to bake privacy and security into the technical platform. That way the system is designed so that developers automatically just do the right thing. The conversation covers how complex it is to both provide security and privacy early and often, as well as deliver at a large enterprise.

Explainers
Bring Your Own Keys (BYOK): An Overview
Bring Your Own Keys, or BYOK, is a cloud architecture that gives customers ownership of the encryption keys that protect some or all of their data stored in SaaS applications.

Podcasts
Colorado = Security Podcast Interview
Starting at around minute 22, an interview with IronCore CEO Patrick Walsh.

Blogs
IronHide: Better Team Encryption
A few months ago, we quietly released a little utility that brings the power of proxy re-encryption to the command line. Proxy…

Videos
IronHide Demo
How to use the `ironhide` command line tool to protect and share files.

Explainers
CMK: What Architects Need to Know
A white paper on Customer Managed Keys

Videos
IronCore Uses Coalfire for SOC2 Audit
Director of Operations Trevor Zylstra discusses IronCore's experience with Coalfire.

Blogs
Military Grade Encryption
And other security marketing bullshit

Blogs
CCPA: What You Need to Know
The California Consumer Privacy Act takes effect on January 1st, 2020. If you're a dev or work for a software company, this affects you.

Explainers
CCPA: What You Need To Know
A white paper on California's new data privacy law.

Press Releases
IronCore Is Now SOC 2 Certified
We have successfully completed the Service Organization Control audit known as SOC 2 Type 1.

Blogs
IronCore Is Now SOC 2 Certified
We are proud to announce that we have successfully completed the Service Organization Control audit known as SOC 2 Type 1. SOC 2 is a…

Explainers
Data Control White Paper
An introduction to the principles of data control, what it means, and how to use it.

Videos
ngAir 181
Policy-Based Client-Side Encryption in Angular with Robert Pinna

Blogs
Policy-Based Client-Side Encryption in Angular
And How To Fix It
Blogs
DoD's Distributed Data Problem
And How To Fix It

Press Releases
IronCore Labs Proxy Re-Encryption Library Audit by NCC Group
We hired a well-respected third-party with a stellar reputation, NCC Group, to review our implementation.
Blogs
IronCore Labs Proxy Re-Encryption Library Audit by NCC Group
We believe there's a right way to do things. With cryptography, that's even more important than almost any other area of software, save…

Videos
DEF CON 26: Implementing a Library for Pairing-based Transform Cryptography
IronCore CTO Bob Wall and Senior Engineer Colt Frederickson discuss the challenges of building open source proxy re-encryption tools at DEF CON 26.
Blogs
IronCore's Privacy Platform Helps Developers Unlock Enterprise Sales
Today, security and privacy scandals flood the news, and customers are demanding to know who can access their data, who that data is shared…

Press Releases
IronCore Announces Additional $1.5M in Seed Funding
IronCore is changing the way people and organizations think about data in the cloud.

Explainers
Cryptographically Enforced Orthogonal Access Control at Scale
ACM SCC '18 Proceedings of the 6th International Workshop on Security in Cloud Computing.
Videos
How IronCore Works
This video explains how IronCore works, and how it benefits your company. IronCore is a service that implements data control, privacy, and security into your application.

Blogs
Mastering Emotion in Marketing Copy
A tale of three books with an unexpected intersection

Blogs
How Not To Handle a Breach
Equifax Shows the Way

Blogs
Audit Your S3 Storage Immediately
A Quick and Dirty Guide

Videos
Stop Expecting Magic Fairy Dust: Be Secure By Design
Software developers are screwing up the digital world. Security is often an afterthought, or worse, the job of I.T., who is expected to sprinkle magic fairy dust on an app that magically makes it secure.

Blogs
The Proliferation of Under-protected OAuth Tokens
The Hidden Cost of Cloud Management Services and Integrations

Videos
Ironcore Labs Techstars Boulder 2017 Demo Day
Patrick Walsh, CEO of IronCore Labs, talks about the massive opportunity to help SaaS vendors kill on-prem competitors at the Techstars Boulder 2017 Demo Day event.

Press Releases
Announcing "Customer-Controlled Data"
A big step for Customer Managed Keys and a giant leap forward for cloud software.

Blogs
Announcing "Customer-Controlled Data"
A big step for Customer Managed Keys and a giant leap forward for cloud software

Blogs
How the 4th Amendment Is Bypassed
The U.S. Constitution doesn't pull any punches. The Government does not have the right to sift through the communications or property of…

Blogs
Baby Steps with NY's New Financial Cybersecurity Regs
Banks, insurance companies and other financial services companies in New York will soon be subject to new, stronger regulations around…

Blogs
Quantum is the New Global Arms Race
China Takes the Lead

Blogs
Bits, Banks and Burglars
What Happens When Digital Currency Is Stolen

Videos
The Internet is a dog-eat-dog world
IronCore CTO Bob Wall talking about security at Big Sky Dev Con 2016.
Blogs
The Worsening State of Application Security
At the Defcon conference last year, I was struck by the simplicity of most of the hacks that were being described. Five years ago, most of…

Blogs
The Inevitable Demise of Perimeter Security
Computer security today follows classic real-world military approaches: make a perimeter; fortify that perimeter; ensure that only…



























